Blockchain and cybersecurity: 3 points to consider.
I reviewed some news about cybersecurity and blockchain on cryptoworldnews and found an interesting article that gave me something to think about.
The article in question focused on three aspects in which blockchain technology could help address the growing security threat that users can find on networks:
- Averting DDoS attacks
- Authenticating downloads
- Offering consensus mechanisms
Each of these aspects is discussed and explained quite well, I would like to make a brief summary and add a comment on them.
1. Averting DDoS attacks
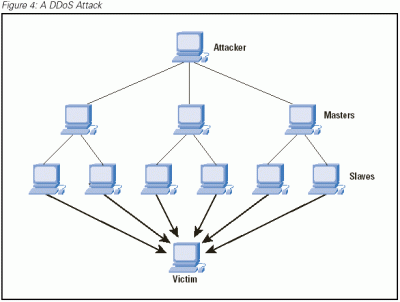
Well, distributed denial of service (DDoS) attacks are something that I think we have all seen at least in their effects, after all, quite famous sites like Twitter and Spotify have been subject to these attacks where servers are saturated with "garbage" service requests and the site is made to collapse.
These attacks take advantage of a weakness of the domain name system (DNS), which is the system that allows us to use names for internet addresses. For the new generations it can be a very common sense to write an address with alphanumeric characters in the address bar and take you to a particular place, but I can tell you that this is not always the case, you will see an IP address is , at the beginning of everything, a numerical address.
For example, if we want to know the real address in IPv4 or IPv6 protocol of a site, we can use services such as DNS lookup - Look up DNS record and put in the search box the name of the site we are looking for, then it will show us in the results the addresses numeric of the web that we are consulting.
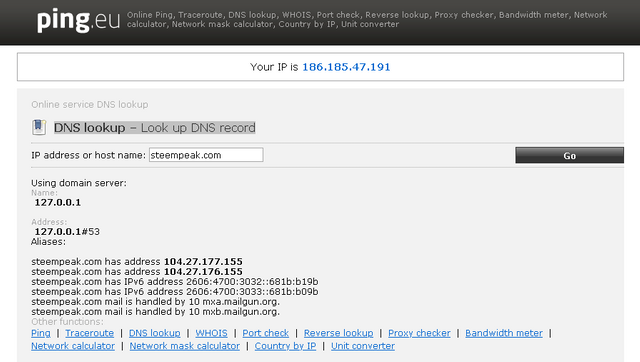
Screening https://ping.eu/nslookup/
The problem is that although domain name servers distribute their files among their peers to disseminate names and facilitate identification and navigation on the Web, it happens that it has a certain centralization in its structure, so it can be achieve successful attacks on these servers and cause the collapse.
Then, by implementing a domain system on a blockchain, service requests from a more robust anera can be addressed and it is much more difficult to achieve a service crash.
2. Authenticating downloads
Software authentication is a matter of interest, especially when viruses, Trojans and all kinds of malware have evolved in great strides and often pose as legitimate software.
The existence of an open, auditable, distributed and constantly supervised chain of information allows greater security for download authentication. Thus, the usurpation activity by malicious programs would be reduced to some extent.
Of course, users are always advised not to download from unknown sources and not accept downloads from unidentified third parties, but it has happened that in some cases even recognized online service store platforms have found that they were hosting malicious programs and that there were Distributed Trojans or malicious programs without knowing it.
Blockchain technology could allow software signatures to be audited by members of the same blockchain and that would be an additional form of security.
3. Offering consensus mechanisms
Before starting this section, we will cite a definition to clarify what is being talked about:
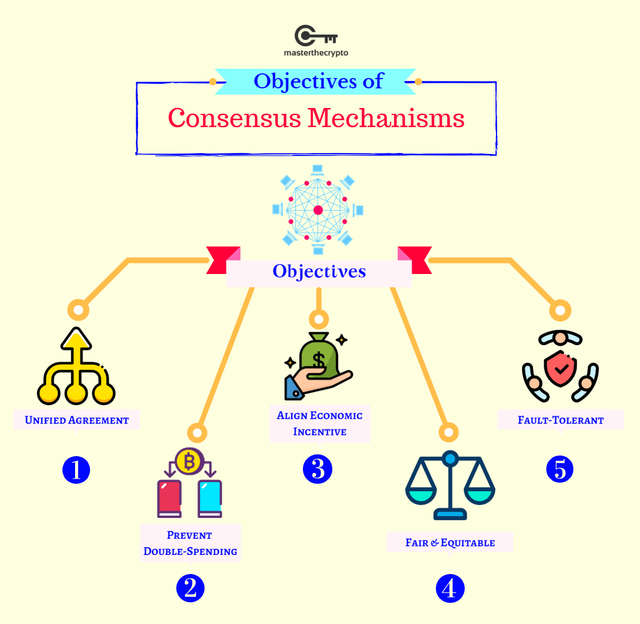
What Is a Consensus Mechanism?
A consensus mechanism is a fault-tolerant mechanism that is used in computer and blockchain systems to achieve the necessary agreement on a single data value or a single state of the network among distributed processes or multi-agent systems, such as with cryptocurrencies. It is useful in record-keeping, among other things.
The use of blockchain technology could be useful in identifying data theft, thanks to its distributed accounting and cryptography in the encryption of information. In addition, the verification process offered by blockchain is instrumental in identifying the data inconsistencies, which are immediately marked and can be identified as "alarm signals".
The usurpation of digital identity is much more complicated in the blockchain, in the same way, the possibility of associating an identity with a specific digital product and that this serves as an authentication signature is something that can help to combat these problems.
Final words
These points that are tackled for sure are not the only points of computer security that would benefit from a greater use of blockchain technology, but I certainly believe that they are one of the most prominent points and perhaps of which end users might notice shorter term.
Of course, even today, the first and last line of defense and security is the same user, but tragically it happens that the user is usually just the "weakest link in the chain" or less prepared in matters of security.
Post published for the @project.hope community - https://beta.steemit.com/created/hive-175254
20% of this Post is intended to support @project.hope - Project #HOPE Community

Project #HOPE Website


Thanks for sharing this. Blockchain and distributed ledger technology (DLT), as it is also known as, is still evolving, so there are many nuances about them yet to discovered. These kinds of articles help stimulate the thinkers pondering them :)
Posted via Steemleo
Thanks for the comment. I just think there is still a lot of field to explore and things to learn about the usefulness of blockchain technology, I hope to learn a little more in the future.
Very nice writeup!
At the end of the day DDoS attacks still come down to firepower. Even if you try to protect yourself via services offered for example by cloudflare and others a wide spread bot network won't have a hard time taking any given network service down. No matter how much redundancy and checks are in place the service will suffer at some point. It's mostly a question of cost on both sides, attacker and target. This seems to be one of the things that'll stay with us not matter how much you scale up redundancy and scattering of services. Just my 2 sats on this.
Cheers!
Lucky
I see, so the DDoS attacks are not going to leave us ... I suppose the strategy would be to contain, maybe make it so expensive to carry out the attack that it is a dissolution.
Of course, if a "Target" is very attractive, no matter how difficult it is, I suppose there will be people interested in attacking it.
Sadly, yes this is true imho.
Solid read. Upvoted and resteemed :)
Thanks for the comment and for sharing the post.
@tipu curate
Upvoted 👌 (Mana: 10/20 - need recharge?)
Hello my dear teacher @pedrobrito2004, great article.
I definitely need to learn more about this.
What do you propose about the use of blockchain technology, maybe you reduce cyber attacks?
Hello, just the recommendation is the use of blockchain technology to improve cybersecurity.
After all, the characteristics of being distributed, open to auditing, non-modifiable and with continuous registration and verification, in addition to the establishment of consensus, make it possible to consider it as a viable way of addressing the threats that are analyzed.
hi dear @pedrobrito2004
I find it fascinating that such important advances are being made in the blockchain; downloading files seems very cool and interesting, it will serve to sell many things and securely: applications, software, games, etc.
Undoubtedly a very interesting article, I hope that AI goes hand in hand with blockchain technology.
Posted using Partiko Android
Thanks for the comment, I also hope that other technologies will advance and that the use of blockchain in different fields will be widespread. We will have to wait to see what directions the future takes.
I have fallen prey to scam before on the blockchain and i was down for days and i also learnt. Thanks for sharing this.
Thanks for the comment. I share that I have also fallen into cheating and scam schemes, despite trying to be careful, but I have learned a little from each mistake, so I hope not to repeat them in the future.
Do you know how ISO 9001 standard works? Most people don't. It is behind many products in the supermarkets. Blockchain can also be a technology hidden in the background. My grandma doesn't know how bank transactions work, but still can use a bank (debit) card. But: We need user friendly blockchain solutions for all!
I think you are right, it is somewhat contradictory, the less you know the more vulnerable people it is, but in reality ordinary people do not want to know everything about the technology we use every day ... so, we do not start to find out how something works In depth, what we want is to be easy to use.
I can support the idea that things that are friendly to end users are needed, but I don't forget that users have to be educated to generate a minimum of user culture that helps avoid problems.
I have come to understand that as tech keeps growing, so do scammers grow in knowledge. I have loved the blockchain from the day i knew about it because of consensus. The use of the blockchain to identify theft is a good advantage. Thanks for sharing.
Thanks for the comment. I certainly share your ideas.
Dear @pedrobrito2004
I've been thinking a lot about security threats. And my impression is that thanks to decentralization - things will get only more dangerous.
Right now centralized servers are being an "easy" target. Right? And it's not that easy to hack to those servers. Could you imagine that your own bank would be hacked and your account would be cleared out? Very unlikely.
However - could you imagine your personal PC/laptop being hacked and all your keys and passwords stolen? Your wallets cleared out. And noone to complain.
Thank you for this excellent read. Upvoted already,
Yours, Piotr
Individual security always seems more vulnerable to me, but I think that in a broad picture, decentralization with a constant audit and the need for consensus is much harder to hack.
Since when performing an operation on the chain, the witnesses of the chain will record what was done, what hash is done and that would be visible to any block explorer, it is not impossible, but I think that if it is difficult, that makes me He recalls the old phrase: "One person can be deceived for a long time, many people can be deceived for a short time. But it is quite difficult to deceive many people for a long time."