Blockchain upgrades and their consequences
Blockchain’s hype seems to have smoothened for now.Nevertheless this year has been full of interesting developments, and fundamentals are getting stronger.Here just some of the improvements made and future upgrades of some of the most important blockchains.
Lightning Network (Bitcoin)
Lightning Network is now active, allowing low fees for the transactions in the Bitcoin network.
Excessive fees were creating doubts about the future and scalability of this blockchain, and this led to long debates and clashes.
The implementation of this second layer on the top of Bitcoin allows users to fulfill several transactions before settling them into the blockchain. In this way, users can now benefit from fast transactions and low fees, while still relying on the underlying network security.
Lightning network is possible through the creations of payment channels, in which both parties compromise to deposit an amount in a multi-signature wallet. Micro-payments are made off-chain and are settled periodically on the main chain, allowing less transactions to be recorded on the blockchain and boosting the network’s speed.
Payments can be routed through the Lightning Network, allowing user to benefit from channels that have already been opened.As long as there is a route that connects the two parties, a new channel does not have to be created between them in order to transact and benefit from Lightning Network.
Picture of Lightning network payment channels
Ethereum 2.0
Scalability is surely an important matter when it comes to blockchains.The reason is that blockchains are inefficient by design: every node needs to replicate the ledger in order to guarantee decentralization and security.
Blockchains face a trilemma, having to choose one of the following element to sacrifice in order to save the other two.
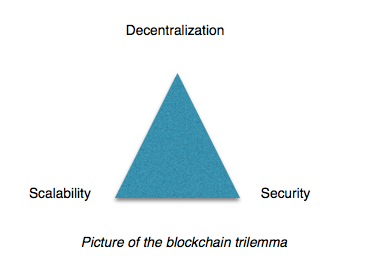
Ethereum is facing several changes in order to obtain a satisfying equilibrium.This important changes come with the Metropolis and Serenity upgrade. The coming hard forks are not expected to create new ethereum currencies, because the consensus on the changes is strong among the ethereum community.
The upgrades will consist in:
-Sharding
-Casper(Switch from PoW to PoS)
-Zk-Snarks
Also there are other solutions for the scaling problem, such as Plasma and Raiden
Sharding
Sharding allows to divide the network into pieces, allowing the nodes of the network to validate transactions only for the shard they are currently in.
Every shard is a subset of the network, in which validators just verify the transactions of that specific shard.Transactions are not required to be validated by the whole network, improving scalability.
In this way, Ethereum can manage to improve its scalability without excessively affecting decentralization or security.
In order to preserve the network security though, it is extremely important to prevent attackers to coordinate on being in the same shard.Several malicious nodes on the same shard would allow to cheat the network with a relatively small amount of resources, making attacks easier.
Validators are randomly assigned to shards, and they are required to reshuffle constantly.This mechanism prevents malicious validators to join the same shard and coordinate an attack.
The randomness through which validators are selected for every shard is extremely important: if the reshuffle of validator is not random enough, malicious actors could gather into the same shard and affect the network.
##Switch from PoW to PoS (Casper)
Consensus mechanism is an important element of blockchains.The way nodes agree on a single version of truth makes the differences in the decentralization, security and scalability of a blockchain.
Proof of Work has few problems that have to be faced: the high consumption of energy and the scaling problems. Let’s make a short recap about these two consensus mechanisms:
Proof of Work
In Proof of Work consensus mechanism validators are rewarded for the computational power spent to solve specific mathematic riddles, securing the network. This mechanism makes an attack on the network quite difficult, because the attacker would need to have the majority of computational power of the network in order to take control over it.
Proof of Work is just a way to make expensive for attackers to cheat the network, and the use of resources(electricity) is required to secure the network.
Through this mechanism, a malicious node would need to spend a high amount of resources to attack successfully the network.Everybody would notice that the network is under attack, and the attacker would end up with the control of a worthless currency.Using the same computational power to secure the network, instead of attacking it, would make the node to be rewarded.
With Proof of Work malicious actors are disincentivized to attack the network and they would need to acquire 51% of the network’s hashing power in order to control it.The cost of attacking the network is prohibitive, and nodes are incentivized to secure the network for a reward.
Proof of Stake
Proof of Stake is a consensus mechanism which requires validators to lock up some coins in order to validate the network transactions.If the validator behaves correctly, it is rewarded with a profit on its investment.If the validator tries to cheat the network, the investment is lost. In this way, an effort is needed to validate the network, and participants are prevented to cheat.The only way the network can be cheated is the case in which attackers own 51% of the value of the network.In any case, reordering the network after an attack in Proof of Stake is cheaper, creating an attack/defense asymmetry.
Through sharding, the network is divided in many pieces: it’s easier for malicious nodes to take over by coordinating the attack on a specific shard.An attacker would need a considerably smaller amount of hashing power to cheat the system, because he would just need to overtake the hashing power of the single shard.In a Proof of Work system, the attacker is required to own 51% of the network computational power, but with sharding the attacker just needs to gain a majority on the shard’s computational power.
In a sharded network a successful attack requires less effort, and malicious nodes can successfully attack the network with little resources.
There is technically no way to prevent malicious actors to concentrate their hashing power over the same shard.No mechanism can prevent nodes from using their computational power on a small piece of the network.
Instead, changing consensus mechanism to Proof of Stake, would allow the network to scale through the mechanism of Sharding.
This is possible because in Proof of Stake, nodes cannot choose which shard they are assigned to, preventing malicious nodes to coordinate an attack.A constant reshuffle between validators prevents the possibility of malicious actors to gather on the same shard.
This change from PoW to PoS will be made through an hybrid consensus, slowly becoming fully PoS.
Difficulty Bomb
Implementing new important changes on a trustless blockchain, requires an hard fork.This happens because if the new rules are not accepted by every node, the network splits.The nodes who run the old software will play by the old rules, and the nodes who upgrade their software will work on the new network.
When an hard fork occurs, miners can choose to mine on the old chain.In this case there could be a split, because a set of validators would keep working on maintaining the security of the old network if it is a more profitable activity.
In order to avoid a split, miners have to be disincentivized from keep mining ethereum in the old network. Instead, they should be incentivized in locking their funds in the blockchain that plays by the new rules, gaining the reward for securing the new system.
A mechanism called “difficulty bomb” is introduced in order to disincentivize miners to keep working on the old network.
The difficulty bomb makes incredibly difficult for nodes to mine ether, making the process expensive and not rewarding.In this way, miners don’t have any incentive to keep working on the chain that uses the old rules, and they would need to switch to the new consensus mechanism to gain profits from securing the network
Plasma
This layer consists in the creation of child-chains to perform most of the transaction. Childchains are secured to the main chain through smart contracts.Transactions can be performed on the child chains and periodically settled into the main chain through the smart contracts.State hashes of the child-chains are recorded, in order to settle the updates into the main-chain.
Child-chains would work with their own consensus, and users can exit plasma if the child-chain is attacked.
In this way, if problems are encountered, the user can show a proof and reclaim his balance from the smart contract stored in the main chain.
Plasma is still under development, but it is thought to be an effective off-chain scaling solution.
Raiden
Raiden is the ethereum version of Bitcoin’s lightning network.With few variation, it is an interesting off-chain solution that can allow micro-payments without affecting the network’s performance.Through the technology of state channels, users can exchange value routing their payments through already opened channels.
Zk-Snarks
Zero Knowledge Proof is the technology that allow to verify the correctness of an information without revealing the information itself.
Zk-Snarks allow to verify a computation building algebric circuits, perform a Lagrangian Interpolation and create polynomials that allow to verify the computation without revealing the inputs.
Zero Knowledge Proofs can be very useful in many sectors, including decentralized computing and AI development.
In order to improve, AI needs to be fed with huge amounts of data. It would be possible for AI models to improve from each other, without sharing sensitive data between them.
This is a very important achievement, because it allows organization to let their AI improve thanks to the data collected by other AIs but without having the ability to see the data, preserving privacy.
Another interesting technology is Zk-Starks.Differently from snarks, Starks do not require a trusted setup, but are in a earlier stage of development.
These are some of the important updates that the biggest blockchain network will have implemented.
Scaling blockchains is still a very debated topic, and it’s interesting to see in how many ways it can be faced.
References:
https://github.com/ethereum/wiki/wiki/Proof-of-Stake-FAQs
https://medium.com/@VitalikButerin/zk-snarks-under-the-hood-b33151a013f6
Congratulations @lucafra23! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Hello @lucafra23! This is a friendly reminder that you have 3000 Partiko Points unclaimed in your Partiko account!
Partiko is a fast and beautiful mobile app for Steem, and it’s the most popular Steem mobile app out there! Download Partiko using the link below and login using SteemConnect to claim your 3000 Partiko points! You can easily convert them into Steem token!
https://partiko.app/referral/partiko
Congratulations @lucafra23! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!