Learn hacking 1.01 Setting up the lab
Hi everyone,
In the previous post, I sent you the links to download Virtual box and Kali linux. In this article I want to help you set the lab up so you can test the techniques you will learn in a safe environment.
First, setting Virtual box.
You need to download the packages for your platform.
In Windows you just download and run the .exe
In Linux it will depend of your distribution. I recommend you google how to install it for your exact distribution. Here I want to show you Ubuntu because it's easy to use and quite popular. This video is a good tutorial to install virtual box (always check your linux version).
This is a small video for MAC OS. I never did install it on Mac OS so here is a small tutorial and I hope everything works fine!
Once you installed Virtual box, you will want to install the extension pack. You just download it and run it.
When virtual box is ready to go it will look like this:
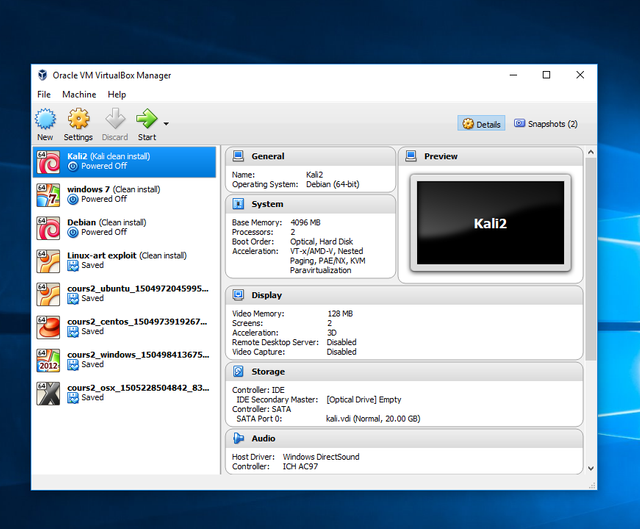
You can see all the machines I can run and my favorite one of course Kali Linux!
Second, we want the attacker machine, Kali Linux. This is a great detailed tutorial on how to install Kali in virtual box from blackmoreops.
https://www.blackmoreops.com/2014/04/08/detailed-guide-installing-kali-linux-on-virtualbox/
The only difference for me is that I put more RAM in it. They put around 1 Gig of RAM.
If you are like me and you hate slow stuff, if you have the resources on your computer, put more! Because I have 16 Gig of RAM, I did put 4 Gig of RAM in Kali! Just be sure your host machine still has enough RAM to function properly!
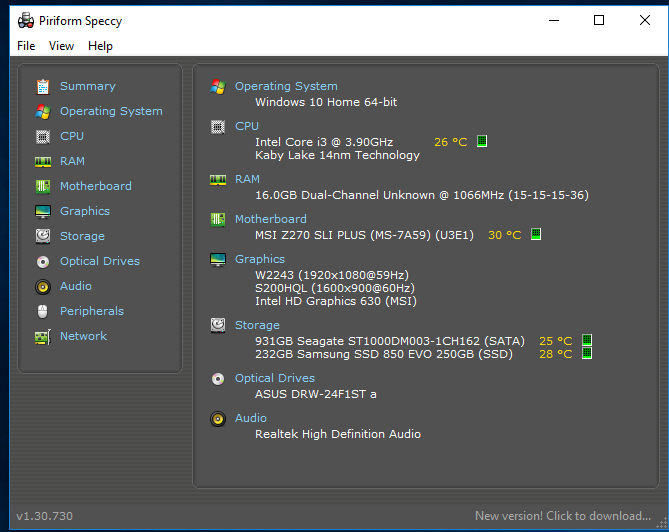
If you don't know how much RAM you have, I like to use a tool called Speccy. Go to https://www.piriform.com/speccy/download and get the free version. Install it, run it and you will know you computer specs!
After Kali is installed you will see it can't go full screen. You need to install virtual box guest additions! Follow this small tutorial:
https://docs.kali.org/general-use/kali-linux-virtual-box-guest
Third, we want a victim!
For my tutorials I will use the victim machine Metasploitable. You can download it from https://sourceforge.net/projects/metasploitable/
You then unzip it and run the file
Metasploitable.vmx
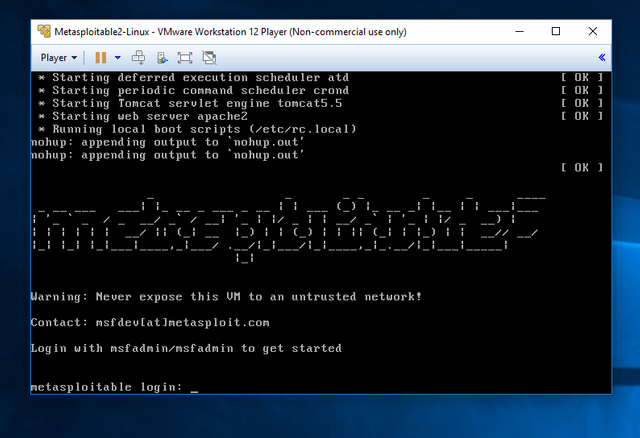
You should see the login panel
In conclusion, what we did was:
set up Virtual box to host machines
set up Kali linux as attacker machine
set up Metasploitable as victim machine
If you have any questions or something doesn't work, feel free to ask! Don't be afraid to google your error messages if you encounter some. It's normal and it practices your patience! Errors are always a good way to learn!
We are now ready to Start Hacking! Stay tuned for the next article!
The information provided on hacking is to be used for educational purpose only. The creator is in no way responsible for any misuse of the information provided. All the information provided is meant to help the reader develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage directly or indirectly. The word "Hacking" should be regarded as "Ethical hacking". You implement the information given at your own risk
Written with StackEdit.
What was the hardest for you to learn.
Its hard to say, when you learn, alot of things are new. The hardest part is keep learning when you don't always want or understand. Just keep reading, learning, trying new things and eventually you will find it easy! The hardest is to keep the focus!
Very Instructive.
I'm glad you like it!
This post recieved an upvote from minnowpond. If you would like to recieve upvotes from minnowpond on all your posts, simply FOLLOW @minnowpond