SIZ EDUCATION | 7 BIGGEST CYBER ATTACKS and It's PRECAUTIONS|| 20% to @siz-official || by @nehazakir
Assalamualikum! , hope you are doing good as am I. As the title says this post is about cyber attacks and its precautions ,hope you'll find it helpful.
Nowadays, everyone is worried about cyber-criminals,fraudsters and hackers as we heavily rely on smartphones ,social media and electronic devices connected to internet from which our information can be easily stealed .
Our systems ,networks ,programs ,data and information are not protected because of CYBER ATTACKS . CYBER SECURITY is the solution to all of these problems.
Before mentioning cyber attacks and its precautions ,I would like give a breif introduction to cyber security.
CYBER SECURITY
It is basically a process consist of technologies and controls of protecting sensitive data,information ,networks,operations and software applications from the cyber attacks.
Its also called information technology security (IT Security).
CYBER ATTACKS
Its is considered as an unauthorized attempt to exploite resources ,steal ,expose, disable or destroy data inorder to exploit and encrypt data to extract money.
Cyber attack is also known as online hacking & cyber-crimes.
Some big cyber attacks are
1.Man in the middle attack
2.Backdoor
3.Phishing
4.Ransomware
5.DDos attack
6.SQL injection
7.Malware attack
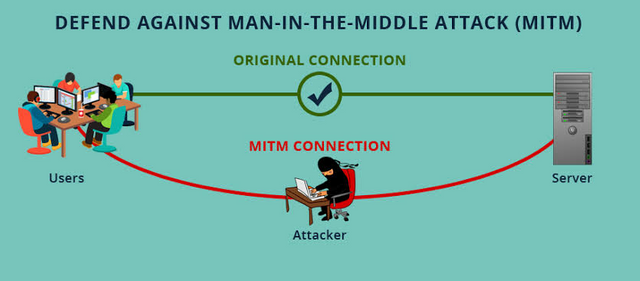
1.MAN IN THE MIDDLE ATTACK
A man-in-the-middleattack is a sort of snooping attack where attackers makes independent connections with an existing conversation or data transfer of user. After inserting themselves between the computer and the server to intercept confidential data. Mainly attackers steal information of financial apps and pretend it to be a normal exchange of information
PRECAUTION
To avoid MITM attack you should setup a Virtual Private Netwroks (VPN) or Intrusion Detection System(IDS) they'll basically encrypt your web traffic and secure your communication. Use high security web browsers and keep mobile security system up to date.
2.BACKDOOR
Backdoor attack is type of malware that is used to get unauthorized access to normal security of a computer system. Backdoors are installed by software ,hardware developers in order to access sensitive data remotely and update malware . Attackers usually attack small businesses as they have limited resources.
PRECAUTION
Backdoor attacks can be prevented by using advanced antivirus system that can detect malware installed in the system. Malware is often installed in games and other type of softwares that can be downloaded , just download the software from official webs and avoid pirate sites.
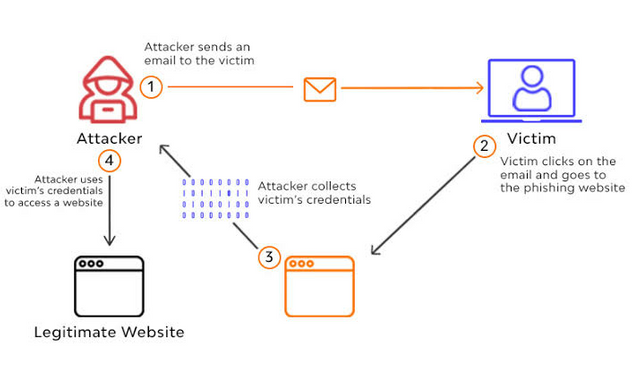
3.PHISHING
Phishing is a cyber attack that is most common challenge faced by individuals as well as companies ,in which attackers disguise as a trusted entity which trick the human victim and steal data, mostly credit card numbers ,pins. Its usually done by emails ,messages or online scams.
PRECAUTION
Don't give your information to the sites without security certificate. Keep your security system update . Don't be tempted by pop-ups and click on any link ,its often linked to malware.Only share your personal data or info with official site in case its necessary.
4.RANSOMWARE
Large companies, organisations or agencies are attacked by ransomware attackers. Its also a malware type in which attackers blocks the system and personal files from users and demands ransom money (ie. In form of cryptocurrency or bit coin)from users to restore access to the data. Initially, they get access to the data which enables them to use malware needed to encrypt
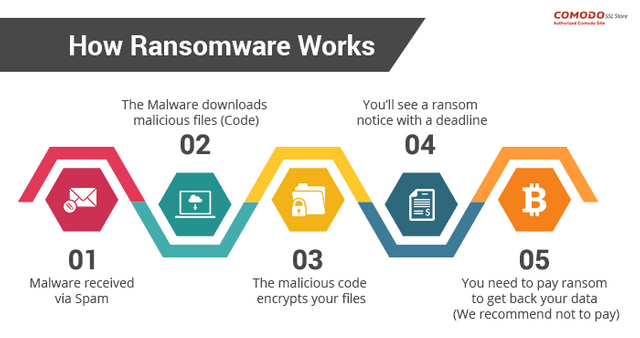
https://comodosslstore.com/blog/
PRECAUTION
Use VPN services ,dont click on links or attachments in emails that look suspicious
,dont give your personal info to any unknown/ unofficial website. Keep your mobile security system up to date ,use strong passwords and don't forget to make backup files
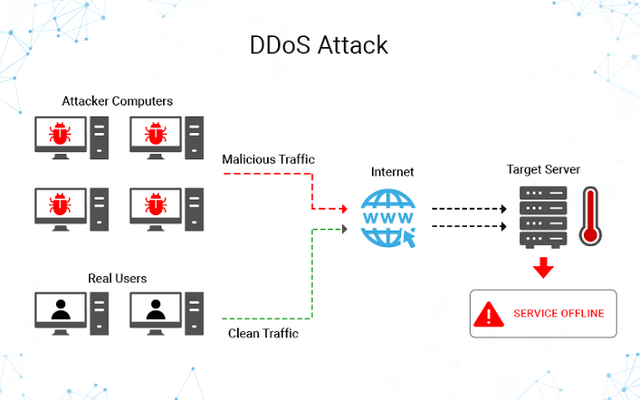
5.DDOS ATTACK
Distributed Denial of Services(DDOS) attacks are linked to IOT devices that are infected with malware. It's the process of sending huge amount of data requested from multiple resources that causes disturbance in the system which freezes or crashes the system . It is growing more extensively and firmly from last twenty years.
PRECAUTION
In order to prevent DDOS attacks you need to install prevention management systems and other security layers ,adopt Cloud based service providers ,deployment of anti-DDOS hardware & softwares and perform a network vulnerability asssesment to protect system from traffic inconsistencies and to protect DNS servers
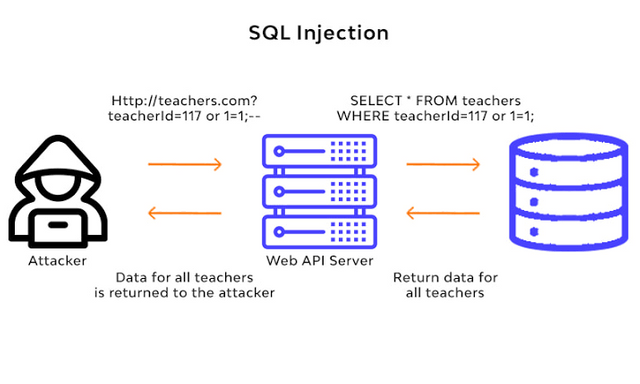
6.SQL INJECTION
SQL injection is a kind of injection attack used to read and modify user input that are sensitive data and information like phone numbers, addresses , credit card number , pins to exploit data and execute admin tasks on the databases, causing repudiation issues
PRECAUTION
To prevent SQLi attacks you should validate user input this process is also called input validation or query redesign. Apply prepared statements and parameterization ,apply patches and update system security, keep your read-access data limited . Each individual should be trained and aware about the risks associated with SQLi attacks.
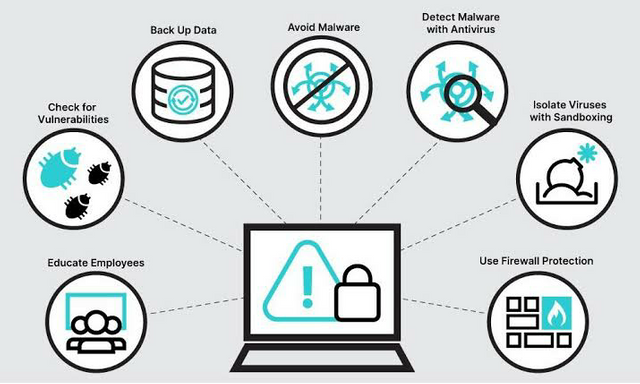
7.MALWARE
Malware attack is the most common attack ,also known as malicious attack. Malicious software is designed to exploit or extract data from any programmable devices for financial gain. Its installed secretly on someone's devices to get access to personal data and info and infect user's computer and to inflict harm on it in various forms. Ransomware, spyware, Adware, Botnet, Worm and Torjan horses are types of malware attacks.
PRECAUTION
Antivirus software should be downloaded on your device . Keep your security system updated,use strong passwords,enable multi-factor authentication. Only share information with official or trusted sites, if its absolutely necessary and investigate unusual or suspicious actions .
Hope you find it helpful
Thanks for reading:)
Regards,
@vvarishayy
@siz-official
#steemit

@cryptokraze | @arie.steem | @qasimwaqar | @vvarishayy | @suboohi



Good post dear friend please used the tag #steemexclusive in your post.
Thanks.
Regards, Faran Nabeel
Sure, thanks...!