QREDO MPC Security for Digital Assets - Rendering stolen data useless to hackers
With Blockchain technology being implemented into a wide range of industries, safe private key management is now facing a big challenge. In contrast to Blockchain’s whole concept of ‘decentralization’, private keys are kept and stored by individuals. It’s led to many serious problems and risks such as loss, theft, destruction, etc. Therefore, to prevent such issues, it’s necessary to understand high-level encryption technologies for safe key management such as Multi-Signature (a.k.a. ‘Multisig’) and MPC.
It is also notable that MPC signature has been receiving more attention than other encryption-based signing technologies, and thus leading to this blog post explaining how MPC and One asset security platform that is at the forefront of MPC technology is QREDO

1: About Qredo ????
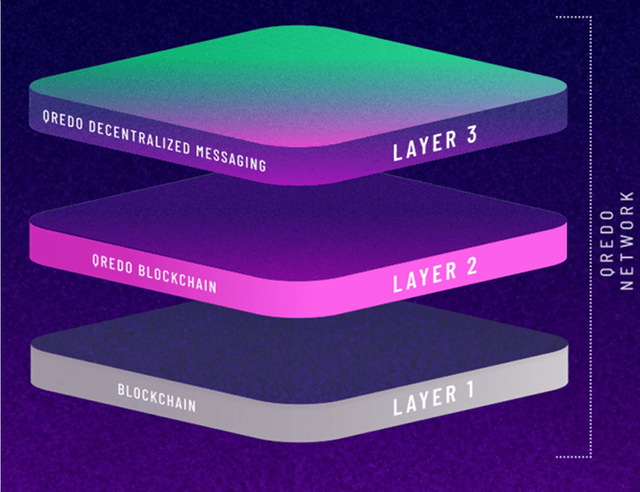
QREDO is a decentralized custodian who facilitates other essential blockchain features like cross-platform liquidity, interoperability, and faster cross-chain settlement. Qredo, a Layer-2 protocol based on Tendermint, also features a Layer-3 decentralized communications platform (based on Matrix, a decentralized messaging protocol). One of the salient underlying features of Qredo is the use of Consensus-Driven Multi-Party Computation (CD-MPC) to provide asset security. Qredo’s blockchain is a Proof-of-Stake (PoS) chain. The project aims to decentralize the governance of its network progressively.
QREDO Network aims to offer the following key features:
Institutional-grade security and controls.
- Cross-platform credit and liquidity.
- Cross-chain atomic swaps and settlements.
- Progressively decentralized governance and compliance.
- Interoperability in an open-source way.
2: What is MPC (Multi-Party Computation)?
To utilize your digital assets, you need a public key and a private key; your ability to safely hold and transfer the asset itself is only guaranteed as long as the private key is safe. Once that key is in someone else’s hands, they can transfer the assets to their own wallet. Therefore, preventing the theft of private keys is crucial to maintaining digital asset security.
In a general sense, MPC enables multiple parties – each holding their own private data – to evaluate a computation without ever revealing any of the private data held by each party (or any otherwise related secret information).
- Privacy: The private information held by the parties cannot be inferred from the execution of the protocol.
- Accuracy: If a number of parties within the group decide to share information or deviate from the instructions during the protocol execution, the MPC will not allow them to force the honest parties to output an incorrect result or leak an honest party’s secret information

3: Why Rendering stolen data is useless to hackers when using qredo
From the private key controlling the digital assets, Qredo's MPC protocol generates multiple independent secrets which are then distributed between MPC Nodes on a fast-finality blockchain.
Each MPC node is housed in a security-hardened tier 4 data center. These data centers are distributed across financial hubs around the world, from London to Chicago and Hong Kong.
When an asset owner wants to sign a transaction or generate a public key to make a deposit, they coordinate with their appointed custodians via the Qredo network to confirm the asset ownership on the blockchain, creating a consensus that enables the asset owner to invoke the MPC Nodes to run the MPC protocol from their Qredo wallet.
This protocol then generates a public address for digital assets to be deposited, or a digital signature for the underlying blockchain to send or receive digital assets from that address.
Qredo's MPC implementation distributes private key shares over a decentralized blockchain network, completely eliminating the single point of failure. Each MPC Node on the network has its own secrets. But the loss of a single secret doesn’t give an attacker any advantage in gaining control over the digital assets.
Instead of hacking a single machine and walking away with the private key, a hacker would need to compromise all the machines in the MPC Network, and each MPC node is housed in a high-security tier 4 data center.
If an attacker tried to gain unauthorized access by physically tampering with the MPC node, the keys used to encrypt the hard disk drive would self-destruct, permanently locking access to the operating system.
Read the details here
4: Qredo is built by a uniquely talented team
Qredo boasts a world-class team of cryptographic wizards, startup veterans, legal specialists and blockchain developers with decades of combined experience.

Secure Key Management is a challenging task for even the most sophisticated practitioner. The prevalent digital asset custody solutions in use are 1) self-custody, 2) exchange wallets, 3) third-party wallets and custodians. These options are, for different reasons, problematic to end-users. For instance, self-custody is challenging when it comes to digital assets. Even the improved versions like multi-signature or threshold signature schemes may present drawbacks. Exchange wallets and third-party custodians are trusted parties exposing clients to counterparty risk. The DeFi for Institutions Insight Report published by Consensys identifies several needs and challenges common to all institutional investors irrespective of their size. The Report conceptualizes such needs and challenges by way of a pyramid. At the base of this pyramid lies security, which is the need for safe custody. Qredo could address these concerns with the help of CD-MPC.
Author:
Telegram: lovetokengg