Cyber operation#1 (To construct a sniffer system)
□ General situation
○ You are a information security team leader of a corporation
○ Following orders of CISO, you establish plans, organize TFs and build up systems
○ The security team has 4 information security manager including you
○ The corporation only use internet. It doesn't have a independant network
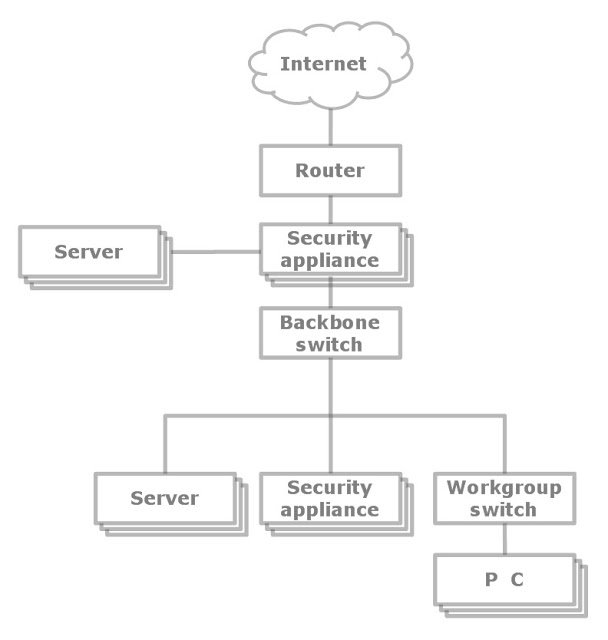
○ The corporation uses same network configuration as above image
○ The corporation network's CIDR is 16
○ The corporation has own email server
□ Special situation
○ Following orders of CISO, you establish plans, organize TFs and build up systems
○ The security team has 4 information security manager including you
○ The corporation only use internet. It doesn't have a independant network
○ The corporation uses same network configuration as above image
○ The corporation network's CIDR is 16
○ The corporation has own email server
○ Recently, I heard that some employees transmit and receive classified materials
(The classified materials should be sent by fixed procedure not email. Because the email doesn't support encryption)
○ CISO ordered to construct the system that collects and audits employees' emails
○ The result of the constructed system is not reported to parent department(=management)
○ There is no support funds to construct the system
○ The efficiency rating is in next month
□ Requirements
○ CISO ordered to construct the system that collects and audits employees' emails
○ The result of the constructed system is not reported to parent department(=management)
○ There is no support funds to construct the system
○ The efficiency rating is in next month
○ You construct the system before next month for good efficiency rating
○ You report to CISO by 1:1 face to face the result of the constructed system
○ You include the alpha test result and the system performance at result of the constructed system
○ You actually run the system after the efficiency rating
○ You report to CISO by 1:1 face to face the result of the constructed system
○ You include the alpha test result and the system performance at result of the constructed system
○ You actually run the system after the efficiency rating
※ It is also posted at : http://cysecguide.blogspot.com/2016/09/cyber-operation1-to-construct-sniffer.html
thats interesting :) > i followed u. it would be nice if you check out my art! <3 kalipo