Grassroot Crypto Education | Series 2 Volume 9 - Scams in the Crypto Ecosystem (Part 2)- Phishing and Dusting Attacks
Introduction
It's the 9th week of our crypto education in series two, what a great journey so far. It's a great pleasure to be writing again in the community and I hope you are all doing great today. Two weeks ago, we started
the discussion about scams in the crypto ecosystem which featured investment scams, we would be looking into other scams today. For today, we would pick another two methods of attacks in the crypto ecosystem, Phishing and Dusting Attacks.

Designed with Adobe Photoshop
Phishing Attack
Phishing attack is one of the ways scammers utilize to steal from asset owners, this is not limited to the crypto ecosystem rather it exists in other financial settings as well. Phishing attack in cryptocurrency is the false representation of original crypto firms or exchanges, or users, and so on, by scammers. The purpose is to prey on crypto users and the result is always bad, carting away assets from the rightful owners.
In addition, phishing attacks can be a fake presentation of links that looks original but technically it's not, which is just aimed at getting users' details for a successful attack. It can be one promising huge returns on investment or giveaway. It comes up in different ways to lure a crypto user to perform certain actions. We would be discussing different types of it later in this article.
Phishing attack, when launched by the scammer or group of scammers, it's targeted at all users irrespective of their level in the ecosystem (beginner/intermediate/advanced), the aim is anyone can fall a victim. Mostly when such attacks are launched, inexperienced users fall, victims, because they may not have an idea of what they are interacting with.
Having explained this method of attacks utilized by scammers in the ecosystem, let's take a look at some of the types of phishing attacks and how each of them is carried out.
Types of Phishing Attacks
Reward Phishing Attack
This is a common type of phishing in the crypto ecosystem, it always involves the use of catchy fake reward to attract users to click on the link which leads one to another website designed by the attackers, in the website, they may request a user to input his/her private key to claim the rewards, they use that medium to gain access and have control over the wallet of the victim.
In some cases, they may not request users' private keys but clicking on the link, instantly download malware to the device which gives the attacker access to the crypto wallet of the victim, it doesn't end well for the victim as such you should be careful.
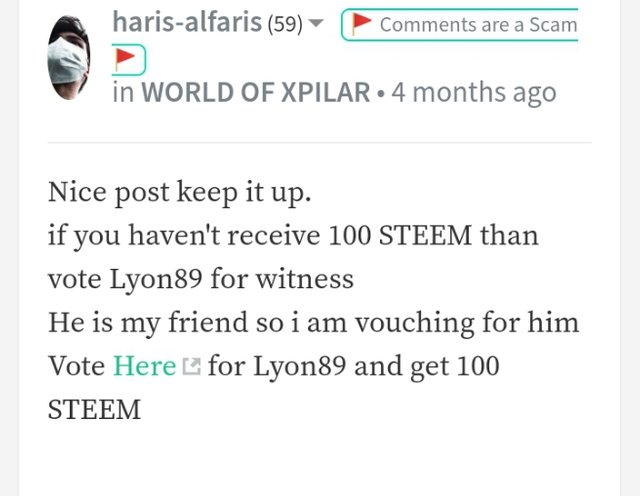
Link
Above is a screenshot promising users 100 STEEM, that doesn't exist, it's a phishing attack. If a user clicks on it, the attacker would have control over the account including the wallet, and even use the account to spread the attacks. As such, you should be careful when you come across a link like this.
Clone Phishing Attack
In this type of attack, the attackers clone an original message from a legit crypto firm with a link in between. The links therein are obviously not original, it all takes patience to ensure the link is original and if a user clicks, he/she would be a victim of malware download or password request that give the scammers full control of the account.
For example, if the Binance Exchange had shared emails about a referral program with the original link https://www.binance.com/en/activity/referral, attackers can clone the entire message and replace the link with another created for scamming people.
The new link can be https://www.bnance.com/en/activity/referral, they have completely eliminated [i], if a user is not patient enough and visits the link, he/she may be requested to input a password on the website, that's the beginning of the problem for the users' account.
Impersonation Phishing Attack
Scammers can technically become a chameleon taking different forms, in essence, impersonating another person or account (mostly of high rank). In this case, they may create an account similar to a one belonging to a notable person and distributes messages to people sometimes with investment doubling and so on.
For example, a scammer can decide to impersonate steemcurator01 by creating an account that closely has the same name, let's say steemcurtor01 and leave comments on people's articles to visit a link or even cajole them to send some STEEM tokens to receive double of it and more. Beware of these as well.
Apps Phishing Attack
Another form of attack is installing malware on users' devices after they have downloaded an application. This is very common when you download Apps from untrusted websites, your device might have downloaded malware as programmed by the attackers, this monitors your crypto activities over time and reveals sensitive information to the attackers. It mostly results in a huge loss to the owner in the long run.
Dusting Attack
Dust in the crypto ecosystem is different from the usual dust you are used to. Dust in this context means small amounts of tokens sent to the wallet, let's say 0.001 STEEM. On the Steem blockchain, users tend to use this to communicate with each other, exchanging encrypted messages to communicate in the presence of others such that they don't reveal the details to outsiders, we have talked about encryption in a lesson before, you can check again.
Dusting attack is very popular which aims not to communicate any good information, but rather to defraud users. Dusting attack involves distributing dust to crypto wallets in the quest to identify crypto users and other wallets linked to each user to see their activities in the crypto realm and see if they are worthy of being attacked. If they have identified these things, an attack is launched at the target wallets.
In addition, having been able to get the desired information about wallets, attackers utilize the dust attack conducted earlier to plan a phishing attack in some instances. In most cases, links are embedded in the dust such that the scammers expect users to visit so that they can gain control. Let's see an example below.
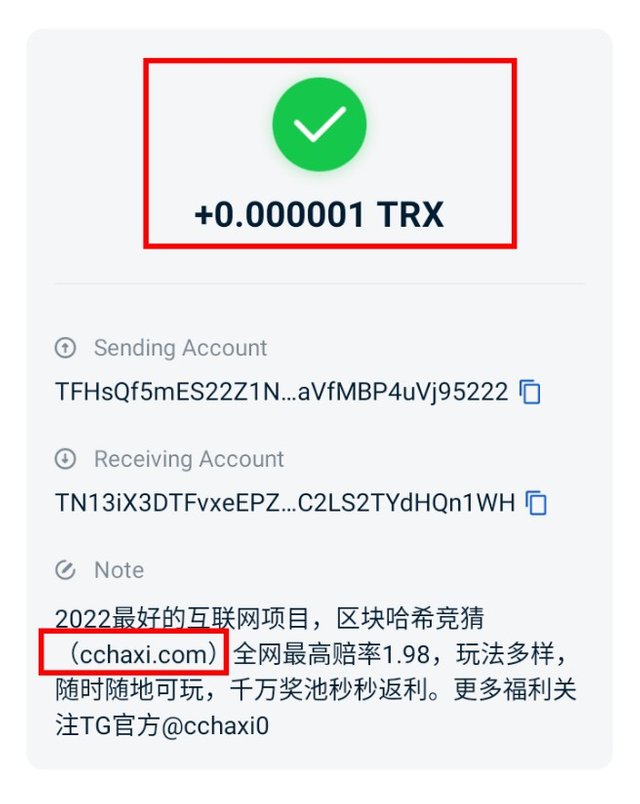
Screenshot from TronLink wallet
Take a look at the image above, I have received the dust of 0.000001 TRX in my TronLink wallet with a link embedded which could be said to be a phishing link, I looked up the wallet address on TronScan and it has sent out dust to other wallets too. You can view it here https://tronscan.org/#/address/TFHsQf5mES22Z1NnHDUaVfMBP4uVj95222. You should also beware of this type of attack.
How to Avoid being a Victim
- Do not click links from random users, only visit links from trusted users and you should check the URL very well to be sure you are visiting a genuine website.
- Avoid chasing rewards that sound too good to be true, they are mostly devised for phishing attacks.
- Before you interact with a top account giving directives on Steemit, ensure you check the username to be correct, I have given an example of a probable impersonation of top accounts like steemcurator01 and so on.
- Do not follow links embedded in the dust if it goes beyond an encrypted message between you and a friend.
Conclusion
In conclusion, the crypto ecosystem is associated with a lot of methods devised by scammers to rake away funds from users. It's important to know some of the methods they utilize for such frivolous activities such that one doesn't end up a victim. We have been able to talk about phishing and dusting attacks in this context today, and a few ways they work. Stay safe in this ecosystem by practicing healthy interactions. Thanks for reading today and I look forward to your participation in the homework task.
Homework Task
- What is your understanding of Phishing Attack? Discuss any 2 types.
- What is Dusting Attack? How can one Avoid being a victim of the two attacks discussed?
Guidelines
- Write an article of at least 300 words. Keep your explanation as simple as possible.
- Include the tag #grassroot-educations2v9, #fintech, #steemexclusive, and your club status among the first 4 tags. Also, tag me @fredquantum in your homework entry.
- The participation in this lecture/homework task is open to everybody but only entries made by verified kids would be reviewed.
- I will check your articles and drop comments on the entries submitted now till 11:59 pm UTC, 12/06/2022.
Cc:-
@steemkidss
Thank you so much sir for this great delivery. The kids will surely benefit from this lesson. I have personally benefit from it.
Reminding us about phishing links and how to avoid being a victim is great. I appreciate the valuable information you shared in the post.
Thank you, @udyliciouz for verifying my article today and I am glad you have learned a few things from this piece.
My homework: https://steemit.com/hive-139765/@ghani12/phishing-and-dusting-attacks
My entry
https://steemit.com/hive-139765/@habdallah/grassroot-crypto-education-or-series-2-volume-9-scams-in-the-crypto-ecosystem-part-2-phishing-and-dusting-attacks-or
Here is my entry sir:
https://steemit.com/hive-139765/@david-o/grassroot-crypto-education-or-series-2-volume-9-scams-in-the-crypto-ecosystem-ii-by-david-o
Hello, @fredquantum. Your article has been supported using the @steemcurator05 account.