Do YOU have 2FA enabled? Do you use a password manager? The convenience of cutting these corners is NOT worth the risk!
This public service announcement is a reminder to stay safe when you crypto! I know many of you have heard this all before, I know I certainly have - but then the other day I witnessed an attempted crypto-heist in the flesh, so I feel it's worth saying it again in case anyone missed the memo.

The other day I met up with an acquaintance of mine who is a miner, to have drinks and chat crypto. We only met recently, and hadn't had much time to talk tech until .then. Also, I was looking to sell some USD, so naturally we had our computers with us.
A little bit of background: the individual I was meeting up with only got into crypto because it can be mined. In some ways, he might almos bet a caricature of what "chinese miners" are described as: he doesn't keep up with tech, he's not a technology enthusiast (other than crypto), he got involved because he can buy these machines that generate money as long as you keep them online.
He was also using an exchange as his wallet (for some cryptoassets), as not all cryptoassets have light wallets and some assets get acquired speculatively in quantities where its hard to justify the installation of a dedicated wallet for each one. I understand the line of reasoning, but I find it to be a path of least resistance that can be quite dangerous to follow.
When he fired up his browser, he immediately got a notification from his email about emails from Bittrex. I hear him say "Wtf? Someone's trying to withdraw my coins!" when he opens his email, and indeed, he has withdrawals awaiting approval in his email that he did not initiate.
While he cancelled the withdraw requests, and changed his password on the exchange account, while my mind immediately jumped to attack vectors. How did this happen? The thought that it was a targeted attack because he is a miner crossed my mind, but didn't have much in support of it. It didn't seem likely that his PC was compromised/keylogged, or his exchange account would have been emptied for sure - but the attacker appeared thwarted by email 2FA.
The attack vector we determined was password reuse across multiple sites. He had used the same password on his the exchange as on various cryptocurrency oriented forums - which have disproportionately large targets painted on them for this very reason. One of the forums probably stored passwords insecurely (plaintext, or hashed without a salt), was hacked, giving attackers a DB of email addresses + passwords. From there, an attacker need only try the combination on exchanges.
My friend was very lucky on two counts - he didn't have the same password on his email and the attacker didn't have enough time, since the withdrawal attempts were discovered only 10-15 minutes after they were initiated. Given more time, the attacker could have run a background check (based on the KYC info in the exchange account), used the information from that to guess secret question answers, and reset his email password that way.
The way to protect yourself from the password reuse attack vector is by having a unique password for each and every online account. This can be accomplished by using a password manager, so instead of having to remember each and every password, you have one master passphrase which is necessary to decrypt your database of saved passwords. If you need to synchronize across multiple devices, as long as your master passphrase is strong, the password database can safely be stored in Dropbox/Google Drive. If you prefer to avoid sharing the encrypted DB with any 3rd parties, syncthing can be used.
I recommend KeePass or KeePassX 2 for a password manager. There are browser addons to allow autofilling of login information, but I would think twice about using those: is it really a good idea to give the software you use for executing untrusted code (your browser) direct access to the database of all your shared passwords?
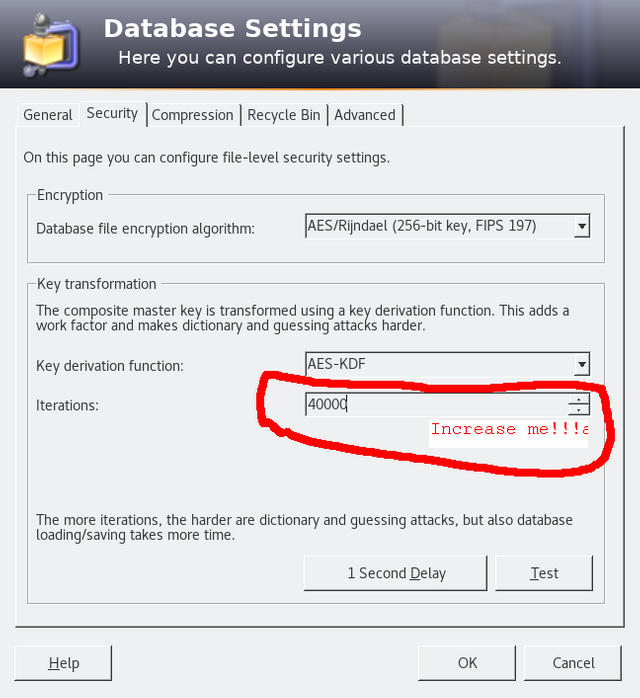
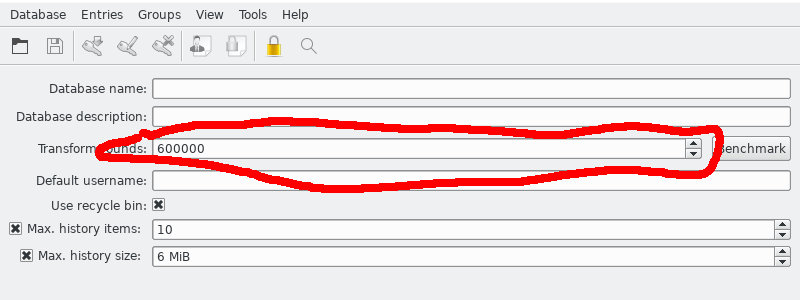
Create a strong a pass-phrase for your password database. Then, go to File->Database settings (in KeePass2) or Database->Database settings (in KeePassX2), and increase the number of Itirations/Transform rounds. This will increase the amount of operations it takes to derive the DB's master keys from the password, making it much harder to decrypt via brute force attack.
KeePass2
KeePassX2
Then, every time you log in to an online account, you need to systematically start changing the passwords, replacing them wit ones randomly generated with KeePass.
It is also of critical importance to enable 2FA on every cryptocurrency-related account where it is available, including email accounts associated with any logins. Google Authenticator is considerably more secure than Authy, but you have to make sure to write down 2FA secrets, as you will be locked out of your accounts without them if you lose your phone (or it breaks).
SMS-based 2FA is NOT secure, and should not be used. It is far too easy for an attacker to socially engineer the phone company into giving them control of your phone number.
tl;dr Enable 2FA everywhere it's available and use a password manager, unless you want to make it easy for thieves to steal your hard-earned crypto. Don't use exchanges as wallets. Get a hardware wallet if its cost is <%10 of the value of the crypto you are holding and need to protect. Use traditionaly cold storage if you don't want to fork over the bitcents for a HW wallet. Don't become a statistic.
I wish there was a way to enable 2FA here on Steemit. I understand it's complicated to do for posting and voting but for transfers it should be mandatory!
It's non-trivial to do so because the only way the chain currently verifies a transaction's validity is by checking the digital signatures on the tx. While creating a 2FA mechanism for transfers on the steemit.com frontend interface would be easy it would in no way thwart an attacker who got control of an accounts private keys (they could just import the keys into cli_wallet and empty an account that way), without major changes to the backend. In order for a meaningful improvement in security, 2FA capability would have to be baked in to the STEEM blockchain. It's possible we'll see the addition of such a feature in a future hardfork someday.
IMO, hardware wallet support would do considerably more to ensure safety of high value accounts. I'm hoping
that once the BitShares Munich devs finish coding Ledger support for BTS it might get ported to STEEM.
In the meantime what you can do is only perform transfer operations from a trusted device. On all other devices, log in with your posting private key in WIF format, rather than your password. It's also best practice to log in to various applications built on STEEM (ie. ChainBB for STEEM) with your posting private key, rather than your password.
Good Stuff man I try to tell people all the time there is no such thing as 2 safe. double fire. offline/cold storage as much as possible. Resteemit this and the keepass is the best!
I still struggle to believe anyone uses exchanges to store large amounts. Its not just the attack vectors but we have seen several exchanges disappear and another one looking like its on the verge of doing so. 2FA is also definitely the future.
Exchanges have been hacked too. There were many who reasoned "I'm not a security expert, I'll probably be safer if I entrust Mt.Gox with storing my coins, since they obviously know what they're doing" and lost everything as a result.
Personally, I find it absolutely mind boggling that a majority of exchanges allow users to make deposits and trade without enabling 2FA first. So many thefts could be prevented if more exchanges dared to inconvenience their users by requiring 2FA to be enabled as a prerequisite for doing anything else.
Great post, but I have 1 question I hope you could answer.
What if you lose your phone with the 2FA on it? Is it easy to recover it?
If you are on android there is an, currently unreleased but usable, 2FA generator called "andOTP". In contrast to the mentioned Google Authenticator you can backup the entries with a strong password in an encrypted file. If you lost your phone you can install the app and restore it with the encrypted file. But don't forget the password :)
The app is available on the playstore and as well in the F-Droid store. If you are deeper in programming android or even java you can read the sourcecode on github as well or compile it on your own.
https://play.google.com/store/apps/details?id=org.shadowice.flocke.andotp
https://f-droid.org/packages/org.shadowice.flocke.andotp/
https://github.com/flocke/andOTP
If you are using Authy, it backs up your keys on their servers - but this is less secure for obvious reasons.
For Google Authenticator, you need to back up the key when you set it up. Unless your phone is rooted, you have to make a backup of the QR code that you scan with your phone, or better yet, write down key provided along with the QR code. On a rooted device, you can simply back Google Authenticator up with Titanium Backup (just make sure to backup your Titanium Backup folder to a device other than your phone, and be sure to encrypt the backup since the authenticator secret keys are backed up in cleartext).plain
it is not always easy like Bittrex gives 7 day trade ban on 2FA key recovery request and bitfinex also block ur activities for some time and u need to have SMS recovery.
If it was easy to reset a 2FA token at an exchange, it wouldn't offer any added security. You can avoid having to go through the process if you back up the 2FA secret when you set it up (it's encoded in the QR code you have to scan, and is generally provided in plain text along with the QR code).
Using last pass with 2FA is the best thing you can do!
It safes time and your ass, because your security will be TOP.
I'm going to go ahead and urge everyone not to use LastPass. They have been compromised in the past. With KeePass (even if you're using DropBox to sync multiple devices) the amount of surface area you leave exposed to possible attacks is way lower than with a service like LastPass - which is known to be a central location for login credentials of countless users.
I don't deny that LastPass has certain features with are a convenient, such as sharing login details for a specific account with other LastPass users, but you're trading convenience for security, which in the big picture has far too much in common with trading liberty for security: those who do it deserve neither, and will probably lose both.
If you have a Yubikey/Nitrokey or similar, it is possible to use it for 2FA in KeePass.
Only security questions where leaked. Im not concerned about that. My questions are worthless for attacker.
Of I lose some security for ease of use, but still....I think lastpass with 2FA brings me 99.99% of security I can get. Just having different uncrackable pass on each site improves my sec drasticaly.
I feel really secure against automated hacks (my email was compromised 2 times) and against targeted attack (jsut me) im hopeless anyways.
Given that a KeePass database can be safely stored in DropBox/GDrive (as long as it has a strong passphrase protecting it), the same level of convenience that is provided by LastPass can easily be achieved with a much smaller exploitable surface area.
Does it autofill logins? Generate random passwords for me? Does it store memos?
It has an autotype feature. It generates passwords according to user-defined specs. There are plugins to enable autofill in browsers (this feature is a plugin because of the security implications of granting the browser access to the password database).It automatically wipes the clipboard 15 seconds after you copy a password. It does store memos, and additionally has user defined data storage fields.
I used LastPass before I switched to KeePass. KeePass is feature complete, although it's not quite as a polished as LastPass (which shouldn't come as a surprise, since LastPass is a commercial product). Unlike LastPass, KeePass is open source, so its security can be audited by anyone. The only feature I'm aware of that LastPass has (or had when I used it) which is unavailable in KeePass (and made possible by the centralized nature of LastPass), is the ability to share login credentials to a specific site with other LastPass users.
Ok, thank you man. I will try to look into it closely and give it a try :)
I prefer Authy over Google Authenticator, saludos
It's more convenient, for sure, but the way it binds to a phone number is a rather large lapse in security for the same reason SMS 2FA is insecure. Unless the choice isn't offered, I always select Google Authenticator over Authy.
I have lots of exchanges 2FA keys , API keys, it is very difficult to manage sometimes when u write those. I simply use my older smart phone i just take a snapshot of webpages for future recovery and i make sure this phone is never going to be connected to internet and is password protected. It is like having a nano ledger or keep key in low budget. i hope it is easier to recover in case i lost my main phone.
This is a perfectly valid backup mechanism for 2FA keys, I would still write the 2FA keys down though (or have some additional backup mechanism). The flash memory on the phone you use could fail at any time.
Never forget that the golden rule for backups is
x=n-1, wherexis the number of copies of your data you have, andnis the number of independent storage devices you have copies stored on.Thats a quite important topic, thank you for telling us more about this. Your example was quite good, so it got more easier to understand the Problem. I although got the experience that KeePass is quite useful, you can even use it to generate passwords.
If you installed KeePass, don't forget to save the data of KeePass on a Stick or so, so the passwords are safe and protected before accidents like pc crash etc.
As long as you have as strong passphrase, the keepass DB can be safely sync'ed via cloud storage, since the data in it is encrypted. Alternatively, Syncthing can be used, allowing for cloud-less synchronization across multiple machines.
HOLLY COW! This is why I have not bought any cryptos yet. I want to know I am secure. Lots of security solvers have come out but I want to wait a little longer. I have come to the conclusion though, that keeping my wallet offline is the best solution. I am contemplating a stand alone computer that only gets turned on when I want to do transfers, paper wallet and/or flash drive. Actually I am thinking multiple. Like multiple wallets that I transfer through to my main storage. I know I know, this seems like overkill, but right now, it is the best I can come up with :O
You have just described how cold storage could be achieved in the old days - before hardware wallets existed.
For supported cryptos, a Trezor/Ledger will enable the same level of security as an offline computer used for signing transactions (which you would have to sneaker-net to an online computer in order to broadcast), with the convenience of creating transactions from an online device.
Great post! Everything is a dictionary length for tech. I love the old days where anyone trying to steal my cash was met with a pistol in face.
People have had BTC stolen the old fashioned way too.
Geeze!