What is The DDoS Attack and how it takes down big sites?

If a known international site you are visiting shows to be malfunctioning or has dropped completely for some hours, it is most likely that the culprit is a DDoS attack. According to Verisign, 50 million cases are reported annually, which can even knead the largest sites. See what DDoS is and what makes it so dangerous.
What is DDos and DoS Attack?
DDoS and DoS are abbreviations of Distributed Denial of Service. In Greek it translates as "Distributed Denial of Service Attack".
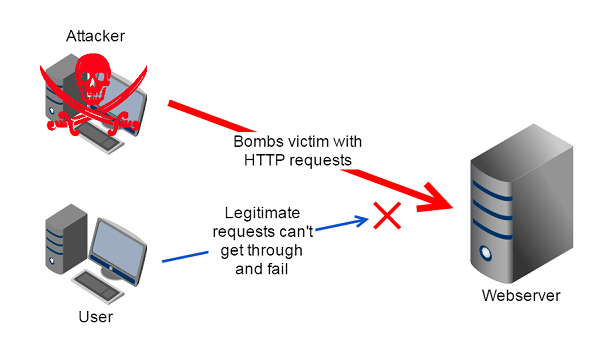
A DDoS attack targets a system, usually a server or a whole data center (datacenter). The attack "bombs" the system with a huge amount of data from different sources.
The system, in its attempt to respond, ends up exhausting its resources, such as CPU, RAM, and so overloads and eventually collapses.

A "DDoS attack" that we have unwittingly involved in
Have you noticed that on New Year's Day, with the change of time or immediately after Easter Resurrection, it is difficult for a few minutes to make a call or even send sms with the cell phone?

This is because too many subscribers are trying to use the network at the same time. The same applies in the case of an extensive natural disaster, such as an earthquake.
Under normal circumstances, only a percentage of users need access to the network at any time.
Thus, virtually no large network, be it a cellular network or a web site, is not designed to support all users at the same time. It would be a huge waste of resources.
A malicious overload
Something similar happens in a DDoS / DoS attack, though for quite different reasons. In this case, they are not real users who are blocking a network or a server. These are automated actions through software.
These actions are not intended to use the server but to block it. Thus, they prevent real users from having access to the network.
In fact, because the actions are meant to block, they use a larger volume of data than a simple user.
A computer that is involved in a DDoS attack can cause a charge equal to hundreds or thousands of regular users.
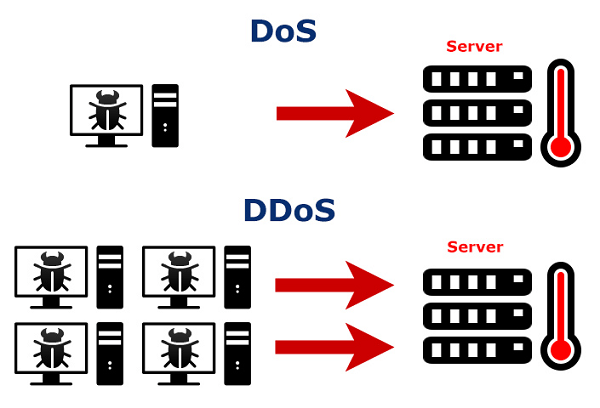
DDoS and DoS attacks essentially refer to the same thing, with a difference in scale.
DoS attack is a small-scale case, usually from a victim-victim system to a victim-victim.
In DDoS attacks, the scale is far greater, as they are based on hundreds of thousands of devices. Several major DDoS attacks and can drop entire data centers with multiple servers.
A short story
The first DoS attacks were observed in the 1990s and they simply exploited software bugs and weaknesses. They were meant to disable individual servers and services.
Over the past 20 years, this kind of action has grown to a significant extent. This helped advanced networking tools as well as reduced service costs that can be used in a DDoS attack.
Victims of such attacks have fallen into big companies from the beginning of 2000 to today, such as CNN, Amazon, Yahoo, eBay, Sony, Facebook, Twitter, and even the FBI site, among others.
Historically, the biggest DDoS attack that has been recorded so far has been made on October 21, 2016.
The victim was Dyn, which controls most of the Domain Name System (DNS) infrastructure on the Internet. This case had an impact on countless websites worldwide, which were based on Dyn's DNS servers.

The volume of data that managed to kneel the server may have exceeded 1.2Tbps (Terabit per second, trillion bits per second).
This size was made possible by using a botnet called Mirai.
Botnet: the main weapon for launching a DDoS attack
No matter how weird, a DDoS attack works on the same basic principle as taxation and charity.
What's Easier? A person to donate 1,000,000 euros, or 1,000,000 people to give out 1 euro?
If some people want to attack a large server, it is not enough to send requests from five or ten computers at the same time. It takes thousands or even hundreds of thousands of computers. Nowadays, this is possible with the use of a botnet.
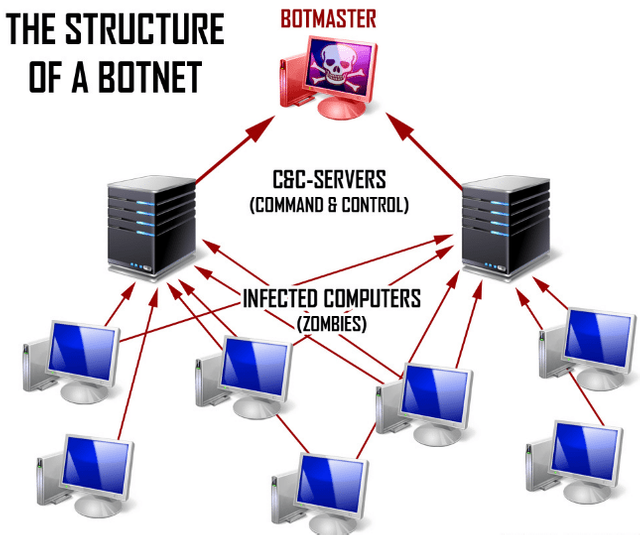
The logic of the botnet is simple. First, a trojan malware infects a number of computers. The trojan may come from infected email attachments, broken programs, infected websites, or from anywhere else.
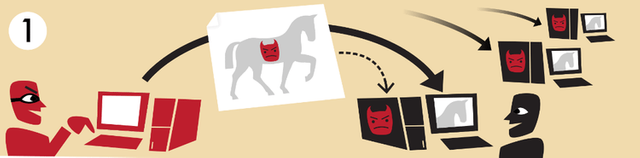
The more computers managed to infect the trojan, the more powerful the botnet.
Of course, the owners of infected computers do not know how their system is infected. The trojan used for the botnet avoids attracting attention, such as showing ads or destroying data.
The infected computers are called "zombie," as the trojan can take full control of the computer when needed.
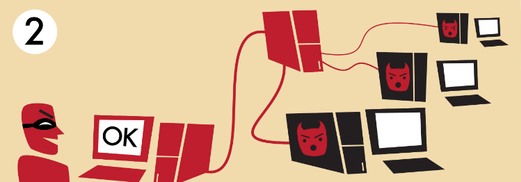
It is worth noting that those who create the botnet and those who use it are not necessarily the same people.
Often a team of hackers has created a botnet and then rents its use to third parties.

Beyond that, the botnet can do whatever the user wants. It can put any computer to send some spam emails to send tens of millions of advertising messages globally.
Naturally, botnets are not limited to email, they can send messages on Facebook or Twitter, comments on web pages, or whatever else is needed.
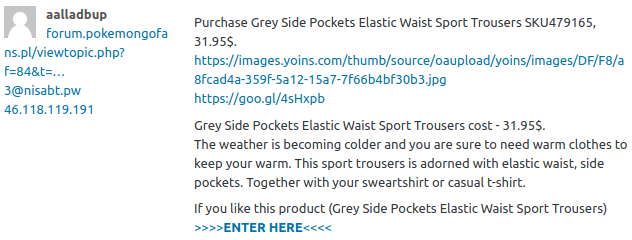
And, to get back to our point, botnet computers can launch a DDoS attack.
Especially in the attack on Dyn, the Mirai botnet had an innovation. Instead of infecting computers, he used security gaps in "Internet of Things" devices.
Internet of Things (IoT) devices are cameras, thermostats, and refrigerators that have internet access.

Mirai allegedly took control of more than 150,000 such devices and used them for the attack.

Types of DDoS attacks
The types of DDoS attacks are too many, and we can not analyze them all in this guide.

But what we can do is show you the four main types of DDoS attacks, on which many other types of attacks are based.
Below are terms such as triple handshake (SYN, SYN-ACK, ACK), TCP, ICMP, etc., which we will not analyze, since a separate driver needs to be understood.
SYN Flood (SYN Cataclysm)
This type of attack is based on the basic principles of the network communication function. Numerous TCP / SYN connection requests are sent to the server at such a rate that they can not handle all of them.
The server, upon receipt of the packet, creates a connection to communicate with the customer and awaits confirmation.
SYN Flood attacks abuse this mechanism, and never send the confirmation awaiting the server.
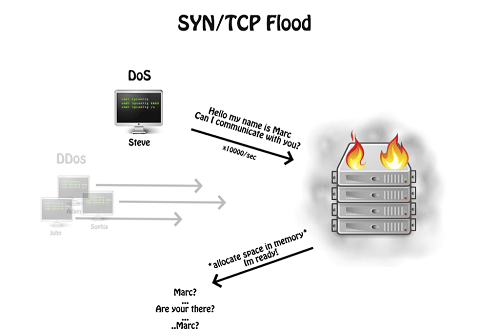
In this way, all new connections are reduced and legitimate users are virtually disconnected from accessing the server.
Connection Flood (Connection Cataclysm)
Here is a huge number of empty links on the server. Essentially, packages are needed only to establish the triple handshake (SYN, SYN-ACK, ACK) without transferring the data.
The goal is to create a large number of real links, derived from real IP, by devouring the backlog capacity on the targeted server.
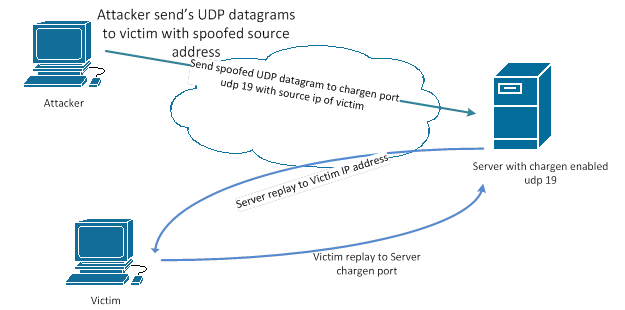
UDP Flood
The purpose of this attack is to exhaust the bandwidth or else the bandwidth. To do this, it uses the UDP (User Datagram Protocol) networking protocol, through which it sends a large number of packets.
Typically, these packets are sent from IP addresses with a fake source. Thus, the bandwidth of links decreases, rendering the server inaccessible to users.
HTTP Flood
HTTP attacks aim to overload the server, and eventually exhaust the hardware that is available.
Sometimes they lead to physical destruction of server hardware due to the inability to cope with CPU overload and RAM.
Why are DDoS attacks so popular?
A DDoS attack is at the same time "easy" and extremely effective. As mentioned before, there is ready botnet for anyone who wants to hire their use. We will find such services on Deep Web.
This means you do not need someone to be a talented hacker or even have any special knowledge around the networks.
In theory, one can rent a ready botnet and a DDoS attack as a service, costing a few thousand dollars.

Of course, the cost depends on the size of the botnet, and the size required depends on the target of the DDoS attack.
A botnet of 50,000 devices is not going to throw up Facebook, which its server can handle over 1 billion users online at the same time.
With a large botnet, however, and given that each device generates multiple charges from an individual user, even larger websites can kneel for a while.
Also, these attacks are an easy way for the attackers to show their anger and disapproval over a subject.

Many times they use the DDoS attack as a way to criticize the company or government organization for the appearance of unwanted political or geopolitical, economic or monetary behaviors.
How are big businesses protected from these attacks?
A DDoS attack can cause significant problems for a company. These are mainly economic as their site ceases to work for as long as the attack lasts. Also, not running a website is a blow to its credibility.
For this reason, each company must take some measures to guard against these attacks.

The most prevalent way of protection is through the use of specialized network security products and network applications.
These are systems that interfere with visitors and the digital services offered by companies. These products have deterrent and tracking mechanisms for a DDoS attack, as well as countermeasures.
Thus, they can see when the use of digital service is normal and when malicious, preventing the latter from disrupting the first.
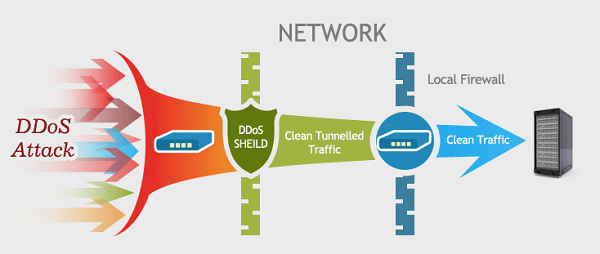
Obviously no protection system can prevent every attack without exception.
As in any other area of online security, malicious users and security researchers are working incessantly, improving their respective methods.
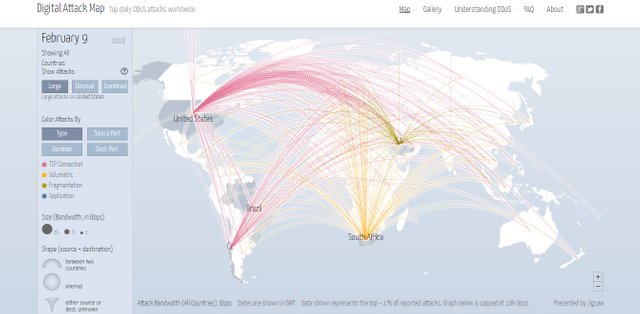
Watch live the main DDoS attacks right now
The Digital Attack Map page tracks daily the most important DDoS attacks worldwide.
Follow and upvote: @andrewclk
Twitter: https://twitter.com/ishere_andrew