Steemit Crypto Academy Contest / S12W6 - Privacy is important
 |
|---|
INTRODUCTION |
Data privacy always holds an important place in anyone's life, hence the internet space. Data privacy is why we lock our filing cabinets and use safety deposit boxes at banks. However, the internet makes data privacy problematic, as it's hard to keep track of all our posts and it's prone to digital thefts like hackers.
The blockchain technology world is not excluded, hence the continuous search for how to keep information private even in blockchain systems, bringing about different safety measures which include the zero-knowledge protocol. Our topic of discussion today.
What is the Zero-Knowledge Protocol (ZKP)? Give your own opinion and explain an example. |
|---|
Have you tried to tell your parents what your siblings did in their absence, without actually stating what they did? It is on this same ground the Zero-knowledge protocol applies.
Zero-knowledge Protocol or Zero-knowledge proof (ZKP), is a technique that allows a user, (the prover), to verify a statement or a piece of information to another (the verifier) without revealing the information itself.
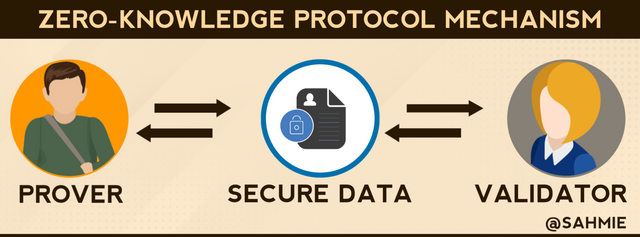 |
|---|
In the Zero-Knowledge Protocol, a user gets to prove the authenticity of a statement or information without disclosing any extra information beyond the validity and authenticity of the statement in other to protect their privacy and ensure security.
In the cryptocurrency field, the Zero-Knowledge Protocol promotes anonymous transactions while also ensuring the authenticity of the transaction. Hence, making blockchain system transactions more confidential and secure, while also protecting the users' identities and transaction details.
An example of how ZKP works is proving to someone that you know a secret without actually saying the secret. How is that even possible, maybe with eye contact or body language?
Let's say your sibling locks a door with a magical phrase, and you want your sibling to know that you know the secret phrase to open the door, without saying the secret phrase itself. Then, How do you prove you know the phrase? This is how ZKP works, proving to your sibling you know the exact phrase without saying it.
Primarily, there are two forms of Zero-Knowledge protocols Interactive ZK-proofs which require conversation between the prover and the verifier, and Non-interactive ZK-proofs which provide an agreement proof that can be verified in a single step. However, these forms are further divided into various types, which include;
ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge)
ZK-STARK (Zero-Knowledge Scalable Transparent Argument of Knowledge), and
Bulletproofs, (used to verify different types of statements)
What is the ZK-SNARKs protocol? Give your own opinion. |
|---|
ZK-SNARKs short for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge is a type of ZKP that permits a user (the prover) to prove to another user (the verifier) that a statement is accurate and authentic without disclosing any extra information beyond facts and authenticity of the statement itself.
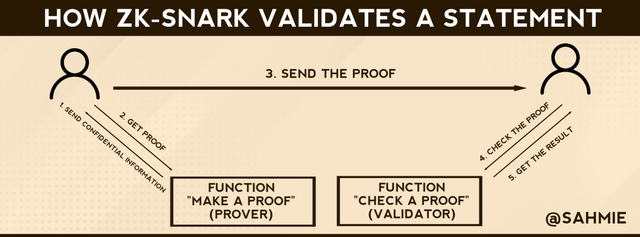 |
|---|
ZK-SNARKs use cryptography to prove that a specific analysis has been executed accurately, without disclosing any definite information about the actual input values or intermediate procedure about the analysis.
Examples of blockchain projects, that utilize ZK-SNARKs include Zcash, to provide privacy and anonymity for transactions while also retaining the integrity of the blockchain network.
With ZK-SNARKs, Zcash users can prove that they have sufficient funds to make a transaction without disclosing any tangible information of their actual balance or any other sensitive information, making Zcash transactions difficult to trace and providing users with greater privacy and security.
How does the ZK-SNARKs work and is it possible to adapt it to the Steem Blockchain? Give your own opinion. |
|---|
 |
|---|
As earlier stated, the purpose or use of ZK-SNARKs is to bring about privacy, anonymity, and security. An example of how ZK-SNARK works in blockchain is its application to Zcash where it is used to bring about the following;
Privacy and confidentiality
ZK-SNARK allows for confidential transactions, letting users conduct and execute transactions without disclosing key information, such as the transaction amount and sender and receiver addresses.
Verification and auditing
Without disclosing the real data or information, ZK-SNARK is used to check the precision of specific analyses or statements. Hence, guaranteeing data integrity and making effective auditing procedures possible.
Identity and authentication
ZK-SNARK ensures safe identity verification and authentication while protecting user privacy, thereby improving security on blockchain-based applications.
In conclusion, ZK-SNARK is used in the Zcash crypto project to validate a transaction, without disclosing any information about that transaction while also improving privacy, anonymity, and security. How is this achieve?
ZK-SNARK enables the sender to confirm that he/she has enough funds to carry out a transaction without disclosing their wallet balance or any other sensitive information. While also allowing the receiver to validate the transaction and that the sender had the necessary funds to carry out the transaction.
Other notable projects that use ZK-SNARKs include HOPR and Quorum, which use ZK-SNARKs to bring about private data exchange and to ensure privacy in transactions among its participants respectively.
Hence, ZK-SNARKs is a type of ZKP used in various blockchain networks to provide privacy, security, and anonymity and also maintain the integrity of the transactions.
It could be adopted in the Steem Blockchain, although Steem mainly employs a Delegated Proof-of-Stake (DPoS) consensus mechanism, which focuses on transparency, efficiency and speed. ZK-SNARK could be embraced to improve privacy on the platform.
However, implementing ZK-SNARK on the Steem blockchain can be resource-intensive and computationally intensive, leading to increased time in processing transactions and the use of resources involving more computational work, which might make the Steem blockchain less scalable.
The adoption of a ZK-proof can add a layer of sophistication or complexity to the Steem blockchain that might make the protocol more tricky to audit and verify, hence increasing concerns about potential security shortcomings or bugs.
Likewise, while ZK-proofs enhance privacy by concealing information, they may also promote unlawful actions in some cases, creating complications for regulatory compliance. ZK-SNARKs might also require appropriate require particular training and experience to implement properly.
Therefore, even as ZK-SNARK provides valuable privacy and security features, it is necessary to carefully study and evaluate the drawbacks before adopting ZK-SNARK into the Steem blockchain.
What is the difference between ZK-SNARKs and ZK-STARKs? Explain |
|---|
ZK-SNARKs as stated earlier stands for Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge whereas ZK-STARK stands for Zero-Knowledge Scalable Transparent Argument of Knowledge.
Both are ZKPs working under different systems to achieve the same objective, which is for a user to prove to another user that he/she knows a certain piece of information without revealing the piece of information itself.
But then, there are differences in the way these two protocols achieve this common goal. These differences include the following;
| FORM | ZK-SNARK | ZK-STARK |
|---|---|---|
| Level of Complexity | Requires a trusted setup, meaning that a group of people must develop a set of secret keys together. Hence, if compromised it is prone to attacks. | Does not need any trusted setup, making them better secured and immune to attack. |
| Level of Transparency | Is not transparent, hence, it is difficult for anyone to ascertain the proof without access to the secret key. | Is transparent, therefore anyone can ascertain the proof without access to any secret information. |
| Scalability | Less scalable as it is based on a tougher mathematical framework. | More scalable because it is based on a simpler mathematical framework. |
| Mathematical Framework | It is based on Elliptic Curve cryptography, which involves complex mathematical equations that are difficult to unravel. | It is based on a simpler mathematical framework called polynomial commitment schemes. |
| Implementation | Requires fewer resources, hence it is less challenging to implement. | Requires more computational resources, making it challenging to implement. |
Overall, while both ZK-SNARKs and ZK-STARKs are zero-knowledge proofs that can help to enhance privacy in blockchain systems, they vary in terms of the level of transparency, efficiency, scalability, and complexity.
What are the main privacy mechanisms used by the Steem Blockchain? |
|---|
The main privacy mechanisms of the STEEM blockchain are the Delegate Proof-of-Stake (DPoS) mechanism and the Graphene technology.
The STEEM blockchain, a social media-based blockchain platform, is designed to give its users complete privacy and control over their data and content. Thus, it provides privacy via the use of the Delegated Proof-of-Stake (DPoS) consensus mechanism.
DPoS gives users the ability to vote for delegates who will validate blocks while also maintaining the network. These elected delegates do not have access to the transactions or personal information of users beyond their transactions making it difficult for anyone to gain unauthorized access to transaction data or information.
Furthermore, the STEEM blockchain employs the services of Graphene, a technology that makes the blockchain protocols more scalable and efficient.
Graphene allows the STEEM blockchain to process a high volume of transactions and posts quickly, trusted to scale as high as 10,000 or more transactions in the space of a second without compromising the privacy and security of users.
STEEM blockchain's privacy mechanism also allows users to control their data and content by having full control over it. This provides the users with the ability to share their content with others on the platform or keep it private, and they can also take their data off the network and prevent others from accessing it.
CONCLUSION |
As the search for more security and privacy in the blockchain industry goes on, more innovations are created, bringing about Zero-knowledge proofs, which bring with them unique properties of privacy preservation and scaling potential. Zero-knowledge proofs are predicted to play a critical role in the creation of DApp ecosystems that are more protected, confidential, and efficient.
I wish to invite @anasuleidy, @ninapenda, @ruthjoe, @drhira and @suboohi
Thank You for your Time
NOTE: Always have a smile on your face, as you are never fully dressed without one.

Thank you, friend!


I'm @steem.history, who is steem witness.
Thank you for witnessvoting for me.
please click it!
(Go to https://steemit.com/~witnesses and type fbslo at the bottom of the page)
The weight is reduced because of the lack of Voting Power. If you vote for me as a witness, you can get my little vote.
Thank you friend @chant for finding me worthy of your support.
Excelente investigación amigo, casi no dejas nada que pueda comentar. Con relación a la adaptación del ZK-SNARK en la blockchain Steem considero que no sea muy compatible nada más con partir de que este protocolo elimina la transparencia al ocultar del ojo público sus movimientos por el afán de la privacidad. Creo que es un punto de debate para el equipo de expertos. Creo que Steem no necesita un protocolo de estas características.
Saludos y éxitos amigo.
Thank you for your wonderful comment, indeed I carried my research to the best of my know, and now I'm hoping to achieve a favorable outcome.
Hey my brother,
Hahaha Sam you are very funny, how did you know what I did when I was small. I am I from my siblings use such patterns to know when an intruder or a visitor is knocking the door. Our pass code then used to be Jack Robinson indeed this is such a lovely example.
Thanks for sharing such lovely post, please also engage on my post https://steemit.com/hive-108451/@starrchris/steemit-crypto-academy-contest-s12w6-privacy-is-important
I've always known you played a lot as a kid and this showed you did as it was evident to see from how you often smiled.
In this world of technology privacy is very important to all of us either we talk about our personal life and either we talk about our life related to technology everything should be private to some extent and that's why there are thousands of privacy mechanism that are being used by many persons in different things and from them zero knowledge protocol is very important thing. You have clear understanding about zero knowledge protocol.
You have implemented zero knowledge protocol with the help of an example in a good way as well as you have also illustrated in a proper way that what is your opinion about this privacy mechanism. You have explained up very clear difference between both these terms that are related to privacy and these are ZK-STARKs and ZK-SNARK.
Your efforts are highly appreciateable and good I wish you success in this engagement challenge.
Greeting dear friend you are very passionate in your knowledge and you always try to explain why well and I really appreciate you are good research in the given topic as you have very well explain about the importance of privacy and it's different impacts and also a very good knowledge about the zero knowledge and I have learnt from it.
wish you best of luck