True web security is possible and affordable for everyone, know Goldilock
As a result of the aforementioned problems, Goldilock is born, a revolutionary security system designed to solve the drawbacks associated with the theft of assets and information within the web, based on overcoming the inherent inherent flaws in current storage practices, ie storage per physical stay or virtual storage given by a centralized, decentralized platform or space in the cloud.
Coexisting in the NEO network Goldilock uses its Lock token to provide a gateway between the user and his wallet, performing certain verification processes without incurring IP gateways that provide some type of tracking and consequently commit such information to users or malicious systems.
The mechanics of Goldilock consist in the remote storage of information, which is lodged in a room that subsequently has to physically disconnect from the Internet until the user wishes to manage said data in a determined period of time. What this pseudo file suspension raises is the disconnection of the encrypted information nodes, partially hiding it from any malicious user who wishes to infringe security parameters, and this is due to the information limitation that this exercise offers, that is why that the notion of isolation in physical air space must guarantee security for users in general.
As a collateral effect of such effectiveness, the current market for cryptocurrencies must benefit from a substantial increase in investment given by a greater parameter of credibility before a healthy and safe exercise for all those who wish to be part of said economic system, since that the current practices not only generate distrust before the eyes of potential investors, in fact the fraud not only has to distort this economy, but also attacks the proposals of development and optimization that revolve around the blockchain technology and the low financing digital capital.
Unfortunately many of the most popular technologies today were conceived and financed as a result of the military and government use so the manipulation and obtaining of information under arbitrary practices are quantifiable facts and known today by the average user, however the free exercise among users has led to adopt this space in a more practical and beneficial way for all, being able to occupy large security parameters and optimization for our information in general, so that the technology "airgap" has to revolutionize the existing paradigms of security within the Web.
Goldilock has decided to make life within the NEO network, due to the modalities of action and benefit offered by this ecosystem in terms of security based on transactions under recognition and identification parameters, the formulation of intelligent contracts by interested parties in consolidating a a certain operation, adding to it the benefits that NEO offers by creating intelligent assets which must grant greater accessibility and speed when making transactions between users, practices that encourage a healthier exercise among stakeholders.
The inclusion of this new security technology in the various existing areas can be quite profitable, since many of the institutions in the financial, medical, educational, governmental, etc. sectors are susceptible to loss of information due to some natural phenomenon, due to the fact that The transition from the physical to the digital information format has not been fully realized due to the aforementioned security problems, which is why the proliferation of an efficient security system has to solve a large number of problems related to reliability, being a clear look to a future where the average user can make effective and practical use of the friendliest technologies.
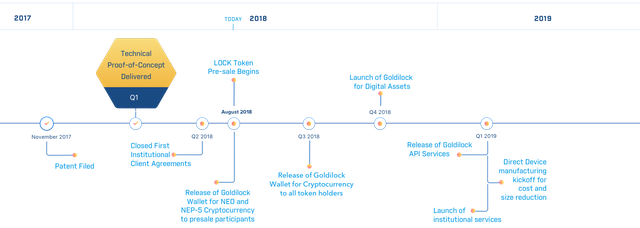
some of the images appended in the post are designs of my author
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Congratulations @guitartech! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
SteemitBoard and the Veterans on Steemit - The First Community Badge.
hi @guitartech
It has been a while since I've hear from you so I decided to check your blog and see if you're still around.
I've noticed that you're not very active lately. having a break? or did you give up on Steemit? (hope not)
ps. your post is already a bit to old to upvote it. till the next time :)
Yours, Piotr
Congratulations @guitartech! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!