CryptoNote - Bitcoin killer?

The project CryptoNote positions itself as an open source technology and the concept of the future of the crypto currency. Developers are going to apply advanced mathematical analysis and innovative ideas to promote cryptoanarchism and egalitarianism in the name of changing the global paradigm. On the basis of this algorithm, crypto-currencies such as Bytecoin, Monero, Boolberry, Bitmonero, QuazarCoin, Fantomcoin have already appeared and, judging by the trends, a lot of other forks are expected.
CryptoNote provides users with a completely anonymous payment plan. It is implemented using ring-signing technology, which allows you to sign a message on behalf of the group. The signature says only that the transaction is committed by someone from the group, but all the members of the group are indistinguishable from each other. No one is able to make the same payment twice. The modified Diffie-Hellman exchange protocol is used to map unique public key addresses.
Each transaction made makes the block as a whole even more resistant to analysis. Built-in processor instructions are used, which are extremely difficult and expensive to implement in ASIC, but which work perfectly on a general-purpose PC. The network changes adaptively, based on its previous states. There is a forum on the CryptoNote website, there is a link to White paper, a link to the first crypto currency based on this technology - Bytecoin [BCN], launched on July 4, 2012 (not to be confused with Bytecoin [BTE] on sha256, which is an unremarkable Bitcoin fork ). Another pleased button - "Submit your coin" by clicking it, you can send created on this algorithm crypto currency for community consideration. More on the site, except for e-mail, nothing and no.
Let's start with the fact that we revere White paper. In this document, a certain Nicholas van Saberhagen immediately takes the bull by the horns, listing the advantages of Bitcoin. In his opinion, these include:
Successful implementation of the idea of a decentralized e-currency.
Both professionals and ordinary public appreciated the combination of publicity of transactions and the concept of proof of work.
Buyers are attracted by the low commission and high level of anonymity provided by electronic currency. Vendors, in turn, are attracted by predictable and decentralized emissions.
Bitcoin proved that electronic cash can be as simple as paper money and reliable, like bank cards.
At the same time, the Bitcoin network has its drawbacks. The structure is not flexible, since most clients that use this protocol need to update to make changes.
For the sake of healthy competition and the creation of the next technology of electronic cash, the CryptoNote project was created.
Privacy and anonymity for electronic money are most important. Decentralized payments hidden from the eyes of a third person - this is what distinguishes crypto-currency systems from the traditional banking system. T. Okamoto and K. Ohta described six criteria for ideal electronic cash. In particular, they include confidentiality: the details of the transaction between the seller and the buyer should not be known to anyone else. To ensure confidentiality, it is required that electronic money satisfy two requirements:
- Non-traceability. For each incoming transaction, all senders are equally likely.
- Unrelatedness. For any two outgoing transactions, it is impossible to prove that they are sent by the same person.
Unfortunately, Bitcoin does not satisfy the first requirement, since all actions taking place between network members are open. The sender and the receiver can be uniquely identified. Even if the exchange between participants is not direct, a study of the history of transactions will disclose the origin of the funds, their recipient and the sender.
Many justifiably suspect that Bitcoin does not satisfy the second requirement. A thorough analysis of the blockage can reveal the connections between users of the Bitcoin network and their operations. Although a number of methods for such analysis are controversial, there is a suspicion that a large amount of personal data can be extracted from the public database - a detainee.
Based on this, we can assume that Bitcoin is not anonymous, but a pseudo-anonymous electronic currency. Users quickly began to look for ways to get around this flaw. There were methods based on mixing of transactions and on distributed solutions. But both approaches are based on the idea of mixing several transactions and sending them through an intermediary address, that is, they require a trusted third party.
More creative approach suggests Meyers and other cryptographers with the Zerocoin project (Zerokoin). The zero-disclosure proof underlying this system uses anonymous proof of ownership rather than the public key algorithm. Nevertheless, the authors acknowledge that the proposed changes in the protocol are unlikely to be accepted by all users.
Satoshi Nakamoto wanted one processor to match one voice of the system member. This scheme protects immediately from two possible problems. First, we can be confident in 51% of honest users. Secondly, the introduction of changes to the system is carried out by a majority of votes, when the majority of users have updated their software. One participant in the system should not have a significant advantage in voting on another participant. This is achieved due to the high cost of computing devices.
But it turned out that SHA-256 creates a big gap between the participants. This was facilitated first by switching to graphics processors, and then to ASIC devices. They received an overwhelming preponderance over the owners of processors. Now you see the classical implementation of the Paretto theorem, or rules 20-80: 20% of the participants control 80% of the computing power of the entire network. This means that the 51% attack is still theoretically possible.
Irregularity of issue
Bitcoin has an algorithmically assigned emission: each block found produces a specified number of coins. Satoshi Nakamoto originally wanted to create a smoother emission, but as a result, we have what we have. Approximately once in 4 years, the reward for the block is divided in half. Graphs show a sharp decrease in the power of the network with each division of the award in half. Such a period would be an excellent opportunity for a malicious attack of 51%.
Hard-coded constants
Hard-coded constants are part of the original Bitcoin development. Among such constants one can name the frequency of appearance of blocks, the total number of currency units, the number of confirmations. Unfortunately, the inability to change many of these constants can lead to terrible consequences. A recent example will be a good example. In early 2013, there was a block size limit of 250 kilobytes, which is about 10,000 standard transactions. When attempting to make a change to the purse version 0.8, there was a branching into 2 chains of a length of 24 blocks, and a successful double-spending attack took place. The fault was not Bitkoyn's protocol, but the database in which the error occurred. This would not happen if the database passed the simplest stress test.
In part, the constants are centralization. Despite Bitcoin's distributed nature, the vast majority of nodes use a client version developed by a small group of people. Because of this, most accept changes regardless of their correctness. This has often provoked heated discussions. Therefore, it seems logical that a protocol with self-adjusting variables or with the ability to configure them by users could solve these problems.
Bulky Scripts
The system of scripts in the Bitcoin network is cumbersome and complex. It potentially allows you to create more complex transactions with transactions, but many features have been disabled for security reasons, and some have never been used at all.
Having listed the disadvantages of Bitcoin technology, we will concentrate on the advantages of CryptoNote technology:
Transactions without leaving a trace
Let us consider several possible schemes that satisfy both the untrackability condition and the incoherence condition. An important feature of these schemes is their autonomy - the sender is not required to cooperate with other users, or trust a third party to make a transaction.
The scheme, first introduced by D. Chaum and E. van Heist, refers to the basics of cryptography. It allows the user to sign his message on behalf of the group. But in this case there is a trusted third party (the so-called group manager), who can uniquely identify the signatory.
The development of this technology is a "ring signature" - in this case there is no group manager, the scheme is autonomous. There are modifications to the ring signature, which allow you to determine whether the letter is signed by the same participant twice. For the most part, the work of the authors is based on the writings of E. Fujisaki and K. Suzuki. But CryptoNote emphasizes the ability for the user to produce only one valid signature with his private key. Traceability is weakened to two options: a secret key for generating a unique anonymous signature and a public key that can be associated with it in the event of an attempt to double the expense of funds.
The basic signature algorithm is the fast EdDSA scheme. It is based on the discrete logarithm of an elliptic curve. The structure of the deal in Bytkoyne is similar to the structure of the Bitcoin transaction - each user can select several unrelated inbound payments (exit points), sign them with appropriate private keys and send them through the network.
Unlike the Bitcoin model, where a user has a unique pair of private and public keys, in the case of Bytkoyn, the sender generates a one-time public key based on the recipient's address and some random data. In the incoming transaction, the recipient uses a one-time public key, and only the recipient of the means can use it with his private key. The recipient can spend money using a ring signature, keeping anonymity of the purse and its actual costs.
In the case of Bitcoin, the once published address becomes a unique identifier for the connection of incoming payments and the recipient. To hide your transactions, you must generate new addresses for each incoming transaction each time, and do not talk about their connection with you.
By default, each CryptoNote output is a public key based on the recipient's public address and the sender's random data. Thus, for an outsider, all transactions are equal. To ensure this capability, Kryptonot's address has to be almost twice as large as Bitcoin's address. The recipient also generates a Diffie-Hellman transformation to recover the private key.
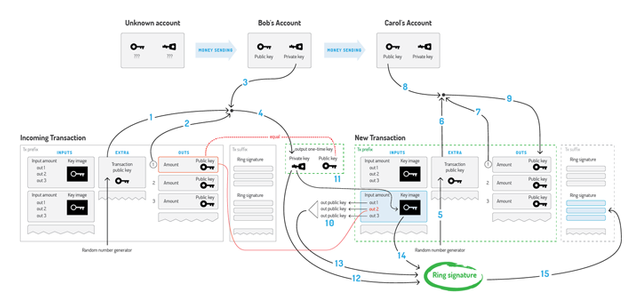
Suppose Alice wants to send funds to Bob. Based on Bob's address and the random number generated on Alice's side, a one-time public key is calculated. Bob checks this data with his secret key and receives funds if the keys match. The processing of Bob's and Alice's transactions can, for example, be entrusted to Carol. She will not be able to use the funds without Bob's secret key. This approach is justified if there is not enough bandwidth on the side of Bob (smart phones and other hardware wallets).
One-Time Ring Signature
The idea is simple - the user generates a signature that is checked using a set of public keys, and not the unique public key itself. The identity of the signer is indistinguishable from other users whose public keys are in the same set.
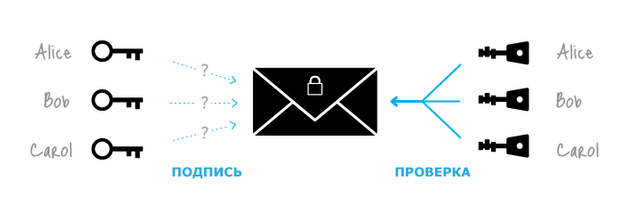
The signer can declassify himself, deliberately reproducing the second signature using the same key pair. By default, this feature is disabled.
Egalitarian proof of work
In this section, just such hardware is used to calculate the algorithm. The main task is not to create a gap between users of personal computers (majority), and owners of specialized devices and video cards (minority).
Why CryptoNote?
Abadi and other cryptographers have developed memory-responsive algorithms. The basic idea is to allocate a large data block (notepad) in RAM with an unpredictable sequence of data in it. The block should be large enough to make the storage of data more convenient than computing them with each access. The algorithm should also prevent internal parallelism, that is, N simultaneous threads should require N times more memory at once.
Algorithm Scrypt, although it uses memory, still leaves the possibility of building powerful and relatively inexpensive computing devices for calculating this algorithm. In the case of CryptoNote, unlike Scrypt, each new block (64 bytes) depends on all previous blocks. The proposed algorithm requires about 2 MB of RAM, since this is the size of the L3 cache (per core) for a modern processor. At the same time, this amount of RAM excludes the use of ASIC. Graphics processors can process hundreds of parallel streams, but they are also not suitable for computing this algorithm, because the GDDR5 memory runs much slower than the L3 cache.
Additional advantages:
Smoothly falling emissions;
Miners independently regulate the size of the blocks. If someone wants to create a huge deal with hundreds of entrances and exits, or with a ring sign of a very large size, he can do this by paying a sufficient commission;
Incredibly small intervals between blocks;
Possibility of protection with a secret password.
Nobel laureate Friedrich Hayek in his famous work proves that the competition of independent currencies has a huge positive value. The issuer (in our case, the developer) is trying to attract users by improving its product. The most convenient and reliable currency will have the greatest demand. Suppose a currency greater than Bitcoin appears, this will stimulate Bitcoin to work faster and become better.
It is necessary to distinguish CryptoNote and CryptoNight.
CryptoNight is one of the implementations of the CryptoNote protocol . On the algorithm "CryptoNote" built Bytecoin ("Bitcoin").
He, like Darkcoin, has anonymity, but does not require the creation and maintenance of a cumbersome node system. This fact alone is enough to consider this crypto currency in more detail.
Features of Bytecoin [BCN]:
Unspecified payments;
Unreliable transactions;
Protection from double-spending coins;
Immunity to any analysis of the chain of blocks;
Equal PoW-confirmation of the block;
Adaptive (adjustable) parameters.
Specifications Bytecoin [BCN]:
Algorithm: CryptoNight. Only for processors. Algorithm demanding memory.
Time between blocks: 120 seconds (2 minutes);
Difficulty recalculates each block;
The reward for the block is calculated by the formula BaseReward = (MSupply - A) / 218, where MSupply = (264 - 1) is the number of the smallest units, and "A" is the number of coins already issued;
One coin is divided up to 8 decimal places. Actual number of indivisible units M = 264 - 1;
The total emissions will be: 18,446,774,073,709,551,616 the smallest units (= 184.46 billion BCN).
Here you can see the technical documentation of the project. On this page you can download purses - for Windows, Mac and Linux, as well as source code.
It remains only to decipher the word "egalitarian", which developers use so often. It came from the French word égalité - equality) - a concept based on an idea that involves the creation of a society with equal political, economic and legal opportunities for all members of this society. Opposite to elitarism. Egalitarianism occupies an important place in the writings of Plato, Aristotle, Hobbes, Locke, Rousseau, Babeuf and other thinkers.
Neoconservatives are negative about this idea, considering it to be contrary to human nature.
A curious feature of the CryptoNote technology was that, after the platform appeared in the public sphere, Fortsecoin forks began to appear almost immediately. This probably indicates the good potential of this technology. Not without the comic fork of DuckCoin, the local analogue of Dogecoin. Also an interesting story happened with BitMonero fork: the original creator of this fork had the imprudence not to listen to the aspirations of the local community, while the fork was just gaining popularity, and the initiative in this fork was intercepted by local patrons. However, they do not yet show a deep understanding of the technology and basically are engaged in copying commits from the main repository of bitcoin , but they are actively promoting it. Essential technical differences are forked by the Boolberry. The developers have introduced a number of quite original innovations, which should be mentioned briefly:
Blockchain-based PoW
The developers of Boolberry claim that they found an original way out of the problem of heavy hash functions that work on large scratchpads. Scratchpad is the term used to designate the portion of memory used by the hash function for computation. Often, the reliability of modern PoW hash functions is associated with the size of the scratchpad - the larger it is, the more difficult it is to implement efficient hardware execution.
Instead of creating and scratching the entire scratchpad for each counting of the hash function, they form one common scratchpad based on the data from the block (block hashes, one-time keys with coinbase, merkleroot), so that at a given block height any node has An identical scratchpad, which is gradually increasing with each new block. The hash is now a hash function called keccak, modified in such a way as to make a large number of hits to the scratchpad at the pseudo-random addresses.
It turns out that the process of checking the hash is extremely fast, and the process of mining is neither memory-hard, which is considered a good protection from ASIC. According to the website of the developers, if the scratchpad is increased to 100MB (ie, there is much more memory cache for the processor), the hash function slows down three times, which indicates the actual dependence of the algorithm on memory operations.
Outputs with guaranteed anonymity.
This feature reinforces the property of non-tracability of transactions: in the classical CN scheme, when the wallet dials the outputs to the ring signature, it can not guarantee that these outlets will not be spent in the future anonymously (if the owners use them in their transactions without mixing , Then their meaning in this circular signature is lost, because it becomes obvious that they are here only for "extras"). The developers of Boolberry have introduced an additional attribute that can specify the policy of using the output: classical (relaxed), the output must be used without mixing, and the output must be guaranteed with mixing with not less than n other outputs. When using outputs with guaranteed mixing in the ring signature, it is guaranteed that the untraceability of such a transaction will not be compromised in the future.
Identification of transactions by prefix.
It is alleged that this will reduce the size of the blockage by 30% (here clearly refers to that part of the bokchayna that is inside the checkpoints) by throwing out ring signatures from transactions.
Aliases of purse addresses.
Any address in Boolberry can be bound to a symbolic name, which can then be used on any of the clients. Registration is possible only in the block, while in each block you can register or re-register only one name, the uniqueness of the names is guaranteed by the crypto-currency kernel. Thus, now you can only have your own alias with a miner who is able to independently find the block. Most likely, the service for registering aliases will later become the prerogative of pools.
However, the wonderful features of Boolberry also create some difficulties: because of the unusual approach to PoW, Boolberry is experiencing a number of technical problems with the implementation of pools, because classic pools do not know how to deliver a scratchpad. At the time of writing, the number of supporting Boolberry pools was noticeably smaller than that of Bytecoin / Monero.
Another feature of this project is the monetization model: the developers in each 720th block are remunerated in accordance with the votes of the miners, the maximum possible reward is 1%. The developers of Boolberry also claim that 10% of this amount is transferred to CryptoNote, probably as royalties.
So, can Bytecoin, Boolberry, Monero and other descendants of CryptoNote be more interesting to anyone than Bitcoin? To begin with, there are people who are more interested in the society of scratchpads, elliptical curves and points A and A 'than the society of intoxicating friends and gay girlfriends, and the more complex CryptoNote model will not only scare away from Bitcoin but will also cause a much larger interest.
A mathematically proven forced anonymity may interest those who do not want anyone to dig into their transactions.
Will there be an interesting remuneration procedure for miners? Here is one of the most important questions on which really a broad acceptance of a coin depends. Since each PC can do a mine, the PC network for mining may be much wider than the ASIC network for Bitcoin. On the other hand, there is a return to an era when one or more supercomputers can affect a network that needs to grow to the size of Bitcoin. So the question remains open.
https://en.wikipedia.org/wiki/Zero-knowledge_proof
https://wiki.bytecoin.org/wiki/Main_Page
https://cryptonote.org/whitepaper.pdf
https://cryptonote.org/
http://boolberry.com/