Cryptography Lesson1 Challenge 1
Introduction
Caesar Cipher
Or more generally this tutorial will cover a substitution cipher and how it works. The Caesar Cipher is a very popular and basic encryption technique that is used to lure people into the idea of cryptography as 1: it is very easy to use and 2: it is eloquent. The general approach to the Caesar Cipher is to take a text, go through it character by character, and shift it by some number. For instance if we were to have a shift1 cipher (meaning we shift by 1 character) and our original text was "a" then we could have an output of "b".| Original | Billy bob loves his nuggets |
|---|---|
| Shift 0 | Billy bob loves his nuggets |
| Shift 1 | Cjmmz cpc mpwft ijt ovhhfut |
| Shift 2 | Dknna dqd nqxgu jku pwiigvu |
| Shift 3 | Eloob ere oryhv klv qxjjhwv |
| Shift 4 | Fmppc fsf psziw lmw rykkixw |
| Shift 5 | Gnqqd gtg qtajx mnx szlljyx |
| Shift 6 | Horre huh rubky noy tammkzy |
| Shift 7 | Ipssf ivi svclz opz ubnnlaz |
| Shift 8 | Jqttg jwj twdma pqa vcoomba |
| Shift 9 | Kruuh kxk uxenb qrb wdppncb |
| Shift 10 | Lsvvi lyl vyfoc rsc xeqqodc |
| Shift 11 | Mtwwj mzm wzgpd std yfrrped |
| Shift 12 | Nuxxk nan xahqe tue zgssqfe |
| Shift 13 | Ovyyl obo ybirf uvf ahttrgf |
| . | . |
| . | . |
| . | . |
| Shift 23 | Yfiiv yly ilsbp efp krddbqp |
| Shift 24 | Zgjjw zmz jmtcq fgq lseecrq |
| Shift 25 | Ahkkx ana knudr ghr mtffdsr |
What is a Substitution Cipher?
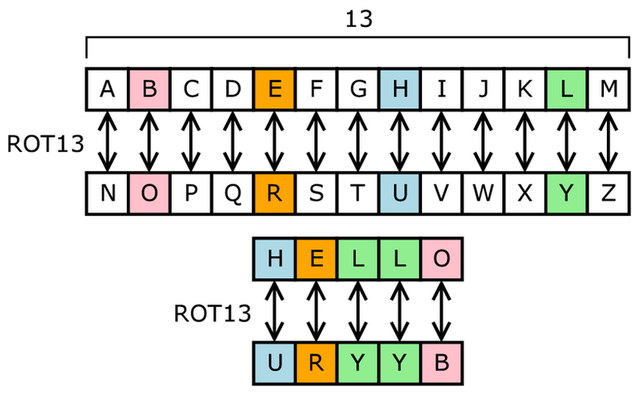
To put it quaintly, a substitution cipher is a cipher/encryption technique where you replace text or portions of text with something else and then you have the substitutions held as a key and only the sender and receiver should have the key and therefore be the only ones able to break it. On the right you will see a specific case of the Caesae Cipher (discussed above) named ROT13, or as we would put it Shift13. This is a special case because a Casar shift 13 can be undone by shifting another 13, with the English-Roman alphabet (For instance the Spanish-Roman alphabet has 27 letters and therefore has no shift that will undo itself as you cannot do a half shift, at least not using substitution methods.Problems With Substitution Ciphers
Sourced as Public Domain
Nby kocwe vliqh zir dogjyx ipyl nby futs mbyyj xia
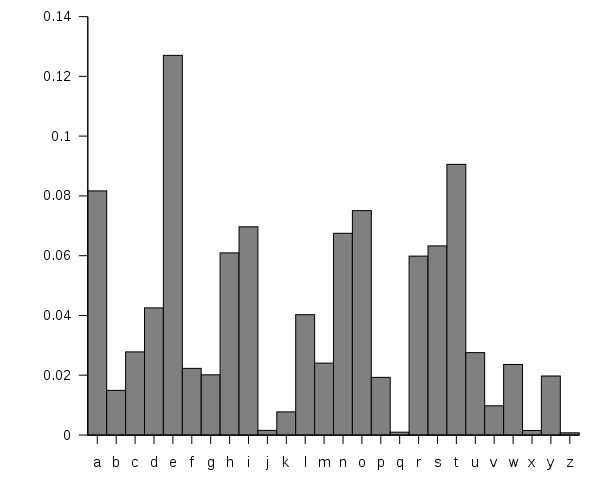
Using this we can quickly see that there are more y's than anything (10 y's to be specific, with a total of 77 putting its frequency at around 12.98%, right where expected for E's) and since we know that if we shift E by 20 we will get Y we can determine that if we shift by -20 (or 6) we should get the original phrase.
The quick brown fox jumped over the lazy sheep dog
How I got 6 as the Shift (ROT) number
Where:
N is the number of letters in the alphabet
Sn is the shift number of the original shift
S is the shift required to undo it
Lets use this with the above example, N=26,Sn=20, 26-20=6, ergo if we shift the previous encryption forward by 6 it will give us our answer.
References
Frequency Counter (0)
Caesar Calculator (1)
Caesar Cipher (2)
Substitution Cipher (3)
Letter Frequency (4)
Stinson, Douglas R. Cryptography: Theory and Practice. Third Edition, Chapman & Hall/CRC, 2006, www.icst.pku.edu.cn/F/course/Cryptography/CryptographyTheoryandpractice(3ed).pdf.
Practice Problems
2: Je ru eh dej je ru, Jxqj yi jxu gkuijyed 3: Kimaiz kqxpmz qa wvm wn bpm wtlmab svwev mvkzgxbqwv umbpwla. Qb qa dmzg aquxtm - qb qa rcab apqnbqvo iv itxpijmb. Bzivanwzuibqwv qa bmzuml ZWBV, epmzm V qa apqnb ditcm ivl ZWB qa nzwu "ZWBIBM" jmkicam bpqa qa i kgktqk apqnb.
4: Mpwf uiz fofnz
5: A world which does not belong
Find the specific encryption to these messages (ROT3 means shift by 3): 6 ROT3: The world will never be enough
7 ROT13: Love thy neighbor as thy would love thyself
8 ROT22: Don't you stick it in your mouth, though it might look good to eat, and it might look good to taste. You could get sick, real ick, real sick, real quick.
9 ROT2: Why do sports fans always question why youtube gaming is popular? You guys just sit there watching others play games for entertainment too!
Answers:
1: ROT13(Shift13) If money is the root of all evil then why do they ask for it at chur
ch
3: ROT18 Caesar cipher is one of the oldest known encryption methods. It is very simple - it is just shifting an alphabet. Transformation is termed ROTN, where N is shift value and ROT is from "ROTATE" because this is a cyclic shift.
5: ROT0 (Shift0) A world which does not belong
7: Ybir gul arvtuobe nf gul jbhyq ybir gulfrys
9: Yja fq urqtvu hcpu cnycau swguvkqp yja aqwvwdg icokpi ku rqrwnct? Aqw iwau lwuv ukv vjgtg ycvejkpi qvjgtu rnca icogu hqt gpvgtvckpogpv vqq!
Find the original text: Hmh vjg usl moo ez sgd cow
To enter your answer (and be eligable) go to https://8gwifi.org/rsafunctions.jsp and enter in the public key below (delete the private key) and enter your answer into the clear text message. Make sure to have the encrypt message clicked. Then comment the output on this post.
Public key:
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCkNHuHqbtW76jzoCXEFaIyNG3+
+t5tUCUugNYn0qTsr0ItVTf3O0g3z/GOgeQJ0trHQSMZ8IcDsz5jMrvMOv1glcvk
XN0D9ke20/YqZ7MOa9lz3oRTHpRaVQlGJlBCrdVq13+UrJKpPR7FYI6Yc/de8i2o
PDtxxq6AXSp0zUtEewIDAQAB
-----END PUBLIC KEY-----
Example comment:
Here is my answer:
IS8G23WLHabrXBn7nL52GVEH9VIq7yXtzhtAWk+d8DGBOw8RY9y+murcsInWoRb7bQ/L1HULb9vAsdCc58EKBAFpxQrB4ju/gt+Tlw+pNl+U9xG7S5ujnROd+X/AwrLzQvWO5ik52jjzkpEC4z5Mc9I8OWLirRxWcMKCZ3Qy4jE=
The prize goes to the first person whom responds with the correct answer but the prize will be handed out no sooner than payout. If no correct answer has been handed in by payout then I will keep the prize for myself. There will be a bonus for second and third place people!

This was a little confusing to read at times but I will bite on and try.
Answer:
Now for some suggestions, its a little confusing that you introduce caesar cipher before you introduce what a substitution cipher is and may be better to reverse the two. Another thing, when coming down to the problem, is it was almost difficult to dissociate the problem from other text, your formatting is pretty good but with how you keep it like that its almost... It could be better.
Welcome to Steemit though!
As I said in my introduction is I don't like blogging/writing. Thanks for the tips though and thanks for the welcome!
I don't see how I can easily change the position of the caesar cipher part to be after the substitution part... But I did do something that should hopefully make the challenge easier for others
I was meaning more for next time. Post isn't bad by the way!
Thanks!
Well good work