Warning about phishing links
Lately, I have been seeing a lot of posts getting comments from bots or some random dude who can't even write proper English, I can hear you saying "But Deathwing, this always happens, it is not something new" but there is one caveat in those comments.
All of them have a link, a link that seems similar to steemit.com or any other big sites such as busy but in fact, it is not.
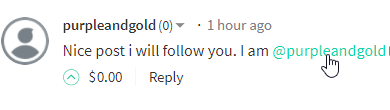
In this picture, you can see the user posted a link with a normal spam message you say? But in fact, it's not a link to his "usual" profile, well... It is. But not on Steemit. More on that later.
What is Phishing
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication.
Wikipedia
Phishing is pretty much a way of scamming, stealing your private information. Most importantly, your private keys or passwords here on steemit (never, ever use your password to login, always use a posting key on a daily basis. ONLY use active key when you are verifying stuff (well, transactions in this case).
Alright, back to the "link" thingy.

As you can see when I hover over the link, you see "sleemit.com" so, what is the difference?
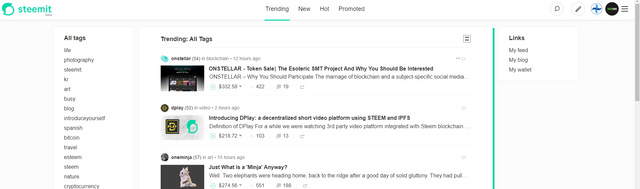
This image is taken on Steemit.com, as you can see; I am completely logged in with Steem Plus active.
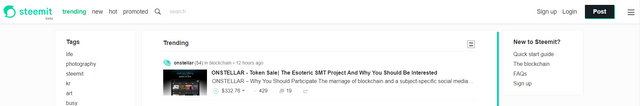
And this is Sleemit.com, I am no longer logged in and Steem Plus is not active anymore. I am not on Steemit anymore, but the site looks EXACTLY like Steemit and works like it. So this is the phishing right here. As an innocent user, you would think you just "got logged out" and would instinctively log back in once again.
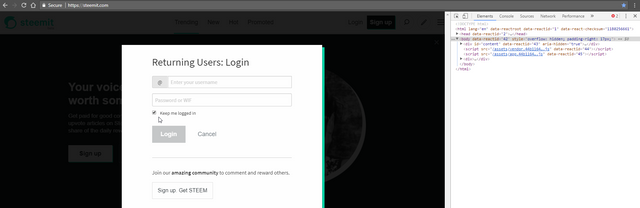
You see the normal login page of Steemit, and only a few scripts are running
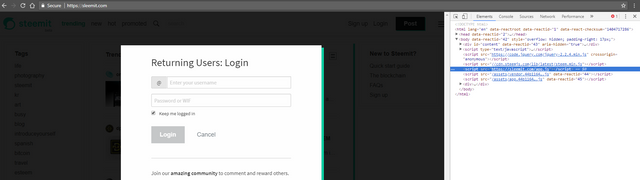
And there you go, this is Sleemit's login page. A few extra scripts right there and the most notably, app.js which is the javascript file they use to steal your passwords as soon as you log in.
Ways to prevent this:
Always check the link you are clicking to
Install the Steem Plus extension made by @stoodkev as it will warn you whenever you are clicking a link that directs you out of steemit.com
Don't click the links at all if they are posted by low rep users, or have no meaning.
TLDR: Never click a link before checking where it redirects you to. Especially on Steemit. Otherwise you will have your password stolen, your account and your money gone. Always have Steem Plus installed.
P.S.: The site and the user I shared here were completely out of coincidence, during my observations for the past few weeks I know that there are more than 15 maybe 20 phishing sites available on the internet just to steal your passwords.
Nowadays it's a lot more easier to hack individual accounts than the institution. It's all about "Social Engineering", and the only way to counter it is common sense and education. You can check my blog post about it: https://steemit.com/steemit/@cortexx/how-to-protect-yourself-from-hackers-or-social-engineering-or .
I agree. Hackers are trying to exploit people in any way possible.
I make it a point to downvote those type of accounts whenever i see spammy posts.
Yep, when security gets too tight, they have to go for the individuals instead.
Honestly, the site shown in this post is scary in terms of how good it is. Most scam sites are not quite as good at matching the real site.
That's dope.
Man they are trying like crazy. Just you should never click on anyone asking you to follow or whatever
Nice advice please follow me via this spotlessben
yes sir @deathwing, i also get comments on my post 6 hours ago from purpleandgold account. I am very worried about this. certainly not just me but comrades who have long existed in this platform. we should now be very careful, whether we can know the account is a danger? I mean other than sending a link on our post?
good info thamkyou!

Thanku soo much sir for this information
They're also sending tiny amounts 0.001 steem to your wallet with a message and phishing links. Don't click!
if the browser is uptodate a https will be enough
also why not clicking on the name rather than the link? ;)
Very interesting find. Very sneaky form of attack. Scary thing is it is so easy to register a domain name and even SSL certificate these days. Also scary because anyone can pretty much run a frontend for condenser, but it is hard to know if the site is trustworthy or not. Thanks for the article, I find this kind of thing super interesting. Will be following you.
Some of the guys that do phising like do make use of url shorteners to hide the actual link. Or from what I could tell in your post they used steem markup to disguise the actual link. In the case where the use a url shortnerer for example tinyurl then you can actually check what the link redirects to by making use of curl. You can do it like this:
See the output. The actual url it redirects to is in the "Location" section in the response.
This link for example was a tinyurl link for the video:"Rick Astley - Never Gonna Give You Up". Haha I got you!
Anyways tinyurl has a feature where you can take any link shortened by tinyurl and preview it by prefixing tinyurl with "preview" like this: https://preview.tinyurl.com/2fcpre6.
Just take in mind that tinyurl is one of many sites that people could use to shorten a url. Twitter even have their own site that they use to shorten any links posted on twitter. My curl trick should work on almost any url shortener, but if you aren't that technical I would suggest that you try:
http://www.checkshorturl.com/ which you can use to check shortened urls. For example I did a check for this url that was shortened by twitter's url shortening service: https://t.co/LGaAniJH32
Something you can also do if you aren't sure if a frontend/site other than steemit.com is legit or not is to use security related reputation checking site to check what other people have to say about the site. Here is a list of sites you can use to check if the site is flagged as malicious by other users or not:
https://www.threatcrowd.org
https://www.virustotal.com/ (It has a feature to check a url and there is a very handy comments section)
https://www.phishtank.com/
(Btw I check sleemit.com and its not mentioned on any of these sites yet , unfortunately).
These are some really nice resources to know about. I myself have clicked on a redirecting phishing link on here but it is worrisome especially for those who don't have a good idea about how front-ends interact with the blockchain.
Anyone can build their own Steemit-like front-end, that's not a problem at all as it can be totally legitimate without needing Steemit to sanction it, but knowing who to trust when it's not Steemit or doesn't use Steemconnect is tricky. It's nice that there are easy technical and user friendly options out there to check but yeah, keeping an eye out and protecting yourself starts to get a bit more serious in decentralized systems.
You can maybe ask these guys:(Who wrote this blog post)
http://blog.thinkst.com/p/canarytokensorg-quick-free-detection.html
To add a honey/canary token for steemit active or posting keys to their site. Which would enable you to see if somebody tries to use a fake made up posting or active steem key that you posted to a frontend, the site emails you if someone tries to use the details that you generated on: http://canarytokens.org/generate
Hope that makes sense? Maybe somebody needs to make a site to track the reputation of steemit frontends.
Be careful what you are clicking on. If it runs javascript then it can do a great deal on your computer, for example people can even go so far to open a shell on your computer using javascript. This is something that people do often when they exploit xss attacks, but if you are willingly visiting a site then they don't even need to trick you into running the javascript.
You can see more about this type of attack here:
https://www.slideshare.net/BartLeppens/owasp-appseceu-2015-beef-session (See from slide 49)
Thanks for your feedback on my comment!
Awesome stuff again, especially those canary tokens. I'm not sure how exactly it could be implemented, but I can see maybe some sort of interesting key-specific decryption of a picture like they were talking on a website that logs use automatically. Not sure how that would work on attacker's own websites or even Steemit though. Interesting to think about.
And yeah, I even read somewhere that web javascript could exploit those Spectre and Meltdown vulnerabilities. I just love it because it runs so easy... everywhere.
Stop phising
Excellent thank you for the headsup daethwing