The Ethics Of Cryptojacking: Rampant Malware Or Ad-Free Internet?

The Ethics Of Cryptojacking: Rampant Malware Or Ad-Free Internet?
Cryptojacking, the practice of using a computer’s processing power to mine for cryptocurrencies without the owner’s permission or knowledge, has recently gained more traction in the crypto sphere as browser-based crypto mining has once again become possible and profitable.
As Bitcoin (BTC) became more and more popular worldwide since its inception in 2009, it became harder and harder to mine for cryptocurrencies on a personal computer, given the increasingly high amount of energy needed to make a profit. More efficient mining hardware like ASIC chips slowly became the norm, ending the era when one person sitting at home with a PC could make money mining Bitcoin.
However, with the introduction of altcoins like Monero, first released in 2014, which are naturally resistant to ASIC mining — due to the large amount of storage they require that ASIC cards cannot provide — the figure of the lone crypto miner has returned via browser-based mining.
Browser-based cryptojacking, however, is not necessarily accomplished by a single hacker taking over your computer to use its processing power to mine crypto. Today there are entire dedicated businesses and services that allow cryptojacking to take place on a mass, global scale.
Coinhive – the crypto miner of choice
A recently published academic study from Concordia University on the history of cryptojacking found that the JavaScript browser mining program Coinhive is currently the most commonly used script for Monero mining, and thus cryptojacking in general.
Coinhive works by providing an Application Programming Interface (API) to developers, which then lets the developer use a website visitors’ CPU resources to mine Monero. Coinhive markets itself to web-based companies as a replacement for online ads, proclaiming unabashedly on their website’s main page: “Monetize Your Business With Your Users' CPU Power”.
This “rejuvenation of browser-based mining,” has taken many forms, from cryptojacking attempts by malicious players to relatively benign cable companies trying to use it as an alternative form of monetization, instead of showing users online ads.
Malicious cryptojacking cases
Cryptojacking malware has been placed on a variety of websites around the world — as Cointelegraph reported in late January, more than 55 percent of businesses worldwide have been affected by the practice.
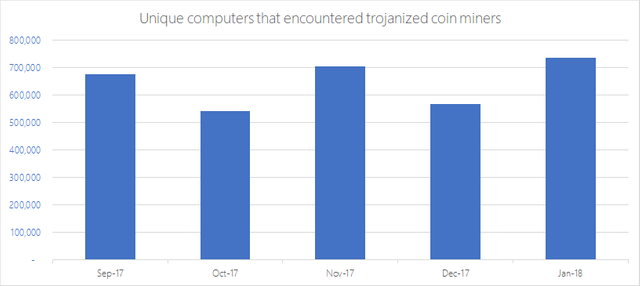
According to a Microsoft blog post from March 13, an average of 644,000 computers were infected with crypto mining malware from the period of September 2017 to January 2018. The blog notes that cryptojacking can come in many forms, like video streaming sites constructed with the only goal being cryptojacking, or tech support scam websites that are actually crypto miners.
It was discovered in January 2018 that Youtube had been the target of cryptojacking attacks, when anonymous hackers placed cryptojacking scripts into ads that played on the platform. According to reports on the cryptojacking hack, Youtube users in Japan, France, Taiwan, Italy, and Spain were the most affected.
More recently, Tesla’s Amazon Web Service software container was cryptojacked due to a lack of password protection. A similar case of cryptojacking took place in October 2017 at the Amazon Web Services of the companies Aviva and Gemalto.
Earlier this month, Microsoft reported that it had blocked more than 400,000 cryptojacking attempts in a span of 12 hours. The attackers used the NiceHash crypto cloud mining marketplace, which supports a variety of currencies, although the Microsoft report found that the attempts were to mine for altcoin Electroneum.
On a larger scale, a study published by the University of Toronto in March found that Telecom Egypt, a government entity, has been linked to using middleboxes to surreptitiously direct Egyptian Internet users to cryptocurrency mining sites, specifically mentioning the service Coinhive.
Can cryptojacking be non-malicious?
The Coinhive mining script has shown up in several cryptojacking incidents that were arguably not as malicious as those detailed above.
In September of last year, it was discovered that the illegal piracy site, The Pirate Bay, was secretly mining for Monero on visitors’ computers without their knowledge. When the news broke, The Pirate Bay defended itself by asking users if they would rather see ads on the site or have their computers be used to mine crypto on the company’s behalf. The majority of respondents voted for mining.
A little more than a week later, major American cable television network Showtime was also found to be secretly running Coinhive to mine Monero using visitors’ computers. Showtime also explained that it used Coinhive as an alternative revenue source, instead of showing ads to users.
In response to several exposed incidents in which Coinhive was being used by a site without its visitors’ knowledge, the mining script company updated their site to include a statement claiming that it would ask for permission before mining on someone’s computer going forward. Coinhive stated in September 2017:
“We're a bit saddened to see that some of our customers integrate Coinhive into their pages without disclosing to their users what's going on, let alone asking for their permission.”
However, given the practice is still alive and well as of this month, with examples such as the Telecom Egypt case, it seems unlikely that Coinhive has been able to follow through on their promise.
Permission-based cryptojacking: the Salon case
News site Salon.com has willingly hopped onto the cryptojacking trend by giving its users the option to allow Salon.com to access their “unused computing power” as an alternative to seeing advertisements. While Salon’s FAQ about this new option neither directly mentions the word “mining” nor the company “Coinhive,” the Financial Times notes that a pop-up on Salon about this new process features the text “powered by Coinhive”.
Selva Ozelli, a Cointelegraph contributor and international tax attorney, says that Salon’s new use of Monero mining as an alternative form of monetization to traditional advertising is not illegal in the US. However, Ozelli notes that the tax regulations around crypto mining would mean that any money that Salon makes off of its visitors in this manner would need to be taxed appropriately:
“Under IRS Notice 2014-21, crypto/bitcoin mining is not a tax free exercise. If you mined crypto/Bitcoin as a trade or business, miners would have to recognize income for each bitcoin mined during the taxable year.”
Since the basis of calculating how much tax to pay on mining profits involves deducting the mining expenses, i.e. “electricity, and depreciation on your mining rig,” it is unclear how Salon would delineate their expenses from their income tax forms.
Ozelli told Cointelegraph that is is likely that the Internal Revenue Service (IRS) will need to develop a framework for these new types of profit-making mining situations:
“Since electricity is a deductible mining expense for those who are engaged in a trade or business of crypto mining, likely there will be IRS guidance provided.”
Another example of a permission-based cryptojacking business model comes from an unlikely source: UNICEF (United Nations International Children’s Emergency Fund). The fund began a charity drive for Syrian refugees in February 2018. On top of accepting fiat donations, UNICEF targeted PC gamers, asking them to let the charity use their high-powered PCs to mine for Ethereum (ETH) during the gamers’ downtime.
The ethics of cryptojacking
The case of malicious cryptojacking, when users’ computer processing power is siphoned off without their permission or knowledge can clearly be classified as an unethical, and illegal, action. However, both Salon and UNICEF’s permission-based cryptojacking brings up the ethical debate of the morality behind offering users an option of which they may not fully understand the consequences.
The already mentioned Concordia University study into cryptojacking discussed the question of ethics, questioning whether an average internet user would be able to understand what they are agreeing to when they “opt in” to cryptomining to avoid advertisements, or gain access to paywall content, higher definition videos, ect.
It is entirely possible that many users may not realize that they are signing up for the potential for raised electricity bills, slower computer and Internet performance, and shorter device lifespan. This is especially true in cases, as with Salon.com, when the language of the permission-asking is deliberately vague or misleading.
On the other hand, the Concordia report mentions the idea that many Internet users already often give their consent to things they likely don’t fully read or understand online, like privacy disclosures and cookies tracking. As a conclusion to the ethics of non-malicious cryptojacking, the reports notes that nothing is “clear cut” and that the nuances should be further debated for potential regulation.
How to keep your computer safe from cryptojacking
Let’s say that you aren’t a PC gamer planning on donating your computer’s free time to UNICEF, and you don’t regularly read Salon – how do you stop cryptojacking malware from entering your computer?
One option is to use the Opera web browser, which blocks crypto mining scripts on both its web and mobile versions as of this January.
The above-mentioned Microsoft report notes that Windows Defender Anti-Virus blocks unwanted applications, citing that the number of coin miners blocked from being downloaded jumped from 2 to 6 percent of all unwanted app downloads from September 2017 to January 2018. Microsoft adds that a variety of their Windows Defender programs can prevent crypto miners from entering corporate networks.
Cointelegraph also published a guide in October of last year for checking if your computer has been cryptojacked. The first thing to do is check on your computer’s CPU usage and make sure that there are no unexplained spikes of processing power use after you visited a website.
Ad blockers are another way to go, as some have added Coinhive to the list of blocked scripts. If you think you have been targeted by more malicious forms of malware, like the trojan injection attempts that Microsoft recently discovered and blocked, you can use Task Manager to terminate the malicious script.
Sourse: https://cointelegraph.com/news/the-ethics-of-cryptojacking-rampant-malware-or-ad-free-internet

Coins mentioned in post:
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://cointelegraph.com/news/the-ethics-of-cryptojacking-rampant-malware-or-ad-free-internet
For future viewers: price of bitcoin at the moment of posting is 8211.00USD