Pre-installed malware on Android devices made $115k revenue in 10 days

From: HackRead
Check Point Mobile Security Team discovered a massive, on-going malware campaign that so far has claimed 5 million victims. Reportedly, the malware dubbed as RottenSys has managed to create a massive army of botnets comprising of 5 million mobile devices from across the globe.
The malware is hidden in a System Wi-Fi service application that is already installed-by-default on countless models of smartphones manufactured by prominent companies including Honor, Huawei, GIONEE, Samsung, Oppo, Vivo, and Xiaomi.
According to the blog post, Researchers believe that these firms cannot be held directly responsible for the malware and the devices must have been infected during supply chain phase. Probably the distribution firm or a rogue employee is to be blamed for the installation of malware.
It is worth noting that the affected devices were shipped through the same Hangzhou, China-based mobile devices distributor Tian Pai. However, the researchers are not yet sure if this particular firm has any direct involvement in the installation of RottenSys malware.
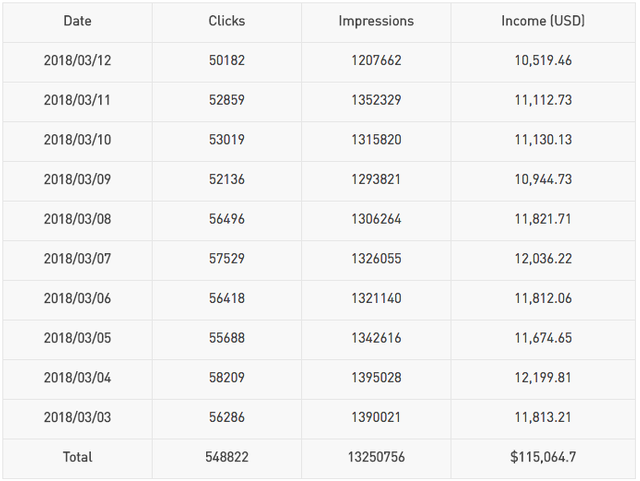
Check Point researchers claim that RottenSys is a highly sophisticated and advanced program that acquires almost all sensitive permissions on an Android mobile phone to perform its malicious acts. Such as it asks for silent download permission (DOWNLOAD_WITHOUT_NOTIFICATION permission), accessibility service permission and user calendar read access privilege. The campaign started in September 2016 and until March 12, 2018, it has infected 4,964,460 devices.
The fake Wi-Fi service app manages to evade detection by employing a submissive approach in the beginning and doesn’t instantly start its malicious tasks. Later, the malware dropper component communicates with its C&C server to receive a list of components it needs. The required component is actually the malicious code. The malware is capable of assembling an army of botnets and within only ten days attackers have made profits of approx. $115,000.
Read more: https://www.hackread.com/pre-installed-android-malware-made-115k-revenue/
It's interesting to think how often just one breach in a supply chain can impact so many brands reputation. Just sitting in wait for who knows how long, then turned on impacting so many. This is why you always flash/wipe everything before you start using it.
I use Internet Explorer on mine thou, So I'm Safe ;) lulz'~

 @millz to stay up to date on more great posts like this.
@millz to stay up to date on more great posts like this. 

 ㅤㅤ
ㅤㅤ .png)

Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
http://cyber.tn/?p=4643
It's referencing a previous article with scourses cited. so don't freak out. haha'~
You got a 19.23% upvote from @bid4joy courtesy of @millz!