Avalanche(AVA) FAQ - Part 2: The AVA Platform
Was so surprised at the amount of claps my last post got, thanks for overwhelming support on the last FAQ!
What is AVA?
AVA is a high-performance, scalable, customizable, and secure blockchain platform based on Avalanche Consensus. It targets three broad use cases:
- Building application-specific blockchains, spanning permissioned (private) and permissionless (public) deployments.
- Building and launching highly scalable and low latency decentralized applications.
- Building complex digital assets with custom rules, covenants, and riders. Also known as 'Smart Assets'.
2. How does the Avalanche consensus algorithm work?
Imagine if a network of trustless nodes that want to choose between two colors, say, blue or red. A node within the network will randomly select a number of nodes, and pose the question to them. The nodes chosen to be part of the sample group will return an answer with their chosen color to the questioning node. Using the responses from the sample group, the questioning node will be able to determine what color the network has chosen. Subsequently, every node in the network goes through the same process and in this way consensus is achieved within the network.
3. How will Avalanche deal with sybil attacks?
The main AVA subnet will be proof of stake based and will require validators to stake coins.
More information about staking can be read in the previous FAQ: https://medium.com/@CryptoResearcher5/avalanche-ava-faq-part-1-the-ava-token-and-governance-6318ca34e703
4. What makes the Avalanche consensus algorithm so revolutionary?
Avalanche is a new consensus algorithm used to achieve record breaking scalability and speed. Time to finality using PoS AVA rivals that of the fastest DPOS chains, but without the centralization. It achieves security, scalability, decentralization and an almost instant time tx confirmation time and an almost instant time tx confirmation time altogether which was previously thought to be impossible.
5. What are some statistics on Avalanche's performance compared to other major blockchains?
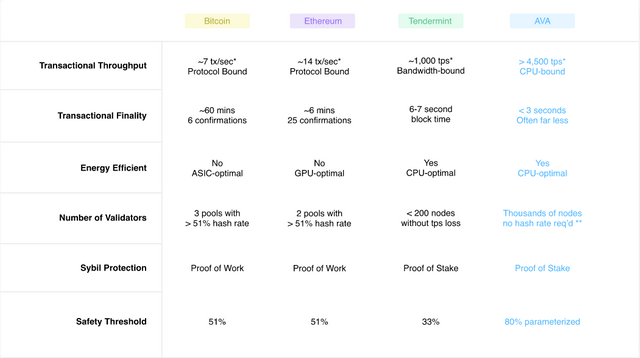
6. What is a safety threshold and what does it mean to have a parameterized safety threshold?
A safety threshold refers to the percentage of mining power or stake someone would need to have control of in order to attack the network. In Bitcoin, for example, in order to perform attacks such as double spending you would need to have the majority of the hash power (51% of all the hash power). However, Avalanche has introduced a revolutionary way to change this safety threshold to any value depending on what users want with different values having different trade-offs. At the moment, the main AVA chain will launch with a safety threshold of 80% parameterized parameterized.
7. Will AVA implement sharding?
AVA will use a different type of sharding referred to as functional sharding. The network will be split between by subnets which can be fully customised. For example, different subnets can have different virtual machines, different fee models, smart contract capabilities etc. Not only that, but the creation of new subnets will be extremely easy to do by following a few steps on their website.
8. What are subnets and what are the advantages of them?
Subnets are essentially networks that AVA validators can choose to also validate on-top of the main AVA chain. AVA can be split into many subnets all with unique features and widely different characteristics. This not only helps with scalability by distributing the workload of AVA to multiple chains - it allows AVA to adapt to changing market conditions much faster than other projects. AVA isn't limited to a single VM, it isn't limited to a single way to implement tokens, anyone who wants to can easily create their own subnet on top of AVA and implement the features they want to in order to create their specific ecosystem. Lastly, the fact that all subnets use the Avalanche consensus algorithm means that communication between subnets are easy to set up.
9. What is a chain?
Chains are a generic term for VM (short for virtual machine) instances. Each chain is assigned a ChainID and can be part of one and only one subnet. However, the same VM instance can be used to deploy the same type of chain multiple times within a subnet.
10. What features will the main AVA subnet have?
Every chain is part of a subnet. All but one subnet is optional for validators. The main non-optional subnet contains three chains:
- P-Chain (Platform Chain) - coordinates validators, keeps track of subnets and also allows people to create new subnets.
- C-Chain (Contract Chain) - a smart contract chain allowing for the creation of Ethereum compatible smart contracts that require total ordering. It uses the Snowman engine - an optimized consensus algorithm created by the AVA labs team to allow for high throughput smart contracts.
- X-Chain (Exchange Chain) - a super fast chain using Avalanche DAG allowing for the creation and exchange of assets between different addresses and subnets and also for decentralized applications that do not require total ordering.
All three of these chains make up the main, default AVA network and provide near endless possibilities. People can create DAOs on the C-Chain and simultaneously utilize the X-Chain to transfer assets at blazing fast speeds. This is an extremely clever and unique way to structure a ledger to allow for as much scalability and speed possible.
11. What's on the AVA roadmap?
Mainnet release - the mainnet should be released during July 2020.
Post Quantum VM - the concern with quantum computers is that they can break some of the currently deployed cryptographic protocols, specifically digital signatures. The AVA network model enables any number of VMs, so it supports a quantum-resistant virtual machine with a suitable digital signature mechanism. This is extremely important due to recent advances in the development of quantum computers and algorithms.
Pruning - Not much information is given as to how AVA plans to implement pruning at the moment. If you're unaware of what it is, it generally involves deleting or not requiring nodes to store old blockchain data in order to keep storage costs for nodes low.
Privacy VM - a virtual machine with privacy features could be extremely groundbreaking as many users and decentralized applications aren't too favorable about sharing everything about their AVA accounts/dapps.
To check out more on the AVA roadmap, check out:
avalabs.org/roadmap
Thanks for reading!
Hope you enjoyed. I try my best to keep these as short and sweet as possible so as to not bore you guys. If you have any extra questions, ask away in the comments and if I've made a mistake anywhere also please notify me so I can fix it. Stay tuned for the next FAQ!
Check out the AVA platform at: Avalabs.org
