CYPHERIUM ENHACES BLOCKCHAIN TECHNOLOGY
OVERVIEW
Rarely has any technology such as blockchain attracted the public and media organisations. Institutions designed to catalyze the fourth industrial revolution are experimenting with technology, and investors have invested hundreds of millions of dollars in blockchain companies. This is a low-risk, experimental environment with error protection. Innovation is a combination of creativity and implementation. Ideas often must go through an evolutionary or cyclical phase before they are ready for commercialization. In fact, the cycle is so long that it is too expensive, inefficient in terms of time and money to generate and generate ideas, and in most cases almost never reaches commercial value. Thus, almost 99% of venture capital firms fail.
A fast growing technology that has come to enhance the blockchain technology is CYPHERIUM.

CHALLENGES FACING THE BLOCKCHAIN TECHNOLOGY
The Bitcoin framework is one of the most notable usage of blockchain innovations in circulated exchange based frameworks. In Bitcoin, each system hub seeks the benefit of putting away a lot of at least one exchanges in another square of the blockchain by comprehending a complex computational math issue, here and there alluded to as a mining verification of-work (POW). Under current conditions, a lot of exchanges is ordinarily put away in another square of the Bitcoin blockchain at a pace of around one new square like clockwork, and each square has an inexact size of one megabyte (MB). As needs be, the Bitcoin framework is dependent upon a looming versatility issue: as it were 3 to 7 exchanges can be handled every second, which is far underneath the quantity of exchanges handled in other exchange based frameworks, for example, the roughly 30,000 exchanges for each second in the Visa™ exchange framework. The most huge disadvantage of the Nakamoto accord is its absence of irrevocability. Conclusion implies once an exchange or an activity is performed on the blockchain, it is for all time recorded on the blockchain and difficult to turn around. This is fundamental to the wellbeing of money related repayment frameworks as exchanges must not be saved once they are made. For Bitcoin's situation, noxious on-screen characters can alter the exchange history given enough hash power, causing a twofold spending assault, given that there is sufficient motivator and money related practicality to complete such assaults. Given that mining gear leasing and botnets are at present predominant around the world, such an assault has become achievable.
Because of this absence of conclusiveness, Nakamoto accord must depend on additional measures, for example, confirmation of-work to forestall pernicious exercises. This hinders the capacity ofNakamoto accord to scale in light of the fact that a exchange must hang tight for various affirmations before coming to "probabilistic absolution".
In this way, wellbeing isn't ensured by Nakamoto agreement, and so as to secure the system, each exchange must experience extra an ideal opportunity to process. For Bitcoin's situation, an exchange isn't considered last until in any event six affirmations. Since Bitcoin can just process a couple of exchanges every second, the exchange cost is preposterously high, making it unreasonable for little installments like shopping for food or eatery feasting. This extraordinarily frustrates Bitcoin's utilization as an installment strategy in this present reality.

CYPHERIUM SOLUTIONS
Cypherium's exclusive algorithm, CypherBFT conquers burdens of the earlier craftsmanship by giving a circulated exchange framework including a gathering of validator hubs that are known to each other in a system however are undefined to the next system hubs in the system. As utilized thus, the gathering of validator hubs might be alluded to as a "Board of trustees" of validator hubs. In a few explanations, the framework reconfigures at least one validator hubs in the Committee dependent on the consequences of confirmation of-work (POW) challenges. As per some uncovered epitomes, a system hub that isn't as of now a validator hub in the Committee might be added to the Committee on the off chance that it effectively finishes a POW challenge. In such an occasion, the system hub may turn into another validator hub in the Committee, supplanting a current validator hub. In elective epitomes, a system hub may become another validator hub in the Committee dependent on a proof-of-stake (POS) accord. In yet another epitome, a system hub may turn into another validator hub in the Committee dependent on a verification of-authority (POA) agreement. In other elective exemplifications, a system hub may turn into a new validator hub in the Committee dependent on a mix of any of POW, POA, and POS accord.
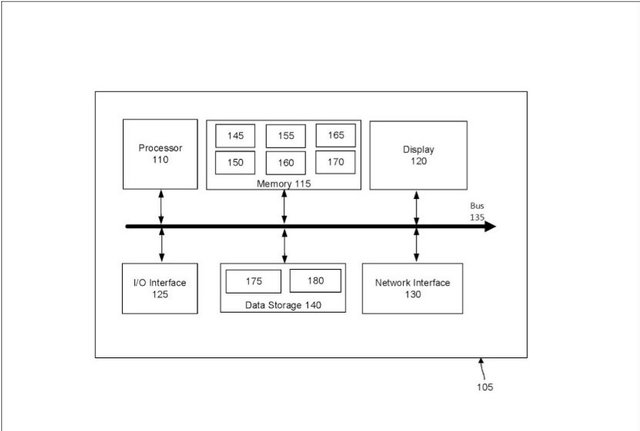
In some revealed exemplifications, the new validator hub replaces a validator hub in the Committee. The substitution might be founded on a foreordained guideline known by all the hubs in the system. For model, the new validator hub may supplant the most established validator hub in the Committee. As indicated by another model, the new validator hub may supplant a validator hub that has been resolved to have gone disconnected, become bargained (e.g., hacked), fizzled (e.g., because of equipment breakdown), or in any case is inaccessible or not, at this point trusted. In the praiseworthy exemplifications, the circulated framework expect that for an adaptation to non-critical failure of f hubs, the Committee incorporates at any rate 3f +1 validator hubs.
Since the validator hubs in the Committee might be every now and again supplanted, for instance, contingent upon the measure of time required to finish the POW challenges, it is hard for vindictive outsiders to identify the total arrangement of validator hubs in the Committee at some random time.

BENEFITS OF CYPHERIUM BLOCKCHAIN TECHNOLOGY
Cypherium runs its exclusive CypherBFT accord, tied down by the HotStuff calculation, and can genuinely offer moment irrevocability for its system clients. With its HotStuff-based structure, the CypherBFT's runtime keeps going just 20-30 milliseconds (ms). A few affirmations are all that is required to for all time acknowledge a proposed obstruct into the blockchain, and it just takes 90ms for these affirmations to come to pass, making the procedure essentially quicker than the two-minutes required by EOS.
Cypherium's CypherBFT, which additionally uses HotStuff, doesn't have to pick between responsiveness and linearity. Cypherium's double blockchain structure incorporates the velocities of a dag, however its review for clients can occur a lot more straightforward and quicker, which adds to the accessibility of data and makes the data more decentralized.
As per some revealed epitomes, the validator hubs in the Committee may get exchange demands from other system hubs, for instance, in a P2P organize. The Committee may incorporate at any rate one validator hub that fills in as a "Pioneer" validator hub; the other validator hubs might be alluded to as "Partner" validator hubs. The Leader hub might be changed occasionally, on request, or inconsistently by the individuals from the Committee. At the point when any validator hub gets another exchange demand from a non-validator hub in the system, the exchange solicitation might be sent to the entirety of the validator hubs in the Committee. Further to the unveiled epitomes, the Pioneer hub facilitates with the other Associate validator hubs to arrive at an accord of an attitude (e.g., acknowledge or dismiss) for an exchange square containing the exchange solicitation and communicates the accord to the whole P2P arrange. In the event that the accord is to acknowledge or in any case approve the exchange demand, the mentioned exchange might be included another square of a blockchain that is known to in any event a portion of the system hubs in the system.
In conclusion, CYPHERIUM'S distributed smart-contracts block-chain is ideal for a good number of use cases which include (but not limited to):
Finance
Messaging
Voting
Notarization
Digital Agreements (Contracts)
Secure data storage
A.I (Artificial Intelligence)
IoT (Internet of Things
To know more about CYPHERIUM kindly visit the following links:
WEBSITE: https://cypherium.io/
GITHUB: https://github.com/cypherium
WHITEPAPER: https://github.com/cypherium/patent/blob/master/15224.0003%20-%20FINAL%20Draft%20Application%20(originally%200003%20invention%201)%20single%20chain%20in%20pipeline.pdf
TELEGRAM: https://t.me/cypherium_supergroup
TWITTER: http://twitter.com/cypheriumchain
FACEBOOK: https://www.facebook.com/CypheriumChain/
AUTHOR: Nwali Jennifer