Steemit Crypto Academy Season 4 Week 2 [Advanced Course] | Mimblewimble Protocol
Hello friends, I welcome you all to my blog as I kick start with Week-2 of the Season 4 series of the SteemitCryptoAcademy lessons. I will be participating in lessons and Homework presented by Prof @fredquantum on Mimblewimble Protocol. My entries below...

In detail, explain your understanding of the Mimblewimble protocol.

What is Mimblewimble Protocol
This is no doubts that the continuous evolution and insatiable needs of man would always make him ask for more even when provided with More. The Bitcoin was a complete breakthrough from the conventional financial system by the provision of an alternative through its Peer-2-Peer payment module, additional Security layer to its safety mechanism and also anonymous status of transaction done via its ecosystem. Also bearing in mind features like Immutability, Interoperability and Transparency of process associated with it. But there was more to what the unsatisfied user wants which are issues bothering of a MORE Privacy status and Scalability of protocol. This brings us to the emergence of Mimblewimble protocol.
For Movie loving users, this would not be unfamiliar with to them especially Harry-Potter favorites. In the series, this was a act that hypnotizes another persons tongue with a spell so as not to expose some information about a given matter to others. This is the same concept used by the developer(s) who came about with this protocol of animosity of transactions.
It is a blockchain Protocol that carries more importantly A more pronounced privacy and anonymous status of transaction a little further from what is obtainable from the Bitcoin blockchain. Yes, it is an advancement on the Bitcoin blockchain which sees that transactions and transaction details are kept in a limited way from third parties who are not directly participating in ongoing transactions. This is seen from the more compacted use of its Distributed Ledger Technology which is different from that obtainable in the cryptocurrency gateway.
Most importantly, Mimblewimble was developed by an anonymous developers code-named Tom Elvis Jedusor which when translated to French means the Arch-Nemesis "Voldemort" in the Harry potters series. It was launched in July 2016 and later in the year 2018, the value was observed to have gone up. This sees the adoption of this protocol by Litecoin with sole aim of improving its Privacy and scalability up-fronts.

Discuss in detail how the Mimblewimble blockchain protocol works.

The Mimblewimble protocol structure is designed from the privacy transactions it is meant to execute. It specifically uses the EEC which stands for Elliptic Curve Cryptography which is a discrete based logarithm. Logarithms are simply the opposite of Multiplication which means when we have 2(9) = 512 (that is multiplying two (2) in nine (9) places), then the logarithm representation is Log2 (512) = 9
On the other hand, Discrete simply means the use of non-predefined values which may be seen from the use of Probability and Set theory indices. Therefore, the Elliptic Curve Cryptography uses the Discrete Logarithm to generate the private key for any transaction initiated from its protocol. In doing this, the senders token is encrypted using the BLINDING FACTOR which it chooses and the receiver have to concur with a similar value so as to validate the transaction.
This use of discrete logarithm or Blinding factors acts like the Proof of Ownership (Private key) which authorizes the receiver to claim and spend the coin. It also sees a combination of other cryptographic protocols by way of achieving optimal security through enhancing them. While combining this Cryptographic protocols, those needed data/information are left in privacy mood to third parties.
For Instance if Ada receives 10 MWC from Tony and Tonia respectively, and Ada later sent the 10MWC received to Obi. All these transaction gets verified and are not in the public domain as Obi is only aware of the direct and single transaction received from Ada without any details of how Ada got the 10MWC sent to him. But in doing so, Ada and Obi needs to exchange verifying details to be able to transact using the Mimblewimble protocol by noting the Blinding factor which generates and serves as the Private key.
Example of these combined protocols include the Dandelion, CoinJoin and Confidential Transactions (CTs).

Discuss in detail your understanding of Confidential Transactions (CTs)

Confidential Transactions (CTs) is one of the combinations adopted by the Mimblewimble protocol to optimized its security potentiality through enhancing its system as well. This protocol ensures that there are improvements seen in concealing the transaction amounts and hence making it Private while upholding the potency of the public network to ensure ledger entries still sums up. It does not add any cryptographic assumptions to its execution process with a reduced and manageable overhead.
The Confidential Transactions (CTs) uses the basic tool that is based on Pedersen Commitment. This commitment inbuilt system allows it to keep data secret but as well commit to it to avoid been changed. For example, a simple commitment scheme can be demonstrated using the cryptographic hash like this;
Commitment = SHA(Blinding Factor || Data).
Even if it happens that the commitment is related to a third party, it would be difficult to guess the blinding factor and data but when both data and blinding factor are revealed, they can run the Hash with anticipated output in view. The Blinding factor is always necessary because it gives the system an additional security level; without it the data can be easily guessed and commitment known therein.
In same vain, commitments can be added using the default Pedersen commitment scheme by summing the total commitments and that of the data which comes with the sum of the blinding keys as well.
Therefore we have;
C(BF1, data1) + C(BF2, data2) = C(BF1+BF2, data1+data2)
where C(BF1, data1) - C(BF2, data1) = 0
Where we have more commitments in the roll;
C(BF1, data1) - C(BF2, data1) - C(BF3, data3) = 0

How do you think Mimblewimble Protocol can be utilized on the Bitcoin Network to enable anonymity of transactions and improve scalability?

Before knowing how the Bitcoin can utilize the Mimblewimble protocol, we have to know what similarities or differences exists between both protocols.
Bitcoin:The Bitcoin entails that all transaction done in its protocol are documented and made open to the public domain right from its genesis block but the identity of the sender and receiver are anonymous (Privacy).
Mimblewimble: It only keeps the essential information which is to offload redundant data offline but goes a little higher by not only concealing the identity of sender & receiver but also ensures the transaction details (Wallet addresses, transaction Amount etc) remains between the sender and receiver only (Additional Privacy).
Bitcoin: There is presence of an Enlarged Blockchain data Size which makes the protocol less scalable in its transaction throughput. (Hence still requires the Mimblewimble protocol as a side-chain solution to enhance the bitcoin ecosystem).
Mimblewimble: Removes the presence of scripting system found in Bitcoin that allows it to store all transaction information in its protocol. This allows for the removal of some transaction data which reduces scalability overload from its system that gives an edge over the Bitcoin due to lesser blockchain data size.
Therefor it is obvious the two (2) distinguishing factors between both protocols stays between the Privacy & Scalability indices of both systems. Some school of thoughts has said that combining both protocols for now would be an enormous task for transaction to be executed in the Bitcoin blockchain but I think there is a similar transaction pattern seen in the Bitcoin system that removes micro-transactions offline and only allows Initial and Final transactions recorded in its blockchain. (The Lightning Network Channel)
The Lightning Network can be positioned in a manner that all of its micro-transactions does not only remain anonymous for sender & receiver but also for other transaction details including its wallets addresses and amount sent. Though It still retains its high scalability given to the absence of miners rather there are available nodes to verify transactions in this Off-chain system.
Secondly, the Bitcoin through its Off-chain systems can adopt a direct channel that allows a complete animosity of transaction by activating special button for Privacy transaction which we already see exist in some blockchain protocols with privacy transaction but this attracts additional fees. This would see the non-traceability of transaction as well as maintain its high scalability.
Most importantly the Cut-through feature of the Mimblewimble vis-a-vis the Pedersen Commitment gives the Mimblewimble edge over the Bitcoin protocol to give it both additional layer security and privacy.

State the Pros and Cons of the Mimblewimble protocol.

| Pros of Mimblewimble | Cons of Mimblewimble |
|---|---|
| It's largess of protocol in use makes it divergent against inflation | Due to its Reliance on digital signatures, there are likelihood of vulnerability through quantum device attacks |
| Gives the system an additional layer of security. Minimal occurrence of coin theft under standard settings | Most protocols that uses the privacy transactions usually have a lower longer transaction throughput.(Maybe the reason for offloading redundant transactions) |
| High scalability seen since redundant transactions are offloaded offline | |
| Ensures High Privacy of transactions done in protocol | |
| Enhanced Fungible status of coin; when coins origin cannot be traced, it can neither be invalidated |

Question 6
Discuss in detail at least a Crypto that uses the Mimblewimble protocol.

There are already some crypto assets that have been seen adopting the use of Mimblewimble protocol and they include; Litecoin, Grin, Beam and the Mimblewimble itself. For this post, I would be discussing just the Grin adoption of the Mimblewimble
The GRIN
The Grin was officially launched in January 2019 having the full adoption of the Mimblewimble protocol with an open-source private cryptocurrency system. Its launch did not pass through the conventional tradition of Initial Coin Offering rather it received Donations to fund its project. It is primarily known as a Private, open-source and Scalable cryptocurrency due to its deep adoption of the Mimblewimble protocol.
After the launch of its Genesis block, its second block was mined in less than one minute of becoming life in the cryptocurrency space with the use of the PoW Consensus Algorithm. It was designed to solve the age-long scalability and limited privacy lacking in the leading coin (Bitcoin). Grin wan intentional about the adoption of a blockchain system that best suits its protocol by selecting RUST as its programming language.
How Grin Transacts
To fully understand the concept of transaction in the Grin system, we will also need to know how the UTXO works in the Bitcoin blockchain where it leverages three (3) key features;
- Signature
- Liquidity availability
- NO existence of transaction using same funds.
These are implemented by the use of the Unspent Transaction Output model which takes into cognizance the modus-operand of this protocol before they are transacted. But there is a little difference noticed in their operations, the Bitcoin is seen to have multiple signatures required for each of the transactions that it executes, unlike the Grin that generates a Multi-signature for all transactions without necessarily having to create individual for each of them. It facilitates the use of a blinding factor instead of addresses which allows both parties to only know the transaction details and amounts involved in the transaction which is the ultimate stance of the Mimblewimble technology (More Privacy).
In the Grin system, the blinding factor is the Zero-knowledge, a proof system of the CTs. It encrypts all input and output cryptographically in a transaction which acts as the private key for each transaction done but this does not entail one is sharing its private wallet key. Knowledge of the Blinding entails that one can claim and spend the fund. Validation done in this protocol follows this routine;
- Verification of Zero sums (Sum input subtracted from the sum of output should be Zero)
- Ownership of Private Key as access.
Coin Distribution & Governance
Grin did not embark on any ICOs rather on Donations received which made its initial supply to be Zero (0). Mining started immediately after it went live with the reward of 60 grins given for block reward as well as One grin issued for every second. It adopts the Linear Emission Scheme that makes it maintain its status for the entire emission period. Also, it can sync faster due to its Lightweight feature vis-a-vis the bitcoin that stays longer period before syncing.
It parades an organized governance system that allows regular developmental meetings and Bi-weekly meetings that take place in Glitter. A full analysis of each outcome of its meetings can be found in the GitHub platform with anyone allowed to partake in its meetings with progressive solutions expected.
Grin Listings and Value
It can be found in some of the Top Exchange listings which makes it easy to access and use. Some of these platforms include; Bittrex, Kucoin, OKEx, Gate.io, Hotbit, Bgogo and Bibox, Coingecko, CoinMarketCap, etc.
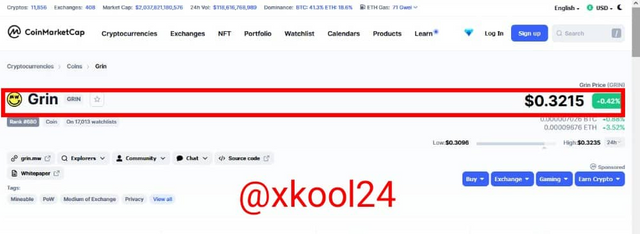
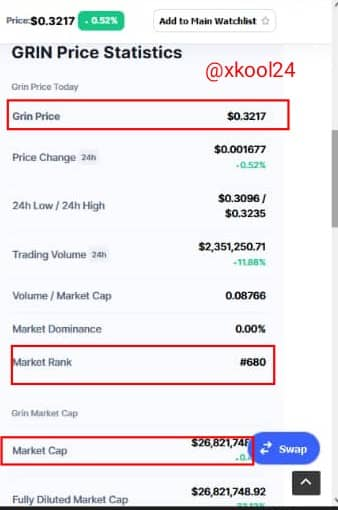
Grin Price - $0.3217
Market Rank - #680
Market Cap - $26,821748

Conclusion

The emergency of Mimblewimble was specifically an advancement on the Bitcoin blockchain to proffer more on Scalability and Privacy features which were perceived deficient in the operations of the Bitcoin system. Though there is alternative off chain systems implored by the bitcoin developers to propagate scalability in its system done in the Lightening Network Channel whereby the transactions happen off-chain, there is still not enough privacy seen in this process. Hence this remains a chance to the Leading coin.
Mimblewimble adoption in some of the crypto space has shown improvements with LTC expected to launch its adoption before the end of 2021. This has shown the importance of these two driving forces "Privacy and scalability" at the center of cryptocurrency space.
Thank you respected prof @fredquantum for this homework task
Written by @xkool24


So brilliant, I cannot do this
I believe you can. Thanks for the appreciation.