Mona -UPL compress diagram
Hello to all!
take a look-->
Some concepts may differ from current standards.
Concept of invoke (decompress)
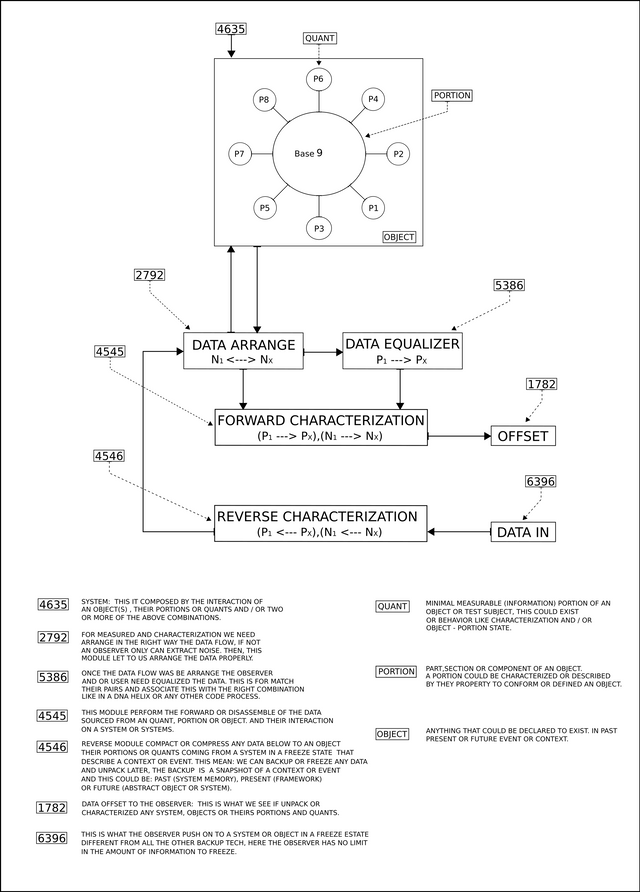
Given the nature of the method used, we cannot say or affirm that we are decompressing data. This is because the resulting data is derived from a fractal or mathematical arrangement. Actually what happens is that the initial data was arranged (organized) and equalized for later apply a dynamic correlation formula. [see diagram 4635]
As mentioned earlier and given that in said (characterization) process we use vectors or temporary indicators (Vcore, CPU Speed, RTC, etc.) even when the data structure is the same and two or more compression processes are performed in parallel in the same device the (key) or engine to decompress said arrangement or fractal will differ from one another.
This is because by incorporating in the process the previous parameters any software or device that interacts with the host that hosts the encryption and compression engine will end up altering said parameters and the result of their computation will be proportional to said interaction. The above applies in the case of a foreign or malicious device, even if it has more processing power than the host, the resulting data will differ from the original data or key. For malicious processes running on the host, they face the paradox that theoretically should run faster than the maximum processor speed of the host itself. Which is impossible even when our app is running in a virtual environment, this is because our reference values are hardware base.
Based on the above, we can conclude that each engine or key generated corresponds and only produces consistent and valid data for its respective fractal or mathematical arrangement. This is very useful since it gives us the convenience of having large volumes of information in a very small space as well as data security and integrity.
So, when (invoking) a data, what we are actually doing is obtaining it from a single equation. This is very useful for downloading or sending large volumes of information such as multimedia content (streaming) or to unpack and run applications or operating systems remotely.
For such cases it is enough to (invoke) on the remote host said key and its respective fractal. The latter is relatively easy since all of the computing devices perform logical operations and these are mostly translated into Hexadecimal format. Same that we use for our computing process, same that I have published in a writing entitled:
(Storage data in the blockchain network) @
https://steemit.com/@azazel0101
http://io-exchange.com
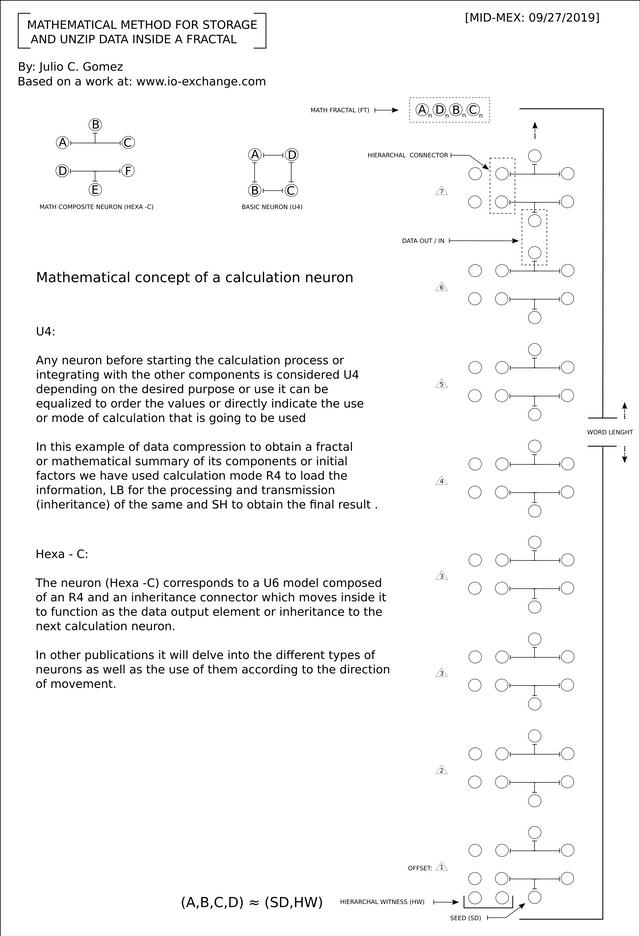
The first step of our model is to convert the entirety of a binary or plain text to Hexadecimal and then translate (assign) numerical values to each of the 16 elements that make up the Hexadecimal.
It is called extemporaneous since the data to be calculated comes from a future position (unknown) and therefore any attempt outside the main body of our program generates variation in the final result. In this equation we incorporate a Wachtdog module to guarantee and prevent possible debugging of processes, regardless of whether they are performed in a virtual environment or are associated with our hardware or external device.
[See extemporaneous formula]
(Proc) Level:
As you will understand when attaching and relating different neurons, these behave like logic gates, which are defined in the main body of the program. The (proc) level is our program structure, which is not externally accessible since, unlike the compression method in which only one key is generated. At this level we generate two, one is used by the program itself to index and expand its data (very interesting for autonomous AI) and the other is retained by the programmer or owner. Once the program is sealed and in operation, in order to correct or modify its structure, both keys are required. This is because these neurons are declared in perpetual state [PPT]. This is analogous to the chaining model currently used in encryption applications. Therefore, the program itself avoids being modified externally since in order to carry out this process the program structure must be (broken) and this mean to stop it (conservation theory).
In future publications it will be delving into this concept and other details as well as the different functions thereof (operands, mnemonics, pseudomnemonics, syntax, etc).
Azazel0101
Based on a work at:
http://io-exchange.com