How Deep Onion wallet aids anonymity by providing additional nodes over TOR
How deep onion wallet aids anonymity by providing additional nodes.
First to truly understand how a TOR Network works one has to understand how a non – TOR network works. In the current example we will take a simple act of web browsing (requesting google.com on your favorite browser), and see how data is transported currently.
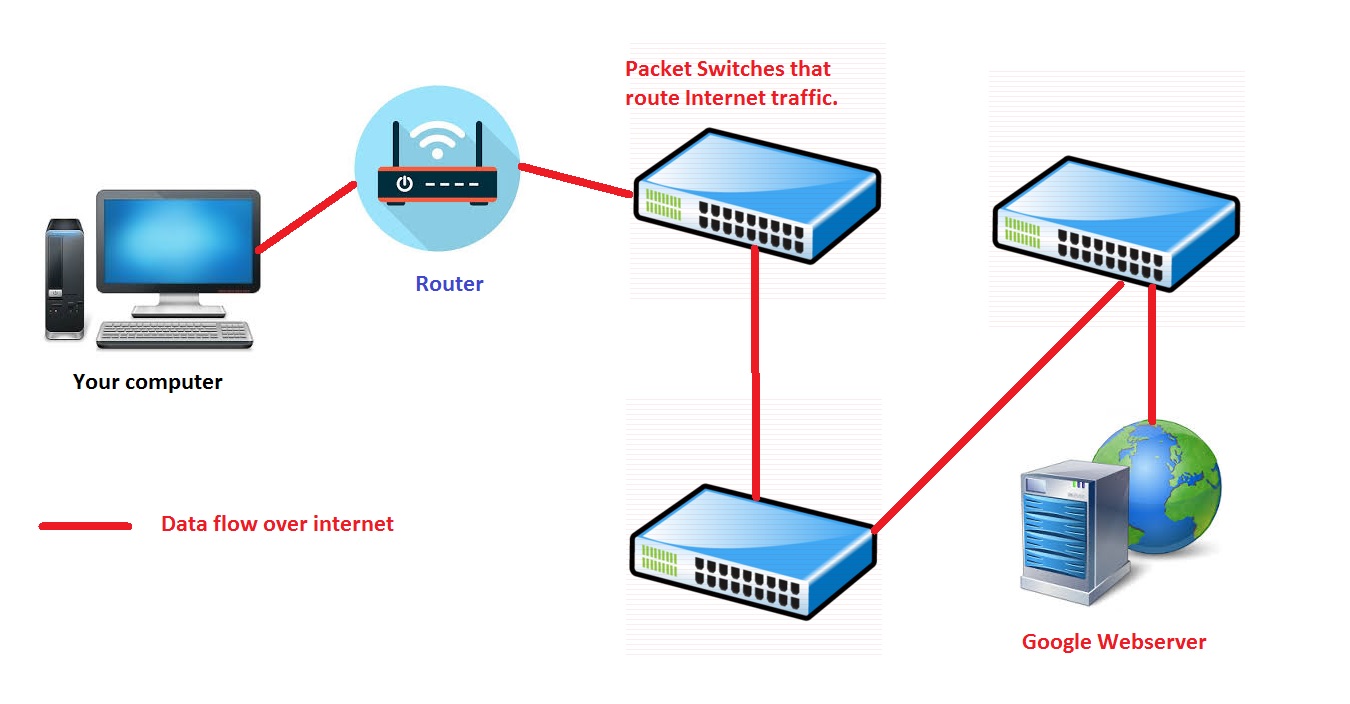
As you can see any of the switches/routers with simple packet sniffers on your request route can see few key things:
- Where the request is coming from (location/IP address few additional information regarding Operating system/internet provider/web browser version etc)
- What are you requesting from the server and from who, and if the data is not encrypted it can see passwords/email textual data/ video packets and additional sensitive stuff either sent or requested for that session.
Hence compromising your Anonymity.
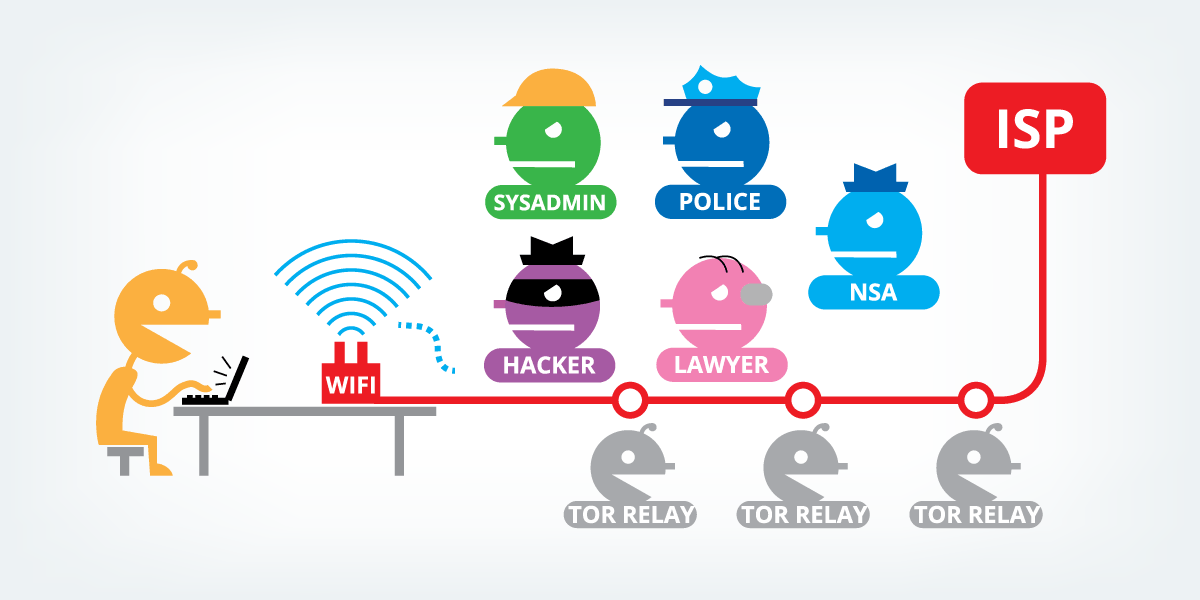
How does TOR Network works:
Here in the example let’s take a tor supported computer and Destination server, and see how TOR protects your anonymity and data.
First the Tor Protocol/browser finds something called an “Entry Node.” Entry Node is where your data will be entering the TOR secured network, between Your computer and “Entry Node” it will create a Tunnel using TLS (Transport Layer Security) which is very secure tunnel where no one can see in it and all the traffic is encrypted between the nodes let’s call it Session1 and the key they use to encrypt/decrypt data call it Key1
Now the “Entry Node” will find an additional Node let’s call it “Middle Node” and it will create a a secure connection using a NEW encryption key let’s call it Key2 between “Entry Node” and “Middle Node” and let’s call that Session2. In the Session2 all the data received from your computer will be encrypted using Key2.
Now the “Middle Node” will find an additional node let’s call it “Exit Node” (where your data will be exiting the tor network. The “Middle Node” will generate a Key3 and Session3 between itself and exit node. All the data transporting between them will be encrypted and secure.
Now the “exit Node” will send your request to its destination because all the data is encrypted by each node the receiving server is only aware that the request is coming from exit node.
Exit node is only aware that the request is coming from middle node and middle node is only aware of Entry node and Entry Node is aware of your computer but not the destination and Exit Node is aware of destination but not the origin and all the data request is encrypted in a Russian doll scenario or like an Onion. Providing your complete anonymity and security over TOR Network.
One of the key things to understand is we can have additional “Middle NODES” in each session, more “Middle Nodes” we have more secure a network is hence more people running TOR Nodes more relays can be added to route the traffic truly anonymizing it.
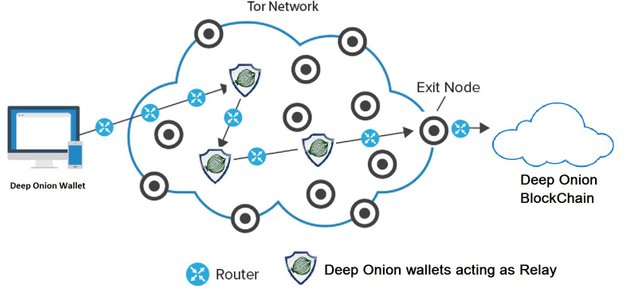
Using the Amazing Tor Network/protocol "DEEP ONION" completely revolutionizes Block-chain client connectivity.
Securing your transaction with deep anonymity, as number of DeepOnion nodes increases (brilliantly incentives by staking) it adds additional Nodes making the network where transactions are broadcasts securely and anonymously and the network more resilient.
If you like post, please follow and upvote!
Thank you!
followed you,if you like steemit tricks,please follow me...!!!
followed you as well. thank you.
thank you for the explanation i didnt know nothing about tor but now i know a littlte more. how it works DeepOnion is really amazing.
Congratulations @crypticj! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard!
Participate in the SteemitBoard World Cup Contest!
Collect World Cup badges and win free SBD
Support the Gold Sponsors of the contest: @good-karma and @lukestokes