How (not) to Lose Your Crypto
How (not) to lose your crypto
I have been reading a lot of articles here on Steemit. Even though there is a lot of good material around on the topic of how to keep your money safe, it still seems to me that there is also a lot of confusion. Because of this, I have decided to make an attempt at writing a complete list of things that can go bad, along with high-level explanations and recommendations on how to avoid those mistakes. I stress the 'make an attempt' part since I will probably still miss certain things, and also my recommendations may or may not be flawed. As always when it comes to security I suggest you do not trust one single source. Use this post as a kind of index that gives you a picture of all the things you need to keep in mind, then do the deeper research yourself.
Index
- Phishing Mails
- Scam Websites
- Malware on Your Computer
- Exchange or Online Wallet Hacked
Phishing Mails
What is it?
What we understand under the term 'Phishing' is the process of some malicious third party trying to fool users into giving away privileged information like passwords or download malware. In the majority of cases, this is done by sending e-mails to users that look like they were sent by some person or organization the user knows and trusts. There are (at least) two different 'flavors' of Phishing, which deserve different explanations:
Normal Phishing
This is the more common (and arguably also the less dangerous) variant. The principle is quite simple: An attacker will create an email that looks like it was sent by some well known online platform like PayPal or Facebook. The message will contain some text that is seemingly legitimate and that makes it clear to the user that he must react quickly. There will also be some kind of hyperlink or button that the message will encourage the user to use. If done well, the message will look quite convincing, especially because it is possible to fake ('spoof') the sender address that is displayed in your mailing client.
The important thing to understand is that the link that this faked message provides might look legitimate, but when you click on it you will be redirected to some website you didn't want to open. The target of this misleading link might either be a website that looks like a legitimate login-page of the service that sent the message, or it could just be some random site that will try to install malware on your machine. Look at the link below for an example of this; while the link seems to be pointing to google, you'll end up on yahoo:
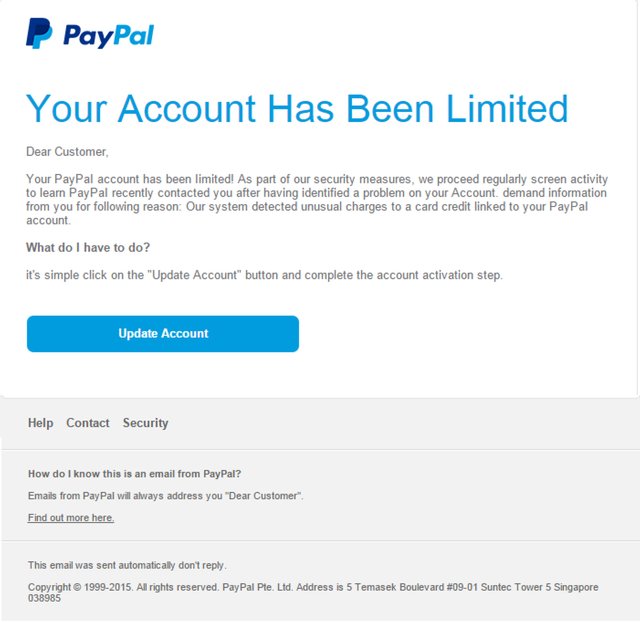
Interestingly enough I haven't received any good attempts at Phishing recently, so I had to google around for this good example of an attempt at your PayPal credentials:
Here's what jumps out at me from this message:
- No customer name. PayPal will almost certainly address you with your full name.
- Text does not make sense. If you read the message thoroughly you'll notice that there are a ton of grammar mistakes and that the overall content does not make much sense. No respectable company would allow messages to be sent out like this. You're lucky if you ever find a typo in a genuine PayPal e-mail.
Depending on the amount of work an attacker is willing to put into designing those faked messages and the websites they link to, it might already be quite difficult to decide whether a certain message is authentic or not. In the past however most normal Phishing-attempts were poorly designed and easy to spot.
Spear/Whale-Phishing
Much more dangerous than the above mentioned 'normal' version is Spear-Phishing. The principle is still the same, but the attacker no longer attacks a large number of individuals he knows nothing about. Instead, the focus is on a small number of people (maybe even just one). The attacker tries to exploit knowledge he obtained either from other attacks or simply from reading one of the victim's social-media pages.
To make these attacks even more successful attackers try to make it look like they were sent from a person the victim either knows personally or who has some authority over the victim:
[...] Spear-phishing messages, on the other hand, are more likely to appear as originating from someone within the target's own organization, generally someone in a position of authority.
National Security Agency expert and West Point instructor Aaron Ferguson calls it the 'colonel effect.'
As an illustration, Ferguson sent e-mail messages to 500 cadets, asking them to click on a link to verify their grades. The message appeared to come from a Colonel Robert Melville of West Point, and the result was that over 80 percent of the recipients clicked on the link.
What can I do to stay safe?
One of the simplest solutions would, of course, be using GPG-signed emails, but for whatever reason, this technique does not seem to find many users outside the hardcore tech-community. Therefore let's look at some less techy recommendations:
- Never click on a link in an email. NEVER! In cases where you are concerned that the content of the message may be genuine, you should visit the concerning website or service by using bookmarks in your browser. Entering web-addresses from memory is also fine of course.
- Never open email-attachments without running them through VirusTotal first. This is true even for archives like .zip/.rar and similar since those archives themselves could already install malware during the extraction process.
- When someone who seems important tries to get in contact with you by email, do not trust him/her until you are able to verify the authenticity of the sender over a second communications channel. The more important this person (and the messages he/she is sending) are to you, the more careful you must be. Ultimately only trust people you can meet face to face to ask them if they really sent you those messages.
- Adjust the settings of your email program to display messages in plain-text only. This will remove all formatting and images, and you will not be as easily tempted by emails simply because they 'look good'.
- Familiarize yourself with GnuPG (aka GPG) and start advocating the web-of-trust, even if you are not at all interested in technology otherwise. You can only profit from it.
Where can I read more?
- Wikipedia article on Phishing
- Some recent phishing statistics (very interesting!)
- The GPG web of trust
- How to sign and/or encrypt e-mails with Thunderbird on Windows
Scam Websites
What is it?
The principle is very similar to Phishing emails: Some malicious third party wants to gain access to people's accounts or private data. We can distinguish two different cases: Fake sites and scam sites.
Fake sites
Like Phishing messages are designed to look as if they were sent by some genuine company, fake websites are designed to look exactly like real websites. The goal: Make potential victims believe they're on the real website, and let them enter their username and password. A clever attacker could even fake a request for a second authentication factor like a code from Google Authenticator. Once the victim hits enter, the login data will be used by the malicious party to log into the real website and steal the victim's data/money within seconds.
Usually, those faked websites will use URLs that are very similar to the ones of the real sites (e.g. www.googl.com to get people who want to access www.google.com), such that a typo in the address-bar of the victim's browser would lead him/her there.
Scam sites
Unlike fake sites, scam sites do not attempt to imitate an existing website. Instead, they will claim to represent a new legitimate service. The most potent cases of such sites in the context of crypto currencies are probably faked ICO's (ICO = Initial Coin Offer). The malicious third party might, for example, claim to be some new group that has designed some very fancy new crypto currency that they are going to sell off at a high discount before trading is initialized. Users will be given the opportunity to create an account (thereby possibly already giving away e-mail-address/password combinations they have used on a number of other accounts), set up a wallet, and transfer real money (be that dollars or BTC/ETH/...) to buy this new currency. Of course, this new currency does not exist, but people won't know that until they have already sent their money.
What can I do to stay safe?
There are already a lot of good tools active on the internet that try to prevent users from falling victim to either fake- or scam websites. Nevertheless, you should do what you can yourself. Here are my recommendations:
- Never use the same email/password combination more than once. NEVER!
- Bookmark all your login pages. This will dramatically reduce the risk of accessing a fake website due to a typo.
- Always double- and triple-check the URL and SSL certificate icon before entering any kind of sensitive data.
- If you come across an ICO that looks promising, don't just pay money! Google around first and see what other people think about it (If no one knows it, that's a bad sign). Check if there is a company behind this offering. Check if this company really exists. Have a good long look at the SSL-certificate. Does it provide ownership-information, or is it one of those generic Let's-Encrypt certificates?
Where can I read more?
- How to prevent yourself from fake ICOs and ICO Scams
- How to spot a fake, fraudulent or scam website
- Different types of SSL certificates
Malware on Your Computer
What is it?
Malware is a piece of software that does something you don't want it to do, probably in such a way that you don't even realize it's there. Viruses, worms, trojans, adware, ransomware, all of those are malware. You might pick it up by visiting a new website, or by plugging in a USB stick that a friend of yours had plugged into his compromised computer. There really is no limit to the ways a system might get infected. Even worse, there's really no way to prevent this, because programmers would have to be able to think of an infinite number of possible attack vectors to make their software safe.
Long story short: Always assume your computer is at least a little bit infected. Even if you have ten different anti-malware-tools installed.
With this in mind, let's look at the ways malware could possibly compromise the security of our crypto currencies:
- Password lists. A clever piece of malware could sift through all your files and send everything that looks like passwords to an attacker.
- Desktop wallets. Certain vulnerabilities in desktop-wallet software might allow malware to directly steal money. And even without explicit security holes, it could still send away encrypted data to a remote server where it can easily be brute-forced (opened by trying every possible password), again resulting in you losing your money.
- Key logging. Malware could also just be recording your every keystroke. A very simple and effective way of obtaining login-information. Even the most hardcore 100 character-long password won't protect you against this.
- Clipboad sniffing. Similar to a key-logger, some piece of software could periodically look at what you currently have on your clipboard (that's the place where stuff goes when you copy it). Very nasty indeed, because even if you use a top notch password safe and long, random passwords, this one still gets you.
- Browser redirect. Remember what I wrote about fake websites? Imagine you enter www.bittrex.com in your browser, and a website that looks exactly right appears on your screen. Even the URL and SSL certificates appear correct. But in fact, some piece of malware has redirected you to a faked website. Very bad.
I could go on for hours, but I think you get the idea. Malware is bad.
What can I do to stay safe?
That's actually a tricky question. You can stay reasonably safe if you follow those points:
- Do not install any software you do not trust.
- Never visit websites you don't know are safe.
- Always keep your system updated.
- Use a good anti-virus software with integrated anti-malware modules.
But, as I mentioned above, there are always bugs and flaws, and even if you trust a piece of software, it could still contain bad code that allows malware into your system. Therefore I would recommend the following, especially if you are moving around larger sums of money often:
- Buy a second computer (doesn't need to be the newest model).
- Install your favorite Linux distribution.
- Use it exclusively to access online-wallets, exchanges and other critical websites. Do not do anything else with it. Use your normal computer for the rest.
- Vice versa, do no longer access critical websites from your normal computer.
- Keep the "secure" machine updated. Always.
- Never install anything on your secure machine except the bare minimum you need, like your desktop-wallets.
- Never plug a USB stick into your secure machine.
This should keep you pretty safe. It's still far from a 100%, but it's a reasonable mix between required skill, caused inconvenience and security. If this still isn't secure enough for you, then you might want to think about creating a live system on a SD-card. Because SD-cards have a hardware-switch that prevents write access to the card, the image of this live system can never be changed by anything. Let me know if you are interested in more details about this.
Where can I read more?
- Wikipedia on malware
- 14 Warning Signs that Your Computer is Malware-Infected
- Tails Linux distribution
Exchange or Online Wallet Being Hacked
What is it?
The same way your computer will never be completely safe from malware, servers of large coin-exchanges or online-wallets will always have some security flaws. This might be caused by incorrect configurations, software that is not up to date or simply by an insider who is corrupt. Large companies may have significantly more knowledge and resources than a single person, but since there's so much to gain from a single successful attack, the time and effort an attacker will be willing to invest is also significantly bigger.
What can I do to stay safe?
In most cases it is very simple to protect yourself from this kind of loss:
- Use exchanges only to trade. Don't leave your money there for extended periods of time.
- Move your currencies to a desktop-wallet on a safe computer, or, even better, use a hardware wallet.
Unfortunately, there are also services that almost force you to have your currency on their servers. One such example is Steemit itself. It is certainly possible to use the cli_wallet to interact with the blockchain directly from your computer, but I assume most people will find that too inconvenient.

great info there are a lot of scammers out there
Great post as always @the-tech-guy. Here's some of my thoughts on each of the sections.
Phishing: one very good way to avoid a lot of the phishing attempts we've seen in crypto is to understand that there is absolutely no reason to share your private key under any circumstance, ever. If a site asks for it, it's guaranteed to be a scam.
Scam sites: I've been recommending that people download MetaMask, even if they shouldn't be using it for secure transactions. The reason is that MetaMask has a nice blacklist of known scam sites, and it will warn you if you land on one of these URLs.
Keyloggers/clipboard sniffers: /shameless plug for my post on this subject, including an exercise in creating your own. This is one that worries me a lot. When a large-scale attack happens involving keylogging PKs, I'm betting it will be because of a compromised popular browser extension.
Browser redirection: XSS and CSRF attacks are your main concern here. I've thought about covering this, but it's always ended up being too technical and nobody gets anything from it since they move on or already understand it.
Malware: There's a balance to be struck between convenience, cost, technical ability, and security here that I think is skewed. Definitely an impossible question to give a definitive answer to, but it's my opinion that people will err on the side of cheap & easy. Those with the technical ability are not the demographic that need the most help, so I wouldn't suggest running Linux or buying a new computer. Instead, I'd focus more on the importance of using unique passwords and 2FA while taking small steps to improve your primary system's security.
Online Wallets: Steemit actually has pretty amazing security measures. They generate your randomized password for you, forcing it to be (at least initially) secure. They also have the savings option where you can store your currency and be notified if somebody tries to move it. They are forced to wait while you have time to cancel the removal and re-secure the account.
great info there are a lot of scammers out there
One can always count on @tomshwom for a great reply. Thanks so much for adding your thoughs!
Great tips! Thank you.
Great article, how can I find out more about creating a live system on SD?
Thank you! I (or @tomshwom or one of the other epic tech people here on steemit) may write an article on that in the future, but until then you could start by trying to get a standard Ubuntu image to a SD-card. That wouldn't allow for any customization, but at least it would give you a pretty safe browser environment without malware. This could be accomplished by using Etcher if you are on Windows, or dd if you use Linux. Have a look at this as a start: How to write a .iso file to an SD card?
Get back to me if it works!
You may also want to look at another @tomshwom article: https://steemit.com/cryptocurrency/@tomshwom/tomshwom-s-advanced-crypto-security-guide-part-3-creating-a-secure-wallet
good stuff
geat info
Great article, very informational. Thanks for the reminder about not storing the cryptos in online exchanges.
Thanks for reading :)
Really useful, good man!
Thanks! Very valuable article. Although we love our coins, the scene also attracts a lot of bad people. Please don't mind if I reference this article in a few blogs. :)
Thank you! Sure, go ahead. This topic needs all the exposure it can get.
Thoroughly written article. Excellent!
Thanks for sharing this. These kinds of education posts are needed and appreciated.