Trivial Defeat of Smart Locks
Abstract
Smart Locks are a new addition to modern physical security systems, which implies an onboard MCU. Just because a lock has an onboard MCU does not necessarily make it “Smart”. The concept of using biometrics to create a secure lock coded to a specific individual or group of individuals, which I will generally refer to as a Smart Lock, suggests a very high level of impenetrability. Even with the use of a code keypad and facial recognition, I will show that Smart Locks having an onboard MCU take less time to defeat than to legitimately activate, unless it has been specifically designed to resist this kind of attack, and how it is done, which includes a trade secret. I will show that the apparatus to defeat a Smart Lock is ubiquitous, the method of defeat is trivial and that a good old fashioned brass key is more secure.
Introduction
The most advanced Smart Locks may require a finger print, a voice print, facial recognition and a passcode, which is sometimes referred to as a biometric lock. It is well know that biometric locks are easy to crack with easily obtained data. Methods to defeat biometric locks are rife on the Internet. [4] [5] A cell phone can take a picture of the individual and record that individuals voice. A small piece of adhesive tape can be used to obtain a copy of that person’s finger print from any object they have touched and transferred to a false finger. When approaching the Smart Lock, the photo on the cell phone can be used for a facial recognition match, the recorded voice on the cell phone can be played for a voice match and the false finger can be placed into position to match the stored finger print. That is why a code keypad is often installed. It is the entry code that slows down the intruder, not the biometrics. There are even devices available to fabricate fake fingers and hands specifically for this purpose. Search the Internet for “defeat biometric locks” and you will be buried in references.
All of the biometric data must be collected by stealth with a minimal amount of stalking. The common belief that this type of information is difficult to obtain is fantasy. The most difficult piece of data to obtain is always the passcode. However, none of this matters since the method of attack on Smart Locks requires no data and is accomplished with a ubiquitous device that is easily concealed providing a trivial defeat in seconds with the swipe of a hand.
History
The hand held device with spiral antenna shown in Figure 1 and Figure 2 was developed by a company in China to defeat Smart Locks. The original video clearly shows that the handheld device defeats many varieties and models of Smart Locks, but not all of them. The method of attack is shown in Figure 1 and a clear image of the actual device in Figure 2. [1] The video shows many different locks being opened in seconds with the swipe of a hand like a magic wand. Figure 1 is a screen capture from that video.
Figure 1 shows a handheld device with a transistor in a TO-220 case right at the base of the spiral antenna. While the button is pushed, a little blue light flashes as the device is swiped across the front of the lock. In all cases where the lock opens, it resets in a safe condition so that the lock is opened by turning the handle.
The video shows many different locks from a variety of manufacturers that are easily defeated in seconds using this device. The device was sold online and was so successful at breaking locks that it was banned by the Chinese government and is now illegal in China.
Figure 2 shows a clear view of the device and its antenna. It looks like a transistor radio with a piece of hand wound wire in the shape of a spiral coming out of the top and a momentary button switch on the side. There is no RF spectrum available for this apparatus shown and it would appear, from the video, that the operators do not really know the mechanism that makes this open Smart Locks. It just works.
One sequence in the video shows the use of a walkie-talkie to open some locks. That sets the frequency range for interference on some of the Smart Locks that are susceptible to that kind of narrow band RF. Some of the waveforms that open some of the locks are shown on an oscilloscope. This is not really how interference compatibility is handled in a professional laboratory. It other words, they have no professional knowledge of RF compatibility engineering techniques. So, they are probably just guessing.
How to Defeat Them
Clearly, the successful device, shown in Figure 2, is using RF interference to cause the onboard MCU chip in the Smart Lock to reset. All commercial electronic locking devices must reset into the open or safe condition to prevent obstruction or the door removed by its hinges or demolished in the event of fire and other anomalous events causing the onboard electronics to malfunction. Sometimes, electronic components just wear out and fail. All that is necessary to defeat the Smart Lock is to find the correct frequency or set of frequencies that will cause a device reset. A set of electronic RF instruments is necessary to sweep a very broadband RF frequency range and transmit that signal using a high power linear RF amplifier that is connected to a broadband RF antenna. This is one method of dealing with RF interference compatibility measurements.
RF interference is part of a specialized electronic engineering field usually studied in graduate school. A typical text book on the subject covers all aspects of radiated and conducted emissions. [2] Many electronic devices are required to meet certain standards related to resistance to interfering RF radiation and limits on what the device can radiate by itself. Government agencies, such as the FCC in the US, regulated these standards. The question is what range of frequencies and power will cause a Smart Lock to reset and what equipment is needed to make that happen. All of the major semiconductor manufacturers publish documents regarding their MCU EMP resistance, which are not referenced to avoid any manufacturer bias; ask your favorite vendor.

The first inclination is to get a high power linear RF power amplifier, such as the one shown in Figure 3, that is designed to be compatible with SDR transmitters. It measures 250 mm x 185 mm x 165 mm. This particular amplifier has a bandwidth from 20 MHz to 2.7 GHz and a continuous power output of 15 Watts. The output of that amplifier is connected by a suitable RF cable to a broadband antenna, which is usually some kind of bilog antenna. The input can be one of the new generation SDR transmitters, which has a similar bandwidth, that is controlled by a PC computer, which can be a laptop. The laptop, SDR and RF power amplifier all require power supplies. None of this is dimensionally small with a total price that can exceed US$5,000. It takes an RF engineer or specially trained technician to hook it all up and operate it. The problem with this equipment is that it is known to work only on a few devices.
This sophisticated RF equipment is not convenient for a would be intruder. The intruder needs something small enough to be put into his pocket and just push a button on demand. The linear RF amplifier approach is not realistic for intrusion despite the obvious practical use in a laboratory setting for scientific and engineering purposes. The intruder just wants to open the door quickly and quietly.
We know that the handheld device in Figure 2 works just fine on many locks, but not all of them. So, why does the handheld device work better than the laboratory equipment? What is the difference between that device and the linear amplifier equipment? The clue is in the blue flashing light in the video. It is a spark connected directly to the spiral antenna.
The Trade Secret
The original device used by the Chinese resembles an adaptation of an electric fly swatter, an electric arc generator. The company that made the first Smart Lock breaker says they used a Tesla coil, but then proceeded to specify a single frequency, which is inconsistent with any kind of electric arc or spark generator. Their video reveals a flashing blue light when the lock breaker is active. This indicates a high voltage electric spark fed directly into the spiral antenna.
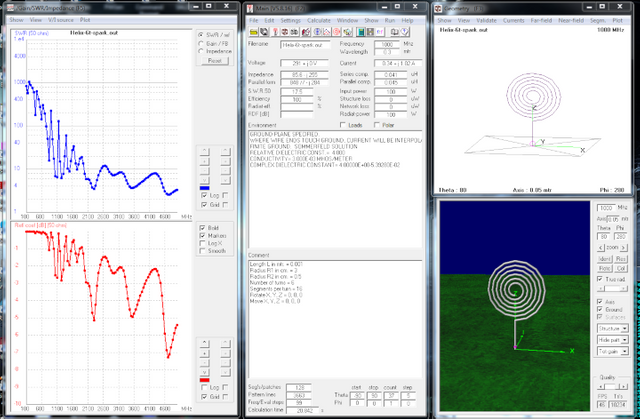
The spiral antenna was modeled on a 4NEC2 simulator. The bandwidth is way into the Gigahertz range which is too high to be very useful. Additionally, the VSWR is too low across the usable bandwidth to transmit efficiently. That means very little power is radiated from the antenna and virtually nothing in the Megahertz range. The secret is the spark generator itself; not the antenna.
RF interference compatibility engineers sometimes use a high voltage electric arc pulse generator to create broad spectrum radiated emissions. One such device used is from Jackson Research as shown in Figure 5. It is portable and has an SMA output connector. Typically, a bilog antenna is used with this device to generate broad spectrum RF interference noise. Electric arcs are not single frequency. They have a broad spectrum from Kilohertz far into the Gigahertz and optical ranges. Consequently, you do not need to know which frequencies are causing an MCU reset. This is a high energy EMP device.
The JREM1000 Arc Pulse Generator opened the same locks as the Chinese handheld device. It also opened other Smart Locks that the Chinese device failed to open. The difference is the level of power output. My experience dealing with military aircraft resistance to NEMP is predicated upon power level. The concept is if your device does not open the door, increase the power level until it does. The more power in the pulse, the more likely you are to open the door. Frying the circuit should also open the Smart Lock by default. Even the most heavily shielded military aircraft will be over powered and fail if it is close enough to the EMP source. This is the same concept behind an EMP taking down an entire power grid.
There are two versions of the JREM1000. One transmits a 3 Kilowatt pulse and the other transmits a 6 Kilowatt pulse. The pulse output is periodic in the Kilohertz range. The battery pack and bilog antenna all fit into a backpack. This apparatus works well in the laboratory, but can be inconvenient to carry around and is not well hidden. It could be fitted innocuously into a brief case facilitating much easier handling and stealth at the Smart Lock.
Fortunately, there are devices available that create a high energy electric arc pulse. The most well known is called a Taser. This device looks and operates like a gun, shown in Figure 6, and fires two darts connected to electrically conductive wires. Details about this device can be found on Wikipedia. [3] This is definitely not what to do.

However, its cousin, a stun gun as shown in Figure 7, works very well.

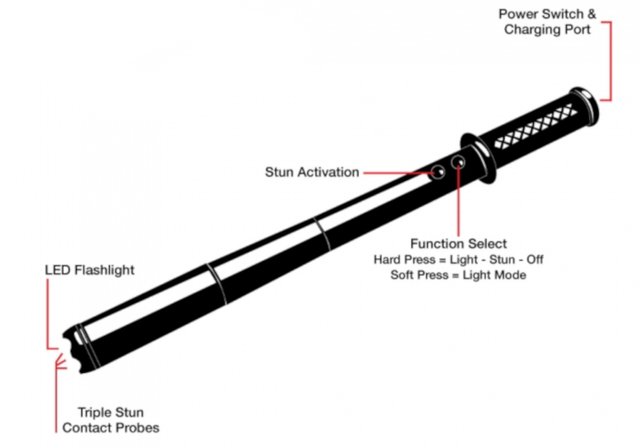
The stun bat also works very well as a spark generator, but it is more difficult to conceal.
The easiest way to open a Smart Lock is with the use of a stun gun or stun bat. These are both very effective. They are easy to conceal and light weight. They are usually rated in volts which does not give us enough information to calculate the power. But, from the size of the spark, it could be several Kilowatts. The stun bat has much larger batteries and potentially much more power than the stun gun. These devices can be easily obtained online for under US$100. And, it takes no skill to use them.
The disadvantage of the stun gun and stun bat is the hazardous electrical arc.
Ethics of Disclosure
The question of releasing methods and means of defeating locks and physical security systems has already been discussed at length by Dr. Johnston. [6] I have seen videos of criminals using advanced electronic devices on the Internet long before anyone knew how the device actually worked. In some cases, confiscation of the devices and analysis in electronic forensic labs were required before anyone knew how it worked. Censorship, in any form, of means to defeat physical security systems aids and abets the criminal element who probably already have such means leaving the general public vulnerable and unaware of the potential threat. Censorship of means to breach security does not protect the general public. It protects the various intelligence agencies and law enforcement agencies from the general public. How would you like the police to just walk up, swipe a stun gun across your Smart Lock and walk right in claiming the door was open? How would you prove that in court?
Conclusion
What happens when using a stun gun on a Smart Lock is that the passcode keypad is also useless. The entire Smart Lock is defeated when the MCU resets. It is not known how many of the existing Smart Locks are vulnerable to this form of Trivial Defeat, since there is no published data. But, the stun bat I used opened every single Smart Lock we tried. Clearly, a Smart Lock can be designed to resist an electric arc EMP attack. But, there is always a practical limit to the amount of power that the lock can resist as well as the amount of power that can be carried around and supplied to the EMP generator. Using an electric arc EMP generator to defeat a Smart Lock leaves absolutely no evidence, whether the attempt is successful or not; fried electronics is not evidence of anything. It is like saying all of the electronic failures in your house are sabotage. Electronics fail and failure due to EMP can easily be diagnosed as a power supply glitch, dirty power lines or lightning storm EMP all of which are common. Electronic circuit components all have a mean length of life and statistical failure rates. Which component caused the failure may be easily ascertained, but the cause indeterminate. That means no forensic evidence as to whether or not the lock was tampered with EMP or was just a statistical failure.
About the Author
John T. Jackson, Jr., MS received his BS Physics from Oregon State University and his MS Electronic from the University of Nevada, Reno. He is the inventor of the “Wide Air Gap Permanent Magnet Motors” (slotless motor). He has patents in the field of physical security. He is a magnetics specialist and maintains a private research and development laboratory in Hong Kong.
References
[1] https://v.vzuu.com/video/995458746503557120 circa October 17, 2018.
[2] Clayton R. Paul, “Introduction to Electromagnetic Compatibility”, John Wiley & Sons, Inc., 1992
[3] https://en.wikipedia.org/wiki/Taser
[4] https://www.helpnetsecurity.com/2019/06/24/beating-biometrics/
[5] https://phys.org/news/2005-12-biometric-expert-easy-spoof-fingerprint.html
[6] Johnston, Roger, Ph.D., CPP, “A Model for How to Disclose Physical Security Vulnerabilies”, Journal of Physical Security 3(1), 17-35 (2009).


Congratulations @jrmagnetics! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPVote for @Steemitboard as a witness to get one more award and increased upvotes!
Yeah...these smart locks are cool in theory...but there's no real regulation or anything to prevent them from continuing to sell locks they know have huge faults. Of course, they do the same thing with standard locks. Most padlocks are practically useless. They can be easily opened within a few seconds, if that. Keyed locks can likewise be opened easily by someone with YouTube and a set of picks from China. Consumers are pretty much on their own. They gotta do their research and get whatever they think is the best choice.
Of course, most locks aren't really supposed to stop a dedicated attacker, just slow them down, and discourage a few that don't know what they're doing.
It would be nice if they would work on smart locks that are more secure though, because it is a cool concept.