Deeponion always thinks about the security and privacy of its users
For many it is not new that Deeponion has been working on its improvements, and also on its updates, taking into account the needs of the user, as it provides greater privacy. Since Deeponion has a network tor, the project seeks to create a network of low latency distributed communications through the Internet layer so that the data of users who use it is never revealed, maintained, as well as a private network and anonymous
But for deeponion it is not enough; and for that reason the Tor browser includes some evasion tools to avoid these locks. These tools are called "connectable transports": OBFS4 and MEEK; in order to have the greatest security and anonymity possible. They are tools that Tor can use to camouflage the traffic it sends. This can be useful in situations where an Internet Service Provider (ISP) or other authority is actively blocking connections to the Tor network.

OBFS4 is an update of previous versions like Obsf3, obfs2 and others. That is why Obfs4 makes Tor traffic look random, like obfs3, and also prevents censors from finding network bridges by scanning the Internet. They are less likely to block obfs4 network bridges than obfs3 bridges. Although it is very similar to ScrambleSuit in its main design, it improves with the use of modern and high-speed elliptical curve cryptography instead of the UniformDH used in ScrambleSuit and obfs3, which allows it to have smaller, more secure and less expensive authenticated key from the computer point of view. When changing the link protocol. Ofs4 is a protocol hiding layer for TCP protocols. Its purpose is to prevent third parties from saying on the basis of the content of the message, what protocol is used. Obfs4 offers protection against active attackers that have obtained the server's node ID and public identity key. Obfs4 offers protection against some protocol fingerprints without content, specifically the size of the package, and optionally the package time. obfs4 provides integrity and confidentiality of the underlying traffic, and server authentication.
On the other hand, also counting on MEEK, which is a different approach, instead of trying to stop the discovery of points of entry in the Tor network, this makes it very difficult for an observer to distinguish between Tor traffic and the rest of the traffic. Given that powerful adversaries have been able to list large sets of bridges by various means, the possibility of having entry points that are not based on being unpublished is difficult to block provides an advantage. Through the use of content distribution networks, Tor can make his connections masquerade as a web request to a non-Tor resource to an external observer, while internally directing traffic to some server software that forwards traffic to the Tor network. . This makes it difficult for a censor to block only the traffic on the Tor network while allowing the other services behind the same CDN to continue unimpeded, essentially creating a situation where successful blocking would result in high collateral damage to resources not entirely related that would make it potentially costly and unpopular to block.
These are the most common connectable transports that are currently implemented, All these transports make it look like you are browsing one of the main websites instead of using Tor. meek-amazon makes it look like you're using Amazon Web Services; meek-azure makes it look like you're using a Microsoft website; and meek-google makes it look like you're using Google search.
How to use them:
First, download a Tor browser version with moderate capacity for your platform and language.
Verify the signature and run the package according to the instructions for Windows, OS X or GNU / Linux.
On the next screen, where it says Which of the following best describes your situation? , click on the Configure button
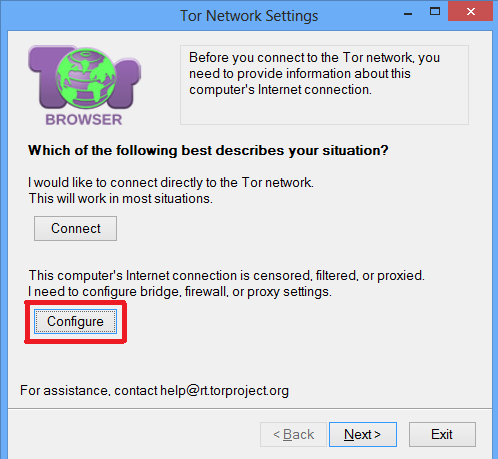
On the next screen that says Do you need this computer to use a proxy to access the Internet, answer No unless you know you need to use a proxy. Meek supports the use of an upstream proxy, but most users do not need it.
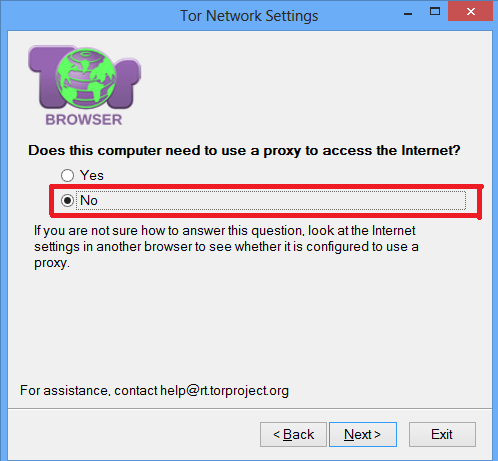
On the next screen that says "Does this computer's Internet connection go through a firewall that only allows connections to certain ports?", Say No. As HTTPS transport, the mansos only use the web ports, which are allowed by the majority of the firewalls.
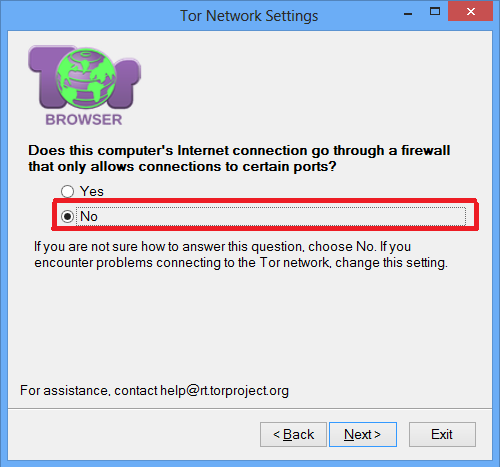
On the next screen that says: Block your Internet Service Provider (ISP) or censor connections to the Tor network ?, Say Yes. If you say Yes, it will take you to the screen to configure connectable transports.
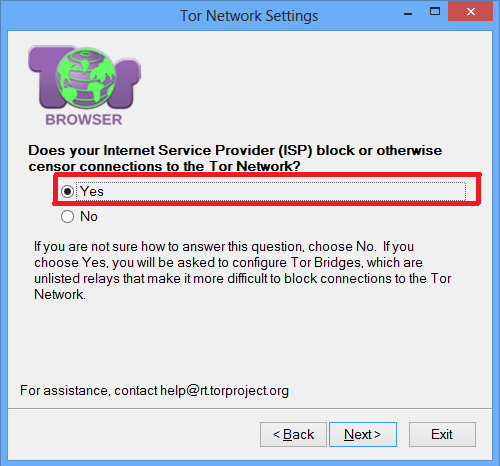
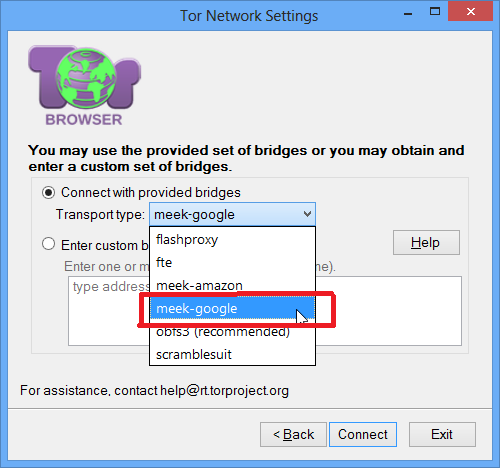
On the next plug-in transport screen, select Connect with provided jumpers and choose either meek-amazon or meek-google from the list. Probably the two will work for you, so choose what feels faster. If one of them does not work, try the other one. Then click on the Connect button
These have been one of the many advances that Deeponion has made weeks before the launch, we are still waiting for new things from this great project and there are still many things to develop, but there is no doubt that deeponion is already a competent project and that is how deeponion every day works to be number one. Having as a priority to guarantee the privacy and security of its users.