Wikipedia Report--Blockchain / Cipher Block Chaining

Image from google images, labeled for reuse: Original Link
Note:
This article is of the form Wikipedia Report and it is a method used to facilitate the assimilation of researched information into a working understanding which is analogous to the classic Book Report from grade school. I won't necessarily be using Wikipedia exclusively but of course it is the starting point of choice for quick research, (If you have an opinion about a better method please let me know, I am endeavoring to ingrain good researching habits & any assistance would be greatly appreciated) simply because of the sheer scope of topics covered.Cipher Block Chaining (CBC)
What is Cipher Block Chaining? Well, first off what is Block Chaining?
From Wiki--A blockchain (originally block chain) is a distributed database, where each sequential data block in the chain has a timestamp and a link to the previous block.

Figure 1: blockchain (From Wiki
The article goes on to say that blockchains are inherently resistant to data modification, once the data is written is cannot be modified (it is set in stone if you will). There is a caveat to this: occasionally concurrent validation can occur, resulting in a fork, and which ever branch ends up becoming the predominant one causes the other branch to be orphaned (a feat exponentially more likely with increasing chain size of the branch). Eventually the blocks which become orphaned are culled from the blockchain, therefore it is not always set in stone. (From an article on bitcoin this is sometimes done on purpose as a result of a type of hacking/attack called transaction reversing; however this requires serious hashing power).
The blockchain data structure allows for decentralized ledger keeping and solves the problem of double-spending. The use of a blockchain in software architecture is an example of using a distributed database. The chain primarily grows linearly with occasional forking, and subsequent orphaning. Loss of communication between computers participating in the blockchain can cause forking as well, which would result in a great deal of data loss when one of these long chains became orphaned after re-uniting the segregated computers. This is the technological basis for bitcoin (and Steemit as well).
Interestingly enough the blocks themselves are composed of individual transactions encoded in a Merkel Tree data structure. (Okay this is probably why my colleague asked me to research Merkel Tree and Cipher Block Chaining)
Okay, now on to Cipher Block Chaining:
Cipher block chaining--Would this would be a blockchain utilizing a block cipher? (which is a form of text encryption where all the contiguous bits in a block are operated on by a cipher key and an algorithm at once, as opposed to bit by bit, as in a stream cipher [Ref 1])
Actually, no... it isn't as simple as concatenating terms and nesting definitions in this case. Rather it seems a more correct way of describing this is that is is a mode of operation of a block cipher, where an initialization vector of a certain length is employed, it also characteristically uses a chaining mechanism that makes the decryption of a block of cipher text to depend on all preceding cipher text blocks. [Ref 2] The error of a single bit affects the decryption of all later blocks, and decryption of the blocks in the wrong order results in data corruption. During encryption, each plaintext block is XOR'd with the immediately preceding block, then encrypted...
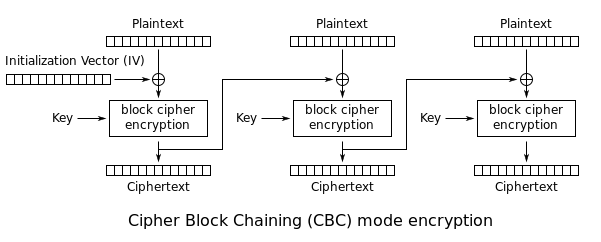
Figure 2: CBC Encryption (from Wiki
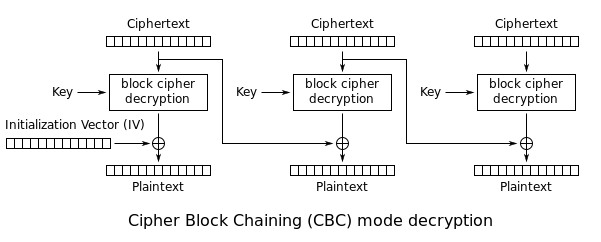
Figure 3: CBC Decryption (from Wiki
Okay, well... I would like to clear up the definitions of the emboldened text (which isn't already mentioned), in a list format:
- Initialization Vector--From Wiki
In cryptography, an initialization vector (IV) or starting variable (SV) is a fixed-size input to a cryptographic primitive that is typically required to be random or pseudorandom. Randomization is crucial for encryption schemes to achieve semantic security, a property whereby repeated usage of the scheme under the same key does not allow an attacker to infer relationships between segments of the encrypted message. For block ciphers, the use of an IV is described by the modes of operation. Randomization is also required for other primitives, such as universal hash functions and message authentication codes based thereon. - XOR--From [Ref 3]
This is just like logical OR except in the case of true XOR true, which evaluates to false. - Cipher Text
This is the original text data which becomes encrypted into blocks. - Cipher Key--From Wiki
The operation of a cipher usually depends on a piece of auxiliary information, called a key (or, in traditional NSA parlance, a cryptovariable). The encrypting procedure is varied depending on the key, which changes the detailed operation of the algorithm. A key must be selected before using a cipher to encrypt a message. Without knowledge of the key, it should be extremely difficult, if not impossible, to decrypt the resulting ciphertext into readable plaintext.
Okay, well now I feel that I understand the ideas a bit better, at least enough to implement them with reference back the schematic figures, :-). I feel that the disambiguation resulting from including the paraphrased description of blockchain outweighs the cluttering effect of it being only somewhat related to CBC (Cipher Block Chaining).
In conclusion, I now understand these technologies better, and I hope I didn't make too many mistakes, Thank You for reading this and please comment if I got something wrong... Until next time!
Hacking made easier..
Need access to keep an eye on your spouse by
gaining access to their emails,phone?
Do you want to know what your kids do on social networks?
*email hack.
*Criminal record erasing
*Clear Your credit scores,
*Keep Tabs On Your Employee....we can get all work done ,100% legit
contact us via email @ [[email protected]]