You are Being Tracked - Real-time Cell Phone Location Data Leaked
This week, I learned about a company called Securus Technologies who has a service that allows users to obtain real-time cell phone location data for essentially all US cell phone users, and likely most of Canada's cell phone users as well. Not surprisingly, this service has allegedly been abused by a former Mississippi County, MO Sherriff to track people including fellow law enforcement officers and a judge. The data that Securus uses in it's service is obtained through a company called 3Cinteractive who gets the data from a California based company called LocationSmart. LocationSmart purchases the data directly from all major US and Canadian cellular carriers and re-sells that data to government agencies and corporations.
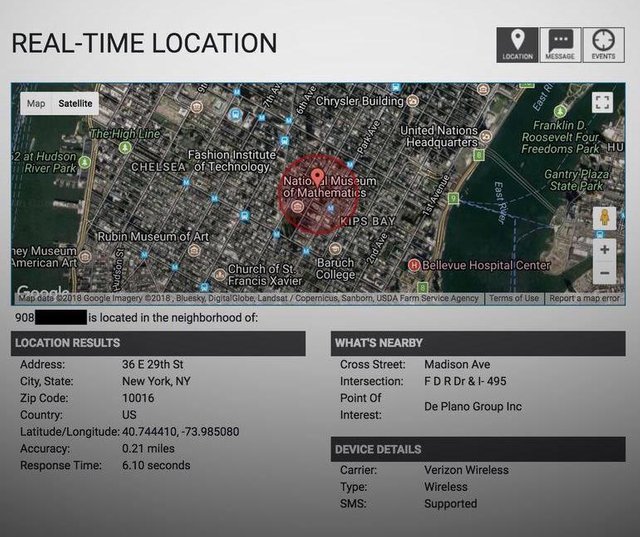
The data that LocationSmart buys from carriers is the tower-based triangulated location of your device. It is accurate to a few hundred meters, so it isn't as accurate as GPS data coming directly from your phone, but that is what makes it more sinister. It doesn't come directly from your phone, so there is no way to opt in or opt out. It comes directly from the carrier whether you grant consent or not. This is bad enough, but it gets worse from here. On May 16th, Robert Xiao, a Ph.D. candidate at the Human-Computer Interaction Institute at Carnegie Mellon University discovered a security vulnerability on LocationSmart's self-service web portal which allowed unfettered access to this location data without any authetication or consent. The web portal was used as a live demonstration where a user could find the location of their own cell phone in order to demonstrate the accuracy and efficacy of the service. Xiao reported the vulnerability to US CERT and publicized the vulnerability via Brian Krebs' website after the portal was taken down by LocationSmart.
Here is a timeline of the most pertinent events to this story:
May 8 - Senator Wyden Demands Investigation
Oregon Senator Ron Wyden sends letter to FCC Chairman demanding investigation into "abusive and potentially unlawfull practices of wireless carriers." Here is an excerpt from Wyden's letter to the FCC:
I write to ask that the Federal Communitations Commission (FCC) investigate abusive and potentiall unlawfull practices of wireless carriers, which have permitted at least one company to provide law enforcement with unrestricted access to the location data of the carriers' customers.
Here is a link to the entire letter.
He also sent letters to all major US wireless carriers demanding that the carriers take steps to prevent things like this from happening in the future. From Wyman's letter to Sprint:
I am writing to insist that Sprint take proactive measures to prevent the unrestricted disclosure and potential abuse of private customer data, including real-time location information, by at least one other company to the government.
Here is a link to the Sprint letter.
Here is a link to the Verizon letter.
Here is a link to the AT&T letter.
Here is a link to the T-mobile letter.
May 10 - New York Times Publishes Securus Story
Jennifer Valentino-DeVries New York Times story exposes the Securus service and sheds light on the state and federal cases against former Mississippi County, MO Sherriff, Cory Hutcheson. The story also raises questions about the embarrassingly outdated laws regarding the data that wireless service providers collect about their users and what they are allowed to do with that data.
May 16th - Xiao Discovers Website Vulnerability
After reading Valentino-DeVries story, Xiao was poking around on Location Smart's website when he stumbled across the vulnerability.
I stumbled upon this almost by accident, and it wasn’t terribly hard to do,” Xiao said. “This is something anyone could discover with minimal effort. And the gist of it is I can track most peoples’ cell phone without their consent.
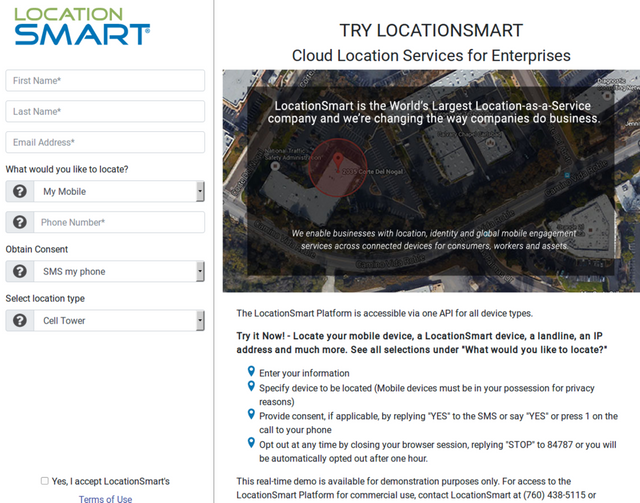
Here is how the portal was supposed to work:
- A user was prompted to enter the cell phone number for which they desired the location (presumably their own phone)
- A text message was sent to the number that the user provided which asked the user to consent to the location tracking
- After consenting, the user was sent another text message which included their location information
The vulnerability, however, allowed direct access with the API which allowed Xiao to gather the location data of any phone number without the need to "opt in" via the text message consent.
Here is a link to Xiao's technical write-up.
May 17th - krebsonsecurity Publicizes Vulnerability
Brian Krebs published his story on the vulnerability after being tipped by Xiao. He also makes the point that consumers have very little protection regarding this type of data.
This is precisely why we have lobbied so hard for robust privacy protections for location information, says Stephanie Lacambra, a staff attorney for the Electronic Frontier Foundation. It really should be only that law enforcement is required to get a warrant for this stuff, and that’s the rule we’ve been trying to push for.
Today, the laws regarding whether law enforcement needs a warrant for this type of data differs from state to state.
The law here is really out of date,” stated Chris Calabrese, VP for the Center for Democracy and Technology. “But I think any processes that involve going to third parties who don’t verify that it’s a lawful or law enforcement request — and that don’t make sure the evidence behind that request is legitimate — are hugely problematic and they’re major privacy violations. I would be very surprised if any mobile carrier doesn’t think location information should be treated sensitively, and I’m sure none of them want this information to be made public. My guess is the carriers are going to come down hard on this, because it’s sort of their worst nightmare come true. We all know that cell phones are portable tracking devices. There’s a sort of an implicit deal where we’re okay with it because we get lots of benefits from it, but we all also assume this information should be protected. But when it isn’t, that presents a major problem and I think these examples would be a spur for some sort of legislative intervention if they weren’t fixed very quickly.
The fact that users are not allowed to opt out of this is a travesty. Let's hope that the carriers not only come down hard on these types of companies, but let's also hope that there is enough public outcry about this incident to get the carriers to take a closer look at their policies and practices of selling our data to the highest bidder. If the staus quo remains, and 3rd parties continue to be allowed to expose this data, I will not be surprised to see more user data exposed in the future.