BEAM - a scalable blockchain that ensures privacy of users

Introduction:
I am very sure that when Satoshi Nakamoto first thought about implementing the first peer to peer electronic cash system, in the form of the bitcoin blockchain, he/she might not have accounted for other projects been based on the blockcahin. Today, different blockchain projects exists, and these projects proffer solutions to different issues that exists in different sectors.
However, since the first blockchain was based on finance, it is safe to assume that the main use of blockchain is to ensure the secure, safe and private storage of finance. However, we should ask ourselves this question. Does the blockchain really provide a private method of storing funds? Let’s take a look at how the bitcoin blockchain works, since the bitcoin blockchain is what most blockchain copy.
The Bitcoin blockchain represents a user’s balance by a series of transactions, and these transactions could be traced back to the very beginning of a blockchain. The bitcoin nodes and miners have the main function of proving the validity of each transaction, this is to ensure that no central entity is brought into the system. Before a transaction is approved, all the parties involved must reach a consensus (agree), and this consensus is reached without trusting one another. The workings of the bitcoin blockchain is enviable in all manners, except in the term of privacy.
The very first time I heard about bitcoin, I believed that financial transactions done in the bitcoin network were private and anonymous, since, for every financial transaction, random private and public key pairs were generated, and then the random public key generated was used to form an address that would be used to receive and control the transaction, with the transaction and it’s details transparently and permanently stored on a public ledger. However, I was wrong.
After various of my personal research, I found out that due to data leaks from various parties, such as exchanges, merchants, OTC deals and even just by assembling the blockchain data, anonymity of users can be uncovered. Recall that I made mention that transactions and their details are stored on a public ledger in a transparent and permanent manner. Thus, once the user identity is uncovered, all past, present and future transactions can be tracked and monitored.
The lack of privacy while using the bitcoin blockhain is a big problem, as users could be attacked at anytime. I prefer that details of my transactions should be private to me, and only shown to those that I authorize. If you feel the same way, then come lets discuss BEAM:

BEAM:
BEAM is a platform that enables the true anonymous storage of values. BEAM has all the enviable workings of bitcoin, however with BEAM, privacy is completely guaranteed. Before we launch ourselves into the workings of BEAM, let us look at the MimbleWimble protocol, the protocol, which BEAM is based on.

MimbleWimble Protocol:
This is a new protocol that was published in august 2016, by an anonymous author. This protocol gives a smart way of achieving a truly private and confidential blockchain. This protocol is known as MimbleWimble. The name MimbleWimble was gotten from a spell in the Harry Porter books. MimbleWimble is based on two concepts, viz-a-viz, Confidential Transactions and Transaction Cut – through. These concepts were originally proposed by Greg Maxwell.
Confidential Transactions:
These are implemented via cryptographic commitment scheme. The cryptographic commitment scheme has two fundamental features, which are hiding and binding. For us to understand these features, let’s use a case scenario. Imagine, you give your 11 year old daughter a closed box containing chocolates, that she can only open on her birthday. When her birthday comes, you then give her the key to open the box, to show that your commitment to her is valid (binding), while she doesn’t know that the box contains her favorite chocolate until she receives the key and opens the box (hiding).
Transaction Cut – Through:
A blockchain consists of different blocks, and in turn each block consists of a series of transactions, each transaction has its own respective inputs and outputs. Thus, a block can be considered as a big transaction to be “cut through”. This means, the unification of all intermediate outputs that exist in a block. When this principle is applied to the entire blockchain, (i.e unifying all the unified outputs of each respective blocks), we get a system that only needs current state of transactions rather than the entire history of transactions as they had happened (bitcoin workings).
With the MimbleWimble protocol, unspent transaction outputs (transaction that is received by a user but still on the blockchain) can only be proved to belong to a specific user through the values of the message and the binding factor.
Once the transaction is created, the address of the users or the amounts exchanged is not stored on the blockhain, instead, only the commitment is stored on the blockchain. Thus, the amount of data to be stored and verified is small, and this allows MimbleWimble to work faster with smaller blocks.

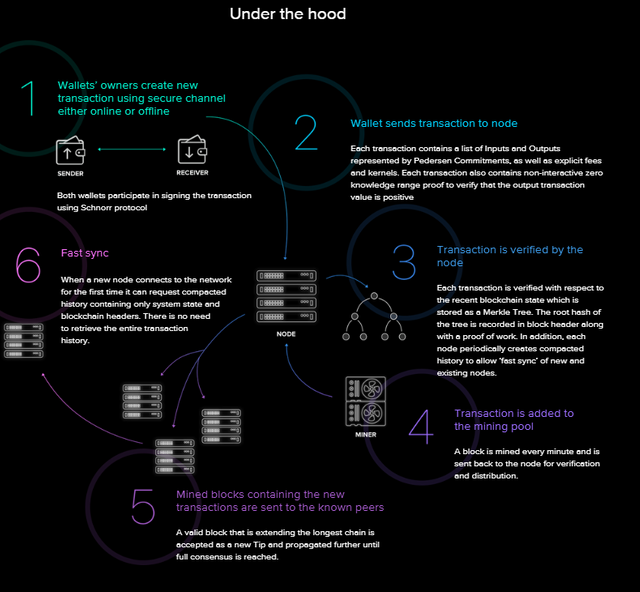
BEAM:
BEAM is built on MimbleWimble, and thus, BEAM has the following characteristics:
User in Control:
User decide the information that would be available, and to which parties these information are available to. Thus, the user is in complete control. The benefit of this is that, only trusted parties are privy to information of users, thus users are safe.
High end performance and Scalability at an enviable level:
With the “cut-through” property of the MimbleWimble protocol, excessive computational costs is avoided, since, , instead of proving that W->X->Y->Z, users can BEAM X->Z.
Sustainability:
The BEAM project is open sourced, and it would be completely implemented using the C++ programming language. 20% of block mining rewards would go to the BEAM Growth Pool (which backs the BEAM community) to incentivize the development and promotion of BEAM.
Usability:
BEAM has a dashboard that enables the effective and efficient management of budget. This dashboard also features actionable spend and earning insights.
Compatibility:
BEAM uses the equihash pow algorithm. This is to ensure that existing miners using GPU can adopt the BEAM project. Attached with the Equihash, are sets of tools that would be used to effectively run and manage mining nodes.
True privacy:
With BEAM, only the commitment are stored on the blockchain. The addresses of users and amount are not stored on the blockchian. Indeed, this is true privacy.
Versatility:
BEAM supports multiple transaction types, such as escrow, time locked transactions, atomic swaps, etc. This is due to the “Scriptless Script” technology.

Use Case:
Case 1:
Bimbo is a business man that values his privacy. He wants to invest bitcoins into a blockchain based charity organization. However, he wants to do it anonymously, to avoid unwanted attention. He is introduced to BEAM, and regardless the amount of donations he makes to this charity organization, his address is not stored publicy, and thus, his privacy is maintained.
Case 2:
Boden likes to use escrow in his business transactions. He has been doing it for a while, however, the address of his wallet is stored publicly on the blockchain, thus his identity could be traced. He gets to know about BEAM, and discovers that he can use escrow in his business transactions while the address of his wallet are kept private.

Applications:
Some application of BEAM includes:
- Finance industry, to ensure exchange of funds in a private manner
- Companies, to pay their employees, while maintaining privacy of everyone involved
- ICOs, to ensure that investors are granted privacy, etc.
Conclusion:
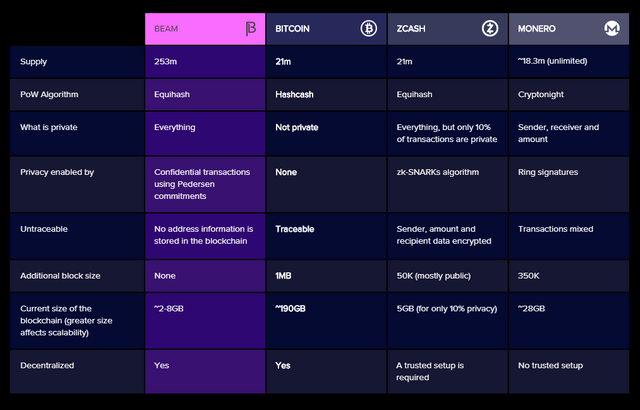
We have seen the features of the MimbleWimble protocol, which ensures privacy at a high level. BEAM is a project based on the MimbleWimble protocol, and thus, BEAM uses the properties of the MimbleWimble protocol to ensure the privacy of users when funds are sent and received. Infact, check the image below that shows the comparison of BEAM with other blockchains.
The opportunities which BEAM poses can never be overemphasized and BEAM should be adopted by users that rely on privacy to do their day to day business.
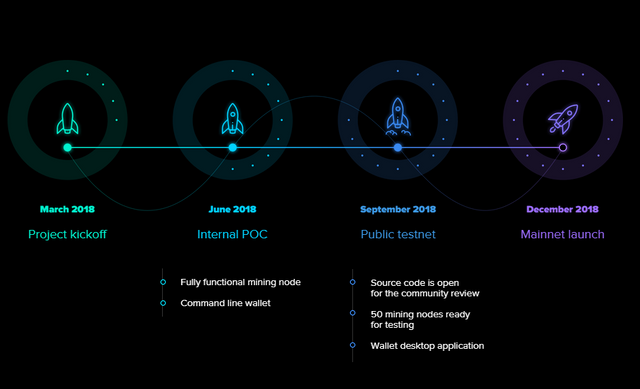
BEAM Roadmap:
BEAM Leadership Team:
BEAM Engineering Team:
BEAM Advisors Team:
BEAM Investors:
Check out this video:

This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Hello! I find your post valuable for the wafrica community! Thanks for the great post! We encourage and support quality contents and projects from the West African region.
Do you have a suggestion, concern or want to appear as a guest author on WAfrica, join our discord server and discuss with a member of our curation team.
Don't forget to join us every Sunday by 20:30GMT for our Sunday WAFRO party on our discord channel. Thank you.