A Primer to the Lightning Network (Part 3): The Full Picture
In Part 2, we looked at how the Lightning Network (LN) would work between 2 people. In this final article, we will explore how the LN works between 3 people, how Atomic Swaps work, and the full picture of the Lightning Network.
The Lightning Network with 3 People
In a different scenario from Part 2, let’s say Alice wants to hire Carol as a Graphic Designer. Alice offers Carol 1 LTC on the condition that Carol completes her job within 30 days. Instead of going through the hassle of creating a multisig address for the both of them, Alice notices that they have a common friend named Bob. Alice has a multisig address with Bob already and she notices that Carol does too. Both of these multisigs are 2 of 2. Alice then decides to send Carol 1 LTC through Bob.
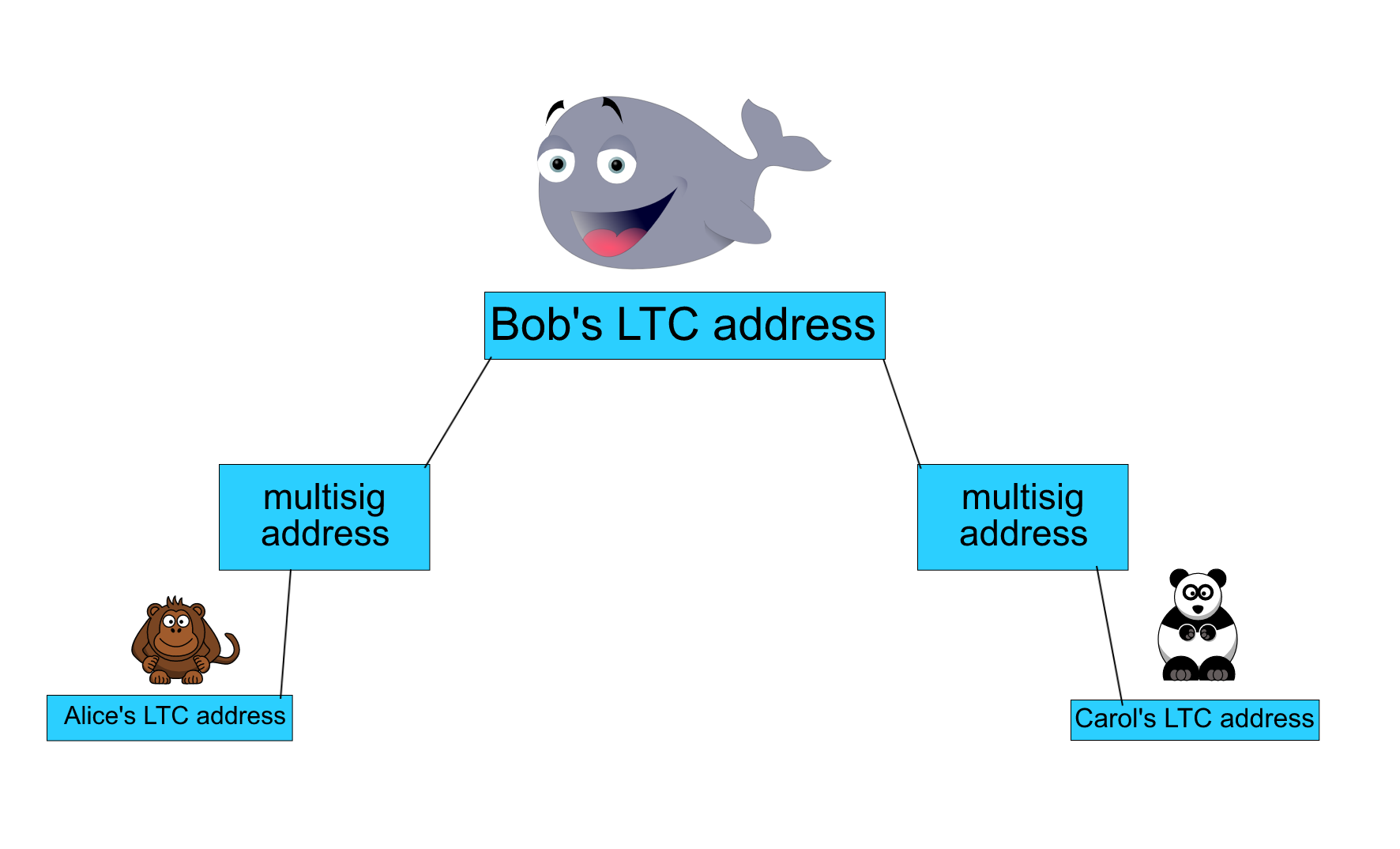
Now in order to do pull this off, we’ve got to do something called “hashing.” Hashing simply means converting a string of alphanumeric characters (R) into a random string of numbers called a “hash.” The cool thing about hashes are that you can reproduce the hash if you have the original data set (R). However, you can’t reproduce (R) from the hash. This unique characteristic allows the hash to act as a “lock” for Alice’s 1 LTC that can only be released if you have the key (R).
Step 1
Carol creates a random string of alphanumeric #’s (R) through her LTC wallet and then hashes it. She sends this hash to Alice. The hash will serve 2 purposes in this scenario: 1) a receipt 2) and a lock
A Receipt
The Lightning Network transactions occur “off chain” meaning they’re not recorded on the blockchain. Because of this, Carol has no idea that Alice is the one sending the LTC. However if Carol sees the hash, she’ll know it’s from Alice. In this way, the hash acts like a receipt.A Lock
When Alice sends the 1 LTC, she will create the condition that the LTC can only be cashed out if (R) can be reproduced. Therefore, the LTC is locked up until Carol provides the key=>(R). This is called a “Pay to Contract” transaction.
Step 2
After Alice receives the hash, Alice then creates a smart contract on her multisig with Bob locking up her 1 LTC so that it’ll be returned to her in 30 days. This then creates the first open payment channel between Alice and Bob. Bob does the same with Carol.
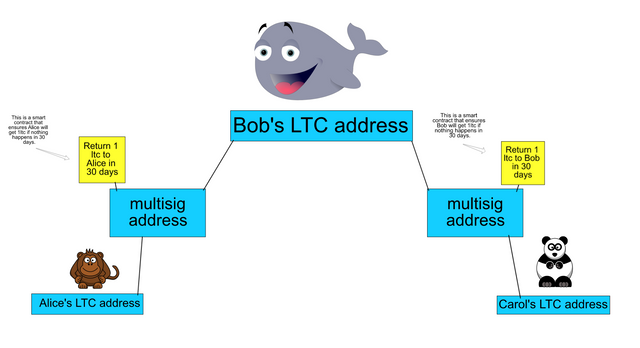
Step 3
Alice then sends 1LTC to Bob but includes the hash stating it can only to be cashed out if (R) is produced.

Step 4
Bob can’t take or steal Alice’s LTC because he doesn’t have (R). So he sends his own LTC combined with the hash to Carol.
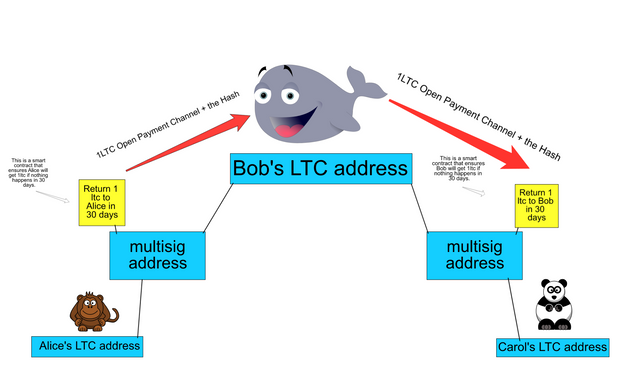
Step 5
Carol then claims her coin by showing Bob (R). Bob can then claim his coin by showing (R) to Alice. And voila! Believe it or not, that’s it!
What about Atomic Swaps?
Atomic Swaps allow users to trade between two cryptocurrencies without going through an exchange.
This is how it works between 2people:
- LTC is sent from Alice -> Carol
- At the same time, BTC is sent from Carol -> Alice
- To do this, you will need to have multisigs for both LTC and BTC.
This is how it works between 3people:
- First, LTC is sent from Alice -> Bob -> Carol.
- At the same time, BTC is sent from Carol -> Bob -> Alice.
- To do this, you will need to have multisigs for both LTC and BTC.
The Full Picture of the Lightning Network
Consider Bob a hub that not just 2 people, but 5 or 10 people are connected to. Bob can also connect to another hub that’s also networked with another 10 people. This is the full vision of the Lightning Network: Peer-to-Peer, zero payment transactions, Atomic Swaps of different currencies, and hundreds if not thousands of multisig addresses connected through multiple hubs.
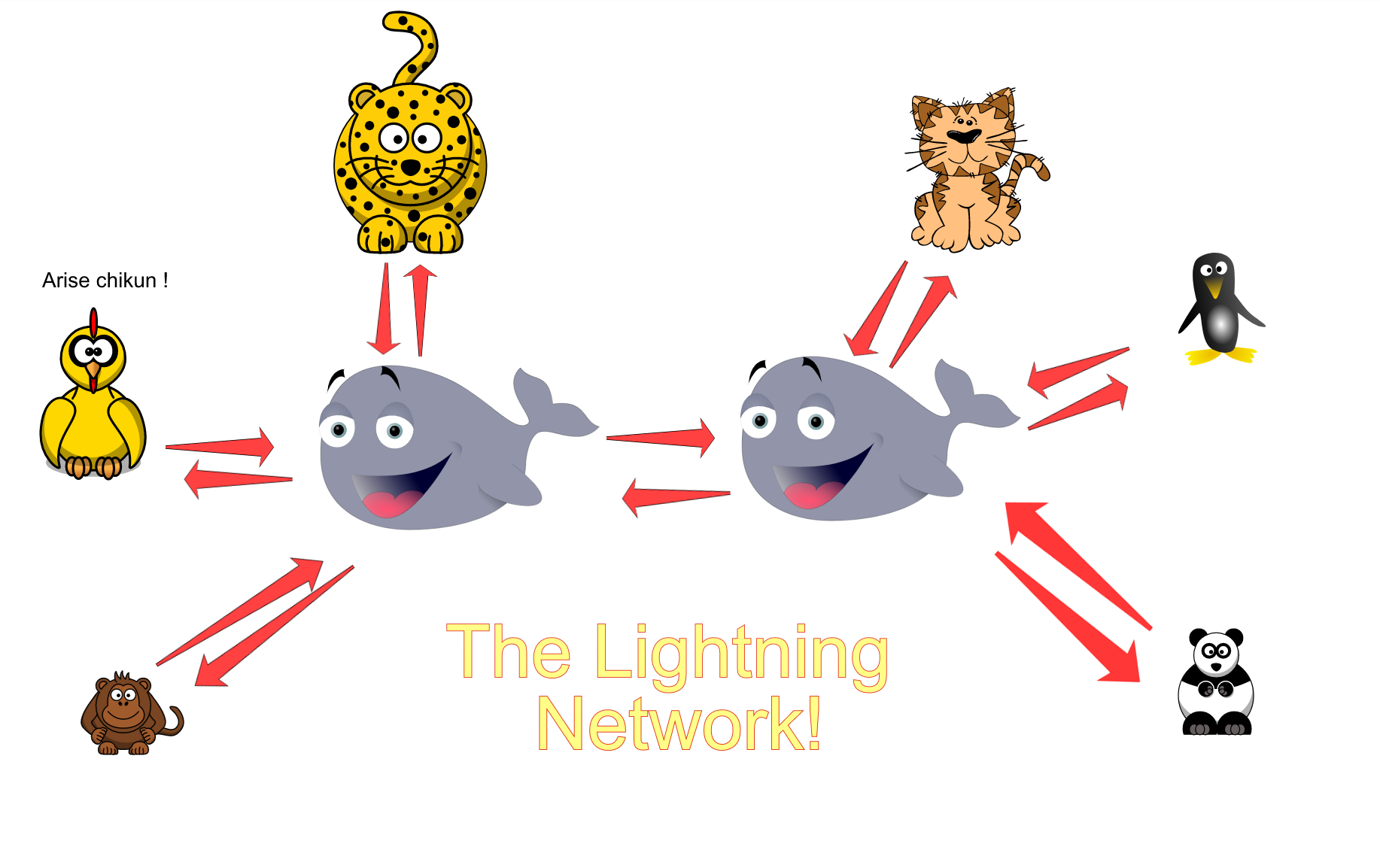
Final Comments:
- It is noteworthy to mention that Bob will most likely have to be a “whale” to provide all the LTC and BTC for the atomic swaps.
The LN is also a bit more complex than I’ve described because it can include other factors such as adding a decreasing nLockTime to each proposed payment offer. This means that every offer Alice makes will expire faster than the one before it. This negates the previous offers. There will also be punishing contracts in case a party attempts to steal coins. - One exciting new LN development that Elizabeth Stark briefly mentioned at the Blockstack Summit 2017 is the possibility of Layer 3 capabilities. For example, Layer 1 is the blockchain, Layer 2 is the LN, Layer 3 would be contracting abilities for apps to be built on top of which would tap into Layer 2 then Layer 1.
- If this was a bit overwhelming have no fear! The Lightning Team is developing a User Interface (UI) that will take care of all of this for you. For example, Jack Mallers recently announced ZAP: A Lightning Network Wallet. This is a wallet that allows LN transactions between 2 people. He will release the source code within the week. Take a look. It is simple, stunning, and very user friendly.
- Finally, if you’d like to get involved with Lightning Network Development, check out this website to learn more about how to get involved here: http://dev.lightning.community or their git hub here: https://github.com/cdecker/lightning-integration
Alright, you’ve made it! Congratulations and thanks for joining me on this three part journey of understanding the Lightning Network! If you liked this series, give my article a green heart on the left, share it with your friends, and follow. 😁 Until next time, onwards and upwards!
Discussion Questions:
- What are some concerns you may have about the LN network?
- What two segwit enabled coins would you atomic swap first?
- What technology in cryptocurrency do you want to know more about next?
Sources:
https://lightning.network/
https://streams.lykke.com/Project/ProjectDetails/b134b15b54e745559f26c217bef5a2f8
Donation Addresses:
LTC: LRrekGu3D4ALFvVwWHNXxBMpphujHCnPkv
BTC: 1Mj6Jrz8WzgnQPP2KQrQXZ6AUWcLsTJukg
P.S. Follow me on twitter at ecurrencyhodler!