Understanding Hash And Cryptography - Final Part
Hello everyone, hope you all are doing good? I'm back with the Final Part of this amazing series, Understanding Hash And Cryptography. If you haven't read the Part 1, Part 2 and Part 3, I strongly suggest you that by clicking here for Part 1, here for Part 2 and here for Part 3. In today's article we would checking the reliability of SHA-256 and knowing the main and notable differences between Hash and Cryptography.

We do this to prove the reliability of SHA-256 to know if it is really collision resistant. Let's go ahead and do the test for "CryptoAcademy", first. To do this, you have to click this SHA-256 hash generator link.

Then, input the text, "CryptoAcademy". The hash code I got from the word "CryptoAcademy" is;
D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9

Alright, we have seen the hash code for the word, "CryptoAcademy". Let's now test for the other word, which is "cryptoacademy".
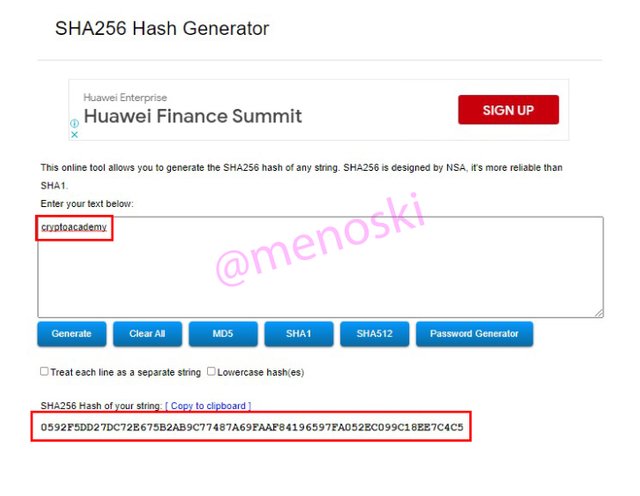
The hash code I got the word. "cryptoacademy" is,
0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5.
As we can see we got two different hash code but why? The meaning and spelling of the words we tested, are the same but there was a difference in the case of words, the first word we tested had two upper case letters which are "C" and "A"(CryptoAcademy) while the other word we tested, only had small case letters(cryptoacademy). This test we carried out shows that the SHA-265 is case sensitive and also shows that the SHA-256 is truly collision-resistant.
Notable Differences Between Hash and Cryptography.
| Difference | Hash | Cryptography |
|---|---|---|
| Length of Encrypted data | Length is static and doesn't change. | Length is not static and changes. |
| Security | Hashes can not be cracked | Cryptography can be cracked with a key. |
| Process | It is unidirectional | It is bidirectional i.e encrypting & decrypting |
| Password | It requires no use of passwords. | It requires the use of passwords |
| Usage | Use for verifying, authenticating and securing our data. | Use for sending data safely. |
These are the main and notable differences between Hash and Cryptography.
I hope you all found the article interesting and exciting. Do well to share your thoughts about the article in the comment section below. Thanks.

Nice publication my friend. I am happy that you have gotten to the final part of this publication and it was worth the read. Nice one once again.
Such a nice publication on Hash and Cryptography. I have missed 2 parts of your series but whatever i get from this is really useful. keep sharing and keep educationg.
@tipu curate 6
Upvoted 👌 (Mana: 0/4) Get profit votes with @tipU :)