Bad Rabbit ransomware: What to do

On October 24th observed notifications of mass attacks with ransomware called Bad Rabbit. It has been targeting organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:
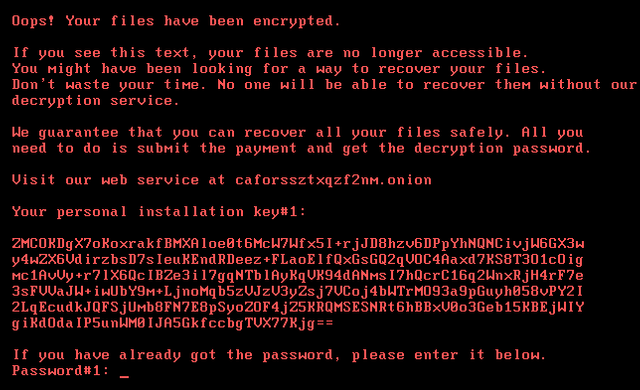
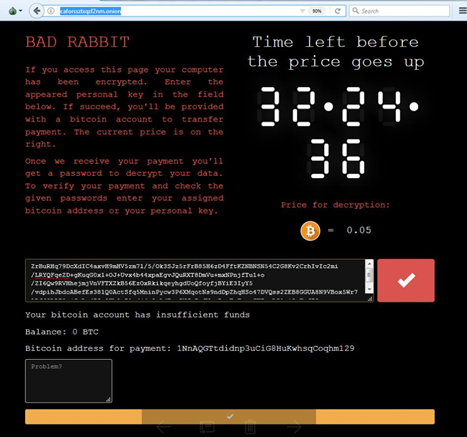
The ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer.
How does it infect users?
Bad Rabbit uses a typical watering hole attack. With several compromised sites it attempts to convince users to install a fake Flash installer. If clicked, the installer drops malicious files.
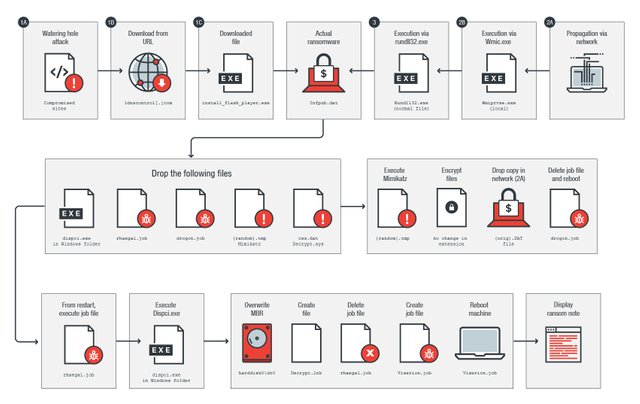
However, people in Ukraine, Turkey and Germany have also been affected.
Bad Rabbit is demanding 0.05 Bitcoin (£220) from victims – a fee that looks set to rise – in exchange for the restoration of their computers.
However, security experts always advise people against paying the ransom. This is because it encourages more attacks, and there's no guarantee the attackers will actually honour their word and remove the malware from your device.
How can you protect yourself?
Habitually back up files. Ransomware distributors gain leverage by encrypting files and threatening you with data loss. If you have backups of the affected files, the cybercriminal loses this leverage.
Keep your systems updated. Cybercriminals often take advantage of known exploits, but updates from vendors come out regularly and can protect users from many attacks.
The trick was discovered by security researcher Amit Serper who shared his tip on Twitter. Serper, who works at Cybereason, explains that all you need to do is create two files (c:\windows\infpub.dat and c:\windows\cscc.dat) and remove all permissions from them. This means that even if you come into contact with Bad Rabbit, it will not be able to work its magic.
https://twitter.com/0xAmit/status/922911491694694401/photo/1
This technique has been confirmed as working by other security researchers, but Kaspersky suggests disabling the WMI service to prevent the spread of Bad Rabbit over a network.
To do this, use the following steps:
This technique has been confirmed as working by other security researchers, but Kaspersky suggests disabling the WMI service to prevent the spread of Bad Rabbit over a network.
To do this, use the following steps:
- Press the Windows key and R simultaneously, type services.msc and press Enter.
- Locate the Windows Management Instrumentations entry, right click it and select Properties.
- Click the Stop button to stop the service, and from the Startup type drop-down menu select Disabled before clicking OK.