GOLDILOCK: A SOLUTION TO DIGITAL DATA STORAGE PROBLEMS
INTRODUCTION
Since the onset of cryptocurrencies, the challenge of keeping wallets secure has always been the duty of the individual investor. This has resulted to the use of outdated, awkward and inefficient security measures to protect passwords and private keys. This is one of the main reasons why many institutions have been reluctant in adopting of crypto investments. To ease this problem, GOLDILOCK technology was integrated. Goldilock is a revolutionary digital asset security system which secure offline storage of digital assets combined with the convenience of securely accessing your assets at anytime from anywhere. The bedrock of Goldilock security suite is a remotely activated airgap security and patent-pending solution that is toggled by a non-IP command.
Goldilock is revolutionizing the way data is stored on the Internet by building an ecosystem to secure cryptocurrencies and digital assets for individuals and institutions. With a functioning platform launched in Q2 of 2018 that provides a remote physical disconnection of data from the internet, the Goldilock Security Suite leverages multi-factor authentication, biometrics, regressive technology triggers, and cryptography to shift the burden of keeping wallets secure away from the individual investor and on to our physically-segregated platform.
THE GOLDILOCK AIM
Goldilock aims at changing the way data is stored and secured across the internet. The Goldilock innovations allow institutions and individuals to secure digital assets in storage that lost connection to the internet until the immediate users want to connect it for its intended purpose.
THE VISION
Goldilock is based on the premise that your data should not be physically connected to the internet when you are not physically connected to the internet when you are not using it, but that it does need to be available to you from anywhere immediately when you want to access it.

SOME ISSUES ASSOCIATED WITH THE CRYPTOCURRENCIES AND SENSITIVE DIGITAL DATA STORAGE.
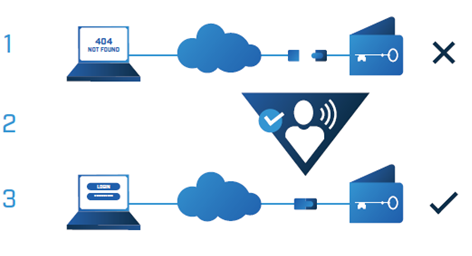
Most cryptocurrency investors and managers of sensitive digital assets are faced with the challenge of making use of either online hot wallet as a storage system which is easily hacked and denied of service or forced to choose personally-held hardware cold storage solutions, which can be stolen, hacked, misplaced, and destroyed. As a result of inadequate, Crypto key custody solution, both institutions and individuals continue to be plagued by frequent financial losses due to the mishandling of their keys.
Hot Wallet Storage Solutions
The hot storage solution is not suitable when it comes to key custody due to the fact that anything connected to the internet can be easily hacked. Thus, Goldilock is established on the idea that if it’s connected to the internet, it can be hacked. The past few years, over $1.2billion in Cryptocurrency has been stolen.
Traditional cold storage solutions
The Traditional cold storage solution is not suitable in the sense that it does not provide a suitable key management solution for investors. Secondly, Paper and USB keys can be lost, stolen, or damaged.

BENEFITS OF GOLDILOCK
Goldilock enhances security for the digital assets under their stewardship thereby providing services both direct to consumer and to institutions through the following ways:
- It provides an essential solution for institutions and Consumers seeking greater security solutions for their private cryptocurrency keys than currently available from third-party hot wallets and cloud-based data storage providers
- It provides an essential solution for consumers who require more global availability of private key custody than offered by physical hardware crypto wallets
- It provides an essential solution for Institutions seeking significant security upgrades for their users’ most sensitive digital assets.

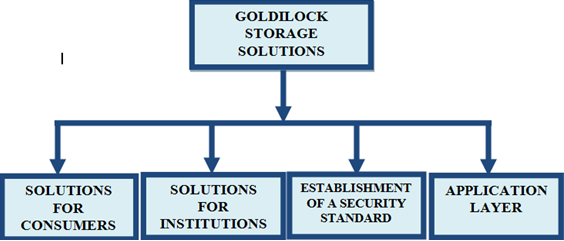
GOLDILOCK STORAGE SOLUTIONS
Private Key Custody
Goldilock provides individual consumers with an encrypted storage device in which information can be stored in a vault within a secure data center. Goldilock keeps the device offline until the customers chooses to access it.
Cryptocurrency Exchanges
Goldilock enables public centralized cryptocurrency exchanges which act as key custodians to reduce transaction processing times and enabling better handling of peak traffic periods during the inevitable market runs.
Online/Hot Wallet Operators
Goldilock has enabled hot wallet operators to leverage our remotely-automated airgap custody solution. In this case, Goldilock will rely on encrypted information flows to route requests, having no access to clients data.
Hardware/Cold Wallet Operators
Goldilock can be used by Cold Wallet operators to enhance their existing technologies, allowing operators to offer a more readily accessible, yet secure and remote solution.
Establishment of a Security Standard
Establishment of a security standard has sufficiently protected consumer data from persistent hacks of cryptocurrency exchanges, key theft, and misuse has cost billions of dollars.
GOLDILOCK Wallet for Cryptocurrency
Goldilock Core Development team have developed Goldilock Wallet for the purpose of storing and transacting NEO, GAS, and NEP-5 tokens; making NEO the most secure cryptocurrency on the Market.
Goldilock API Services
Goldilock Core Development team developed Goldilock API Services after the Goldilock Wallet with the main purpose of enable institutions that already have wallet solutions to make use of our patent-pending solution for their solutions that require improved security.

APPLICATIONS OF GOLDILOCK
The Goldilock technology can be applied in a wide array of fields. It can be used by individuals or larger institutions to store sensitive information.
Crypto Exchanges

The integration of Goldilock security’s core custody solution has made the crypto exchanges to become a more reliable and viable key custody solution by securing their users from the normal hacks and thefts incurred when traditional exchanges was the key custody solution.
Individual Remote Vaulted Wallet

The main priority of every cryptocurrency owner is to protect his/her confidential data and as well making it accessible. Goldilock has made it possible for your transactions not to be tampered with by keeping your private keys secrete and as well hide your sensitive operations inside your hardware wallet.
Secure Digital Vault

The integration of Goldilock has made it possible for the secure of sensitive information such as; bank account and credit card information, passwords, validated KYC information and identification documentation.
Credit Reporting Agencies

The application of Goldilock technology has bridged the hacks into credit account and credit identities by eliminating the need to have personal credit information online except in times when the owner of the credit information give instant approval for credit agencies to make it available for a certain period.
Banks

The application of Goldilock in the banking system has made it possible for banks to provide a safer and more convenient transfer they normally offer their clients by providing a secured solution for transfer management and bank account.
Digital Rights Managements

The application of Goldilock technology in digital rights management has enhanced the faster distribution of their contents by protecting and fighting against copyrights and unauthorized distribution of their production which in turns gives them the ability to control who sends and receives their publications.
Health Care Records

The Goldilock technology can be applied in the healthcare communities by making it a goal to improve the ability for patients and healthcare professionals to securely share data while protecting individual rights which was not possible with technological innovations.

LOCK TOKEN
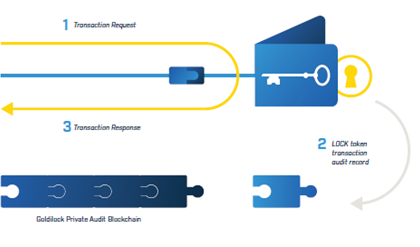
LOCK tokens allow for the storage of private keys for cryptocurrencies and other digital assets using the Goldilock’s proprietary smart contract logic
The LOCK token is required to access the Goldilock Wallet. When the user logs into the Goldilock Wallet, the Wallet will query the NEO public Blockchain to confirm the user’s public key address owns a LOCK token. If the user’s public key address owns a LOCK token, then the Goldilock Wallet will launch in the user’s browser. When the user is granted access, the Wallet will write audit information to our own Private Audit Blockchain. These audit entries will ensure that every time your private key is brought online, this access is written to immutable storage that can be queried from the Goldilock Wallet.
LOCK token allows Goldilock to provide users with a record of their node activity, while keeping user-owned data encrypted and locked away even from everyone including the Goldilock team. In addition, LOCK is to be the accepted method of subscription payment for individual users on the Goldilock Security Suite.
It is our intention to initially support NEO, GAS, and NEP-5 tokens in an effort to transform NEO into the most secure cryptocurrency available today. This step will be the precursor to platform expansion with the inclusion of other mainstream and alternative cryptocurrencies.

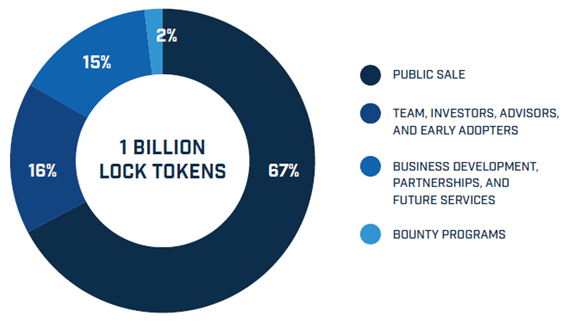
TOKEN ALLOCATION
Goldilock will allocate the LOCK tokens as follows
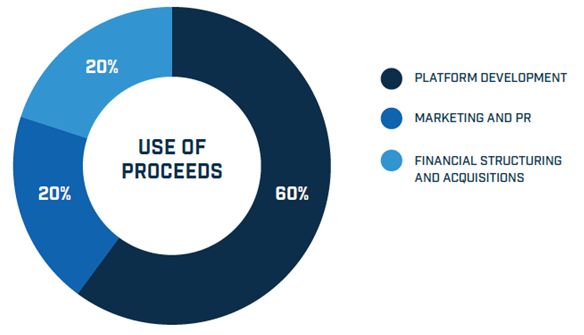
USE OF PROCEEDS
Funds will be allocated to continue company operations in the form of proceeds gotten from token sales.

NEO
Goldilock chose the NEO network for the LOCK token due to our alignment with their vision and philosophy on the future of blockchain. Their focus on Governance and Compliance, Digital Assets, Digital Identity, and Smart Contracts provide a solid base for the Goldilock Security Suite. In addition, their investment in ecosystem and community ensure that NEO will be able to meet the needs of its developers and consumers as the platform evolves.

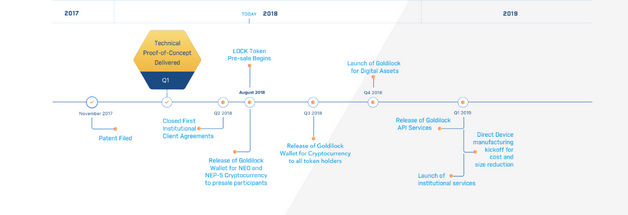
THE GOLDILOCK ROADMAP

CONCLUSION
The Goldilock technology was developed to bridge the gap created by other methods of storing and securing personal data across the internet which has proven ineffective time without number. Goldilock technology has achieved that by taking your personal data and cryptocurrency keys offline thereby protecting them from hacking.

THE GOLDILOCK TEAM
For more information watch this short feature intro:
For More Information & Resources:
Goldilock Website
Goldilock WhitePaper
Goldilock Tokenomics
Goldilock Telegram
Goldilock Discord
Goldilock Linkedin
Goldilock Facebook
Goldilock Twitter
Goldilock Reddit
Goldilock Github
Contest link
twitter link
goldilock2018



This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Excellent article. I learned a lot of interesting and cognitive. I'm screwed up with you, I'll be glad to reciprocal subscription))
Congratulations @kelemasco! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPCongratulations @kelemasco! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!