Phishing With Ngrok
Phishing with Ngrok
Ngrok is an amazing application for securely tunneling you local port/service from a public url.
How to pronounce Ngrok?
en-grok
How it works?
It connects to the ngrok cloud service which accepts traffic on a public address and relays that traffic through to the ngrok process running on your machine and then on to the local address you specified.
Pros
You don’t need to configure port forwarding on your routers or waste time setting up dynamic DNS solutions like No-IP.You can protect the access by providing creds like password & share only with the desired person/client.You can tunnel almost every TCP connection*Ngrok does not log or store any data transmitted through your tunneled connections.I belive there are many advantages of using ngrok, but I found above pros fascinating.
Cons
It actually generates a public url randomly & if you want a custom url then you need to buy basic/pro version for custom domain or whitelabel domain. I can’t think of any other cons.Example: https://d03f2b92.ngrok.io
How Ngrok plays a vital role in phishing?
As we all know phishing is a way or method to steal creds like password or credit cards details. By default Ngrok securely tunnels your communication using SSL/TLS. Novice user usually trust HTTPS more than their life, using Ngrok we can abuse it. See the below example.
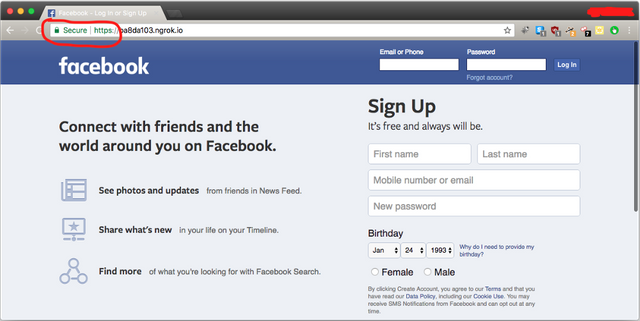
As you can see the above phishing page of Facebook, it’s using HTTPS. For a novice user, it’s a secure site, to them secure means legitimate site. The moment they input username & password it will be delivered to attackers machine in clear text. See the below example
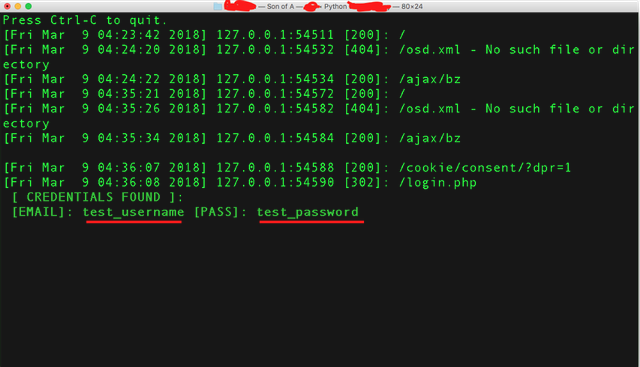
Demo
Let’s quickly do a demonstration on Phishing using Ngrok. To perform this either you can use setoolkit a.k.a Social Engineering Toolkit, developed by Dave kennedy @hackingdave. Host your phishing pages locally using Apache & php. If you don’t want to do complicated stuff then you’d try this amazing automated tool called SocialPhish, developed by @A1S0N_ (Alisson Moretto). SocialPhish is cross-platform, you can install this on macOS or Linux. Just hit the git page of SocialPhish & look for requirements. On Kali Linux it runs smoothly, I suggest you to try it on Kali. I tried it on macOS as well as Kali.
Even tho if you try to anayle the URL using VirusTotal, only Spamhaus detected this URL as Phishing.
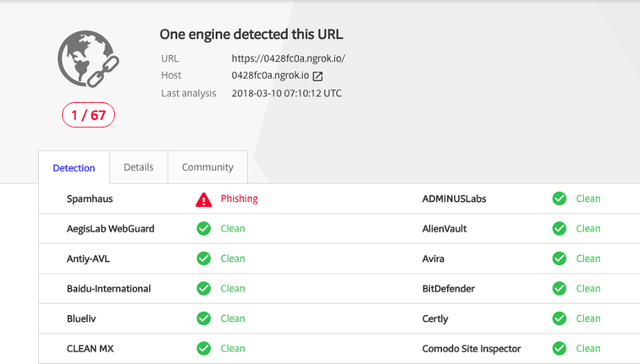
I’ve tried with other phishing analyzers, everytime I got negative result. If you have any other analyzing websites then let me know.
Then, how to detect?
- Check for web address, make sure it’s that website only which you are willing to visit.
- Do not click, I repeat, DO NOT CLICK ON LINKS, without analyzing. If you click, then check address bar.
- Use VirusTotal or IsItPhishing websites to analyze url.
- Check for SSL/TLS certificate
- If you think it’s phish page, then give false information first & wait for it. Hopefully it accepts your false information & redirects to original website*.
If you find any new ways to detect phish pages, then drop a comment here. If you have any suggestion or anything just drop here.
*Try it on your own risk.
Disclaimer: TO BE USED FOR EDUCATIONAL PURPOSES ONLY
Congratulations @g33xter! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!