Crypto Academy / Season 3 / Week 6 - Homework Post for professor @stream4u

Question 1
What is Blockchain and What are the types of Blockchains / Explain in detail the types of Blockchain?
Blockchain
A Blockchain is comprised of digital records called Blocks, that is interconnected with each other, stored and secured such that once saved, it cannot be changed, hacked, or removed. The essential feature of a blockchain is that it is decentralized within the nodes connected to the network. This implies that when a cryptocurrency transaction is initiated, a duplicate of the transaction is made and distributed to all the connected nodes within the Blockchain. This is achieved with the use of Distributed Ledger Technology (DLT).
The security of a blockchain is engineered with a cryptographic function called Hash, which uses a one-way encryption function, that ensures that the hash of an input can not generate the input value. this implies that any changes made within a blockchain change the structure of the blockchain, and requires that the entire block will be re-mined.
A typical blockchain system is made of four essential components which include the following:
1- Block
Blocks are digital files that contain encrypted text data about the activities of a network. Once encrypted data is entered in a block, It cannot be removed, i.e it is permanently stored. A copy of the new data is made and sent out to all connecting nodes within the network, this maintains the decentralized nature of the Blockchain.
Any given block has three essential properties that are peculiar to the block. They are, Data stored in the block, A 32-bit number called nonce which is generated when a block is created, and a 256-bit set of alphanumeric characters that are unique, and called Hash.
2- Links (chain)
Every block within a network has a unique 256-bit Hash and Nonce number. Every new block contains the hash of the previous block (Link) that indicates the position of the block and maintains the blockchain's orderliness. This improves the accessibility of data stored within a blockchain.
3- Nodes
The nodes are computers connected within a blockchain that create, mine, and validate blocks. Every connected node gets an update on the current status of blocks i.e if a new block is created, every connected node gets the update of the current block with the number of transactions contained. This proves the decentralized nature of a Blockchain.
4- Miners
This refers to active members of a blockchain network that validates blocks and transactions through mining. Mining involves the process of using high-powered computers that perform the complex mathematical computation to validate the hash of a block.
Types of Blockchain
Blockchain technology has a wide range of use cases and can be adopted across many sectors depending on the type of blockchain and the use case. There are about four (4) types of blockchains. They include:
1- Public Blockchain
The is the type of blockchain adopted in the cryptocurrency ecosystem. It is a nonrestrictive blockchain that allows access to anyone to connect to its network through means of internet connection. This blockchain uses the distributed ledger technology to maintain the distribution of data stored within the Blockchain to every connected node.
A node can access all the blocks connected to the blockchain and details contained in them, , for instance,, the genesis block of Bitcoin created by Satoshi Nakamoto back in 2009 is still publicly available. Any node connected to a public blockchain can mine, verify the transactions contained within the network, using the agreed consensus algorithm (like proof-of-work and proof-of-stake).
Advantages of Public Blockchain
A- Transparency
This is one of the major advantages of the public blockchain because every information about a transaction is publicly available to anyone anywhere provided the user/node is connected to the network.
B- Security
The public blockchain is very secured. It uses the hash cryptographic function to maintain animosity of transactions and users of the chain network. It also uses the decentralized feature of blockchains to maintain multiple records of the same data across multiple connecting nodes.
C- Accessibility
A public blockchain is free and completely accessible to the general public, organizations, institutions, etc. for use. The blockchain network can be adopted in business and organizational use cases like payment of salaries, transfer of funds, etc.
Disadvantages of Public Blockchain
A- Scalability
With the increasing number of connected nodes to a blockchain network, congestion is experienced and the network is generally slow. This proves that blockchain technology is had to scale up to wider coverages.
B- Cost of Maintenance and Mining
Maintaining a public blockchain is expensive, with an increasing number of users, higher network bandwidth is required for faster data transmission. Also, mining in the public blockchain requires the use of high-powered computers to meet up with the time required to create a new block, which is an average of 10 minutes. This increases electricity costs and high transaction fees.
C- Attack Target
Public blockchains are usually attacked by hackers in other to control the activities of the blockchain. For instance, the 51% attack, where hackers aim to control at least 51% of the mining power of the blockchain.
2- Private Blockchain
A private blockchain is a small scaled blockchain that is restricted to the desired number of connecting nodes. This is similar to a private network where the resources are shared between the nodes connected to the network. In this type of blockchain, data of blocks and transactions are stored across the connected nodes to maintain accurate information about the blockchain network.
This type of network can be used in organizations, companies, banks, schools, etc. Where data can be stored and accessed by authorized nodes within the network. Usually created and managed by an individual or small group of persons.
Advantages of Private Blockchain
A- Access Control
Private blockchain allows access control of the network, where the individuals in charge of the blockchain determine the nodes to grant access to join the network.
B- Fast and Secured Network
A private blockchain is small-scaled, and this improves the speed of data transmission, verification, and storage. The limited access to the stored data improves the security of the private blockchain.
Disadvantages of Private Blockchain
A- Not Truly Decentralized
The core feature of a blockchain is its decentralized nature. That is not the case in a private blockchain, access is restricted to only a limited number of nodes.
B- No Animosity
In a private blockchain, every connecting node is known by the individuals managing the blockchain network. This compromises the animosity feature that a blockchain should have.
3- Hybrid Blockchain
The hybrid blockchain combines the features of public and private blockchain simultaneously. This is achieved by setting up a private blockchain that restricts access to data from authorized and non-connecting nodes. And joining a public blockchain network that allows connected nodes access to all stored data.
Smart contracts are used to manage the public blockchain connection, where transactions and block details can be verified publicly when required. Connected nodes within a hybrid network maintain their animosity, except when a transaction is performed by the node, where their identity is revealed. This type of blockchain can be used in hospital record systems etc.
Advantages of Hybrid Blockchain
A- Faster and Secured Network
The hybrid blockchain is fast and secured, access is still restricted to non-connected and authorize nodes within the blockchain. The reduced number of nodes allows for fast verification of transactions and duplication and storage of data to all connected nodes.
B- Cheap cost on Maintenance and Transaction
It is relatively cheap to maintain the hybrid blockchain network compared to the public blockchains. Verifying transactions is less expensive because less computation power is required.
Disadvantages of Hybrid Blockchain
A- Not Truly Decentralized
The hybrid blockchain is not truly decentralized, access restrictions exist within the Blockchain network and therefore are assumed to be less transparent.
4- Consortium Blockchain
The consortium blockchain is similar to a hybrid blockchain, where the blockchain has private and public blockchains running simultaneously, the major difference is that nodes from different consortium blockchains connect to verify transactions and blocks.
The nodes connected from different blockchains maintain the decentralized nature of consortium blockchain, serving as validators in the blockchain that can initiate, receive and verify a transaction, where other connected nodes can only initiate and receive transactions.
Advantages of Consortium Blockchain of
A- Fast and Secured Network
Similar to the hybrid blockchain, the consortium blockchain is secured and fast, the layered access control allows for easy access of data and verification of transactions.
B- Access to Multiple Blockchains
The consortium blockchain permits selected nodes within a blockchain to connect with other nodes from different blockchains in a decentralized way where details of transactions are updates across the selected nodes.
Disadvantages of Consortium Blockchain
A- Not Truly Decentralized
Similar to Hybrid and private blockchains, the consortium blockchain is not truly decentralized and transparent, access to certain data is still restricted.

Question 2
What are the benefits of blockchain?
Benefits Of Blockchains
Blockchain technology has some very impactful benefits and they include:
1- Data Decentralization
Distribution of data and transaction details contained in blocks, to all connected nodes of a blockchain, improves transparency and security. This adds an additional layer of security to the blockchain by duplicating block details across multiple nodes.
2- Immutability
Blockchain maintains the originality of data, once information is stored in a blockchain, it cannot be changed, or removed, date and time stamps are added to the information. This improves the rigid nature of blockchains.
3- Trust
The decentralized nature of blockchains encourages the buildup of trust between anonymous entities within a blockchain. The reliance on connected nodes within a blockchain for safe transfer and verification of blocks of transactions encourages more blockchain users.
4- Security
The adoption of blockchain technology in different sectors improves the security layers. The immutability of blockchain and its decentralized nature allows for robust security. Other security benefits include the use of cryptographic functions and encryptions to protect data within a blockchain is an added advantage to the system.
5- Reduced Cost
The cost of performing an international transaction using cryptocurrency is relatively cheaper than the traditional centralized bank international transfer. This is a very good benefit of blockchain technology because it encourages individual involvement in investment and trading of cryptocurrencies.

Question 3
Explain Blockchain Distributed ledger.
Blockchain Distributed Ledger
The distributed ledger in blockchain technology forms the basis of its decentralization. This is the distribution of data and transactions recorded contained in blocks, to all authorized and connected nodes within the blockchain. The distributed ledger is the major difference between centralized and decentralized systems like the traditional banking system and cryptocurrency ecosystem.
The blockchain distributed ledger ensures that each node has the updated details of blocks and transactions performed and permanently stored in the network, this adds an extra layer of security to the network. When a node mine a block, the block is validated and a new block is created, the blockchain distributed ledger technology is used by the system to distribute a copy of the new validated transaction and the details of the new block created.
Properties of Blockchain Distributed Ledger
The blockchain distributed ledger had some properties that include:
1- Distribution
The property of blockchain distributed ledger ensures that all connecting nodes have a copy of the ledger and current blocks, to aid security and transparency.
2- Security
A distributed ledger is secured through the use of hash cryptographic functions. This uses the hash algorithm to maintain encrypt and validate blocks by calculating the equivalence of the nonce number.
3- Immutability
This property of the distributed ledger ensures that any validated record stored in a block cannot be changed or removed. Date and time stamps are added to the distributed ledger for easy referencing.
4- Programmable
The blockchain distributed ledger is programmed to function automatically through the use of smart contracts. Smart contracts are used to manage and maintain transactions between buyers and sellers of cryptocurrency within a network and are also used to distribute and maintain ledgers within the network.
5- Unanimous and Anonymousity
The blockchain distributed ledger ensures that all connected nodes accept the validity of every block stored within the blockchain. It also ensures that the identity of nodes and participants are hidden and kept anonymous, this improves the security of the blockchain and the safety of participants.

Question 4
What Is Blockchain Double Spending and how Bitcoin handles this problem?
Blockchain Double Spending
Blockchain Double Spending is a problem associated with digital currencies where the same crypto amount can be used in multiple transactions. This often comes in form of an attack on the blockchain by the initiator of such transaction, as the transaction is initiated directly between the buyers and sellers.
Unlike digital currencies, double spending can not occur in physical cash transactions. To illustrate this, let's assume an investor buys real estate property worth $5000 and pays with cash, the exchange of currency for the asset is confirmed and the deal is sealed off. But assuming the investors pay with digital currency, double spending can occur, where the investor can send the same $5000 to another individual through manipulation of the blockchain, where details of transactions can be copied and rebroadcasted within the network.
There are various types of blockchain double-spending, some of which includes:
1- Race Attack: this type of double-spending occurs when an intruder sends multiple transactions using the same crypto amount to a blockchain network to spend them before they can be confirmed. This can only occur when the recipient accepts an unconfirmed transaction.
2- Finney Attack: This type of double-spending occurs when a miner duplicates the details of a transaction in different blocks and uses them. This can only occur when the recipient accepts an unconfirmed transaction.
3- Vector 76 Attack: this type of double-spending occurs when hackers use software to generate and send fake crypto assets to recipients within a blockchain network.
How Bitcoin handles Blockchain Double Spending
Bitcoin blockchain uses the distributed ledger technology and confirmations of transactions by validators (miners) to handles the problems of double-spending. When a transaction is initiated in a Bitcoin blockchain, it is unconfirmed and is not included in the block. After verification and validation (using a hash algorithm) of the transaction by miners, the transaction status is now confirmed, the recipient will receive the crypto asset and the added transaction is added to the distributed ledger of the blockchain.
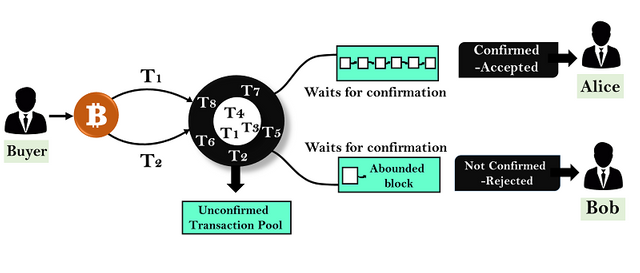
If a hacker launched a double-spending attack on a Blockchain, the confirmed transaction will be verified and sent to the recipient, while the unconfirmed transaction will be removed from the blockchain.
Adding the transaction to the public ledger ensures that the crypto asset and transaction details can not be changed or reversed.

Question 5
Practical + Theory, Visit Blockchain Demo and check section Blockchain, then explain in detail how Blocks Hashes Work in Blockchain, what will happen when any middle of the block gets changed, try to give screenshot for each possible details.
Block Hash in Blockchains
Block hashing is the use of cryptographic hashing algorithm to encrypt the details of a transaction and data stored in the block. To further understand this, the Blockchain Demo can be used to illustrate how a block hash works.
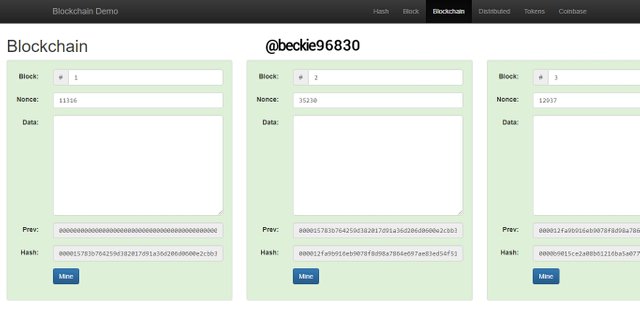
The above image describes the structure of a Blockchain that has four (4) blocks. As seen above, each block has a block number, nonce, and a hash. These blocks are linked in the blockchain by adding the hash of the previous block to the new block created.
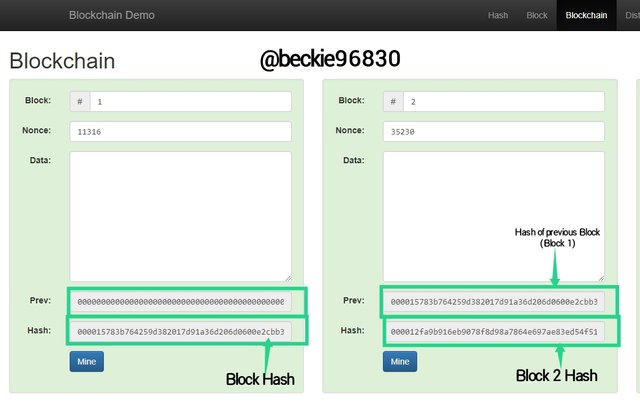
As seen in the image above, the Block one has a previous hash of 0, and a hash of;
000015783b764259d382017d91a36d206d0600e2cbb3567748f46a33fe9297cf.
This is because it is the first block of the Blockchain, often referred to as the Genesis Block.
Block 2
The block 2 has a previous hash:
000015783b764259d382017d91a36d206d0600e2cbb3567748f46a33fe9297cf, which is the hash of block 1.
The hash of block 2 is :
000012fa9b916eb9078f8d98a7864e697ae83ed54f5146bd84452cdafd043c19.
This indicates that block 2 is directly linked to block 1 in the blockchain.
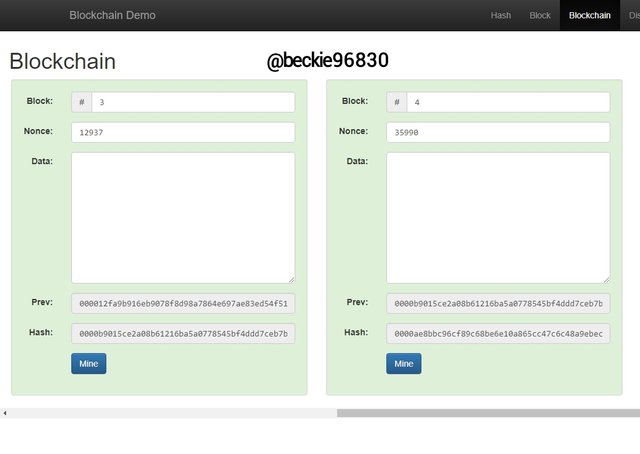
The same is applicable to block 3 and block 4. Where block 3 is linked to the blockchain with the hash of block 2 as its previous hash, and block 4 is linked to the blockchain with the hash of block 3 as its previous hash.
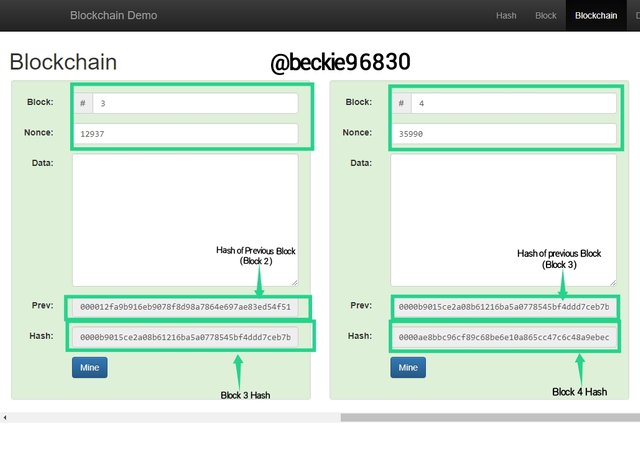
This shows how blocks are linked to form a Blockchain.
Adding data to a Block in a Blockchain
The structure of a Blockchain described above has no data stored in its blocks. When a new data is stored in a block, it automatically generates a new hash for the block and requires that the entire blockchain will be re-mined.
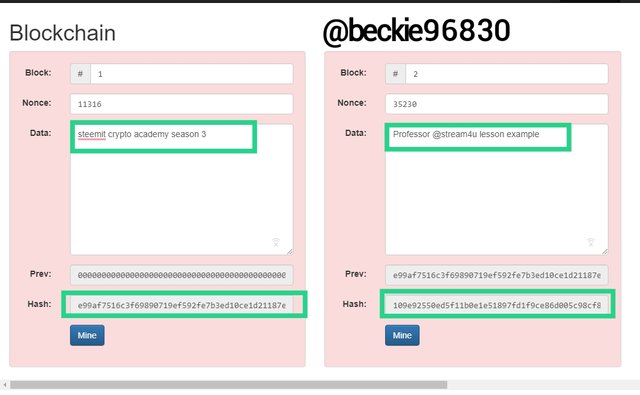
In the image, the data "steemit crypto academy season 3" and "professor @stream4u lesson example" added to block 1 and block 2 respectively changed the nonce values and hashed of the entire Blockchain.
When a change is made in a block, the distributed ledger technology sends a copy of the Blockchain changes made to all the nodes connected to the blockchain.
Mining of a Block in a Blockchain
Mining in cryptocurrency is the process of using high-powered computers to validate blocks in a Blockchain. This consumes a lot of resources like energy, speed, etc. This is done by calculating the nonce value of the block, when a correct nonce is determined, the block is validated and maintained in the blockchain. This confirms the block as a valid block. For this Blockchain Demo, a valid block hash usually starts with 0000.
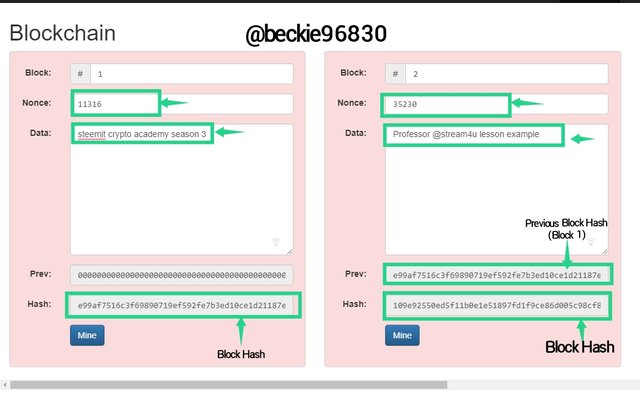
In the image above, Block 1 has a nonce is 11316, with a hash:
e99af7516c3f69890719ef592fe7b3ed10ce1d21187e0bb67df7e5d214144b2a, which is considered an invalid block.
In attempt to mine block 1, changing the nonce to 11300
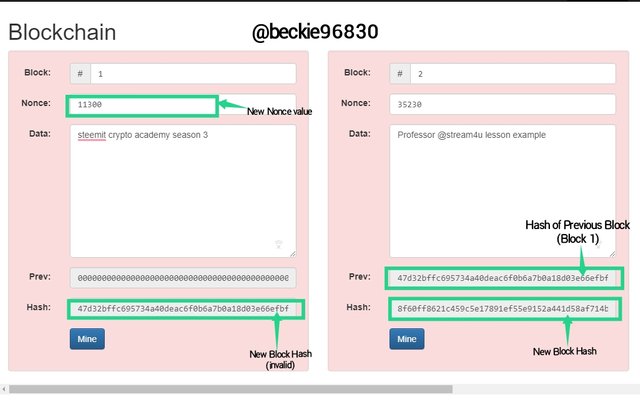
The New Nonce value 11300 changed the hash of block 1 to:
47d32bffc695734a40deac6f0b6a7b0a18d03e66efbf18068825ee7c88139e47, which is considered and invalid block, since a valid block starts from 0000. The has of the block 1 was added to the block 2 as a previous hash.
Changing the nonce value to 11308
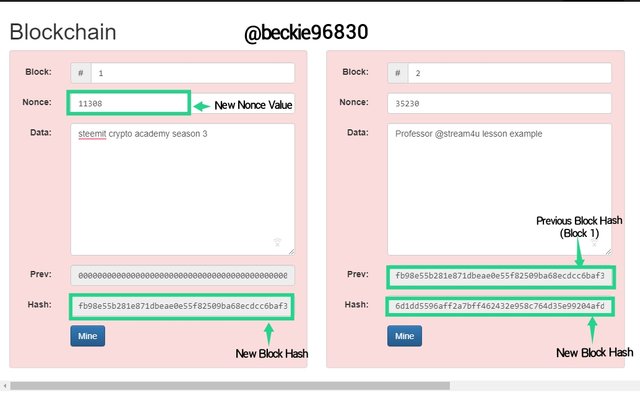
The New Nonce value 11308 changed the hash of block 1 to:
fb98e55b281e871dbeae0e55f82509ba68ecdcc6baf3c611fa8783e74b60e037, which is considered and invalid block.
This computation process will continue till the correct Nonce value is used. To illustrate this, click the Mine Button and observe the block.
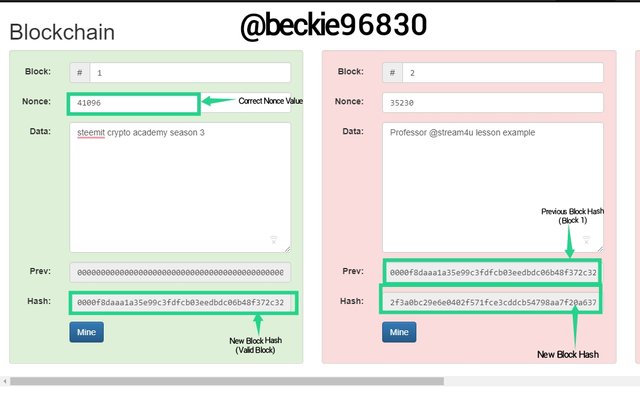
The Mine operation calculated the New Nonce value 41096 which gave a valid hash value:
0000f8daaa1a35e99c3fdfcb03eedbdc06b48f372c32daf4d2b89ecd4d9ddb97, which is considered a valid hash.
The hash of block 1 was used to link block 2 to the blockchain.
Using the same method to validate block 2.
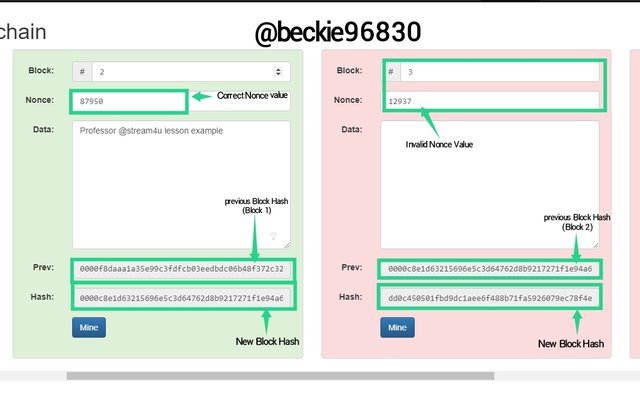
In the image above, the mine computation calculated the nonce value of block 2 to be 87950, which gave a valid hash value of:
000c8e1d63215696e5c3d64762d8b9217271f1e94a6dbb943fd44e68908df12, which is considered a valid hash.
The hash of block 2 was used to line block 3 to the blockchain.
This operation will continue till that last block is validated.
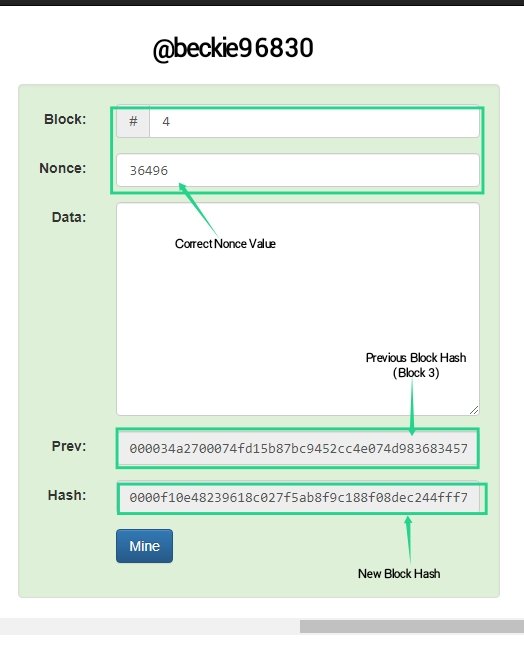
In the image above, the mine computation calculated the nonce value of block 4 to be 36496, and the hash value changed to:
0000f10e48239618c027f5ab8f9c188f08dec244fff7698df4ca56ead5a614f8.
The new data added changed the hash and nonce values of all the blocks in the blockchain. This proves the robust security feature of Blockchain technology.

Question 6
What Is Race Attack in blockchain? OR What Is Finney Attack in blockchain? OR What Is Vector76 Attack in blockchain?
Race Attack in Blockchain
The race attack is a type of double-spending attack launched on a Blockchain by an intruder or hacker, where the intruder sends the same token to different users within a blockchain using different nodes. This is done rapidly with the aim of using a single token to purchase multiple assets.
This type of attack is usually successful when the buyer accepts the transactions without waiting for confirmations. If the hacker leaves the multiple transactions in the blockchain, the mining process will validate one of the transactions and invalidate the other transactions, thus removing the invalid transactions from the blockchain.
The best way to stay away from this type of attack is to wait for confirmation from the miners before releasing the purchased items.
For instance, if a hacker has a token balance of 0.250 ETH, and sends 0.250 ETH to 3 different individuals within a blockchain, using different nodes. The victims of this attack will be the individuals that released their items without waiting for full confirmation from the miners to validate the transaction.
If 0.250 ETH is received by 1 of the individuals, the individual can release the item. The remaining 2 transaction orders created by the hacker will be removed from the blockchain as it is considered invalid.

Question 7
Limitations/disadvantages of Blockchain
Disadvantages of Blockchain Technology
Blockchain technology has some disadvantages associated with its wide use and adoption. Some of the disadvantages include:
Scalability:
The increasing number of connecting nodes in a blockchain affects the overall performance of the blockchain in terms of speed and processing power. This directly affects the cost of mining and thus causing an increase in transaction fees charged.
Cost of Mining
The mining of a blockchain requires the use of high processing speed computers that consume a lot of energy to keep up with the demands of the network through processing queued transactions.
Irreversibility
The immutable nature of blockchain prevents stored data to be removed or edited. This in some cases is favorable, but in events of error by a participant like copying a wrong recipient address, once the transaction is confirmed nothing can be done to reverse it.
Openness to Attack
Decentralization and accessibility were the basis of creating a blockchain. The open access of the blockchain data creates a platform for hackers to develop malicious attacks launched on Blockchains with aim of theft and major access control.

Conclusion
The Blockchain forms the architectural foundation of cryptocurrencies and their network security. It describes the various parts of the decentralized network. Blockchain consists of blocks, which are digital ledgers that store the details of transactions performed within a blockchain network and are distributed to all connecting nodes using the distributed ledger technology (DLT).
The decentralized nature of blockchains allows for transparency to a certain degree (considering the different types of blockchain with access restrictions).
Blocks are created within a blockchain through mining, which involves the use of powerful computers to validate and confirm transactions through resolving complex mathematical computations of nonce value computation.
The accessibility of Blockchain is capitalized on by hackers to launch various types of attacks on the network with aim of theft and majority access control.
In general, Blockchain technology created the cryptocurrency ecosystem which brought huge competition to centralized finance systems like banks. The adoption of blockchain technology in other sectors provides a robust system with valid security and reliance.
Thank you professor @stream4u for this insightful lesson.
Hi @beckie96830
Thank you for joining The Steemit Crypto Academy Courses and participated in the Homework Task.
Total | 10/10
Your Homework Task verification has been done by @Stream4u, hope you have enjoyed and learned something new.
Thank You.

@stream4u
Crypto Professors : Steemit Crypto Academy
#affable
Thank you professor@stream4u I'm indeed happy to have attended the lecture.
Thank you once again.