TheShadowBrokers may have received up to 1500 Monero (~$66,000) from their June "Monthly Dump Service"

Summary
I analyzed the 'Payment ID' field of every Monero transaction in June 2017. Using this information, I was able to find 3 e-mail addresses embedded in Monero transactions which I believe may be TheShadowBrokers' customers, as well as one test transaction that may have been made by TheShadowBrokers. I conclude that TheShadowBrokers may have earned up to 1500 Monero (~$66,000) from their Monthly Data Dump. (This figure does not include money they may have earned from payments via zCash.)
The article is laid out as such:
- Background on TheShadowBrokers' monthly dump service
- Brief background on zCash and Monero
- Background on Monero payment IDs (why TheShadowBrokers may have screwed up)
- Methodology (how I scraped Monero payment IDs)
- Summary of results (including raw-ish data)
- Some discussion/analysis on results
- Other interesting tidbits
I aim to provide all of the information that you, a technically proficient reader, will need to be able to independently verify my analysis.
Background:
TheShadowBrokers Monthly Dump Service
On May 16th, @theshadowbrokers (TSB) made a steemit post titled 'OH LORDY! Comey Wanna Cry Edition' where they advertised their upcoming "TheShadowBrokers Monthly Data Dump". Using their usual obfuscated English, TSB described it as:
new monthly subscription model. Is being like wine of month club. Each month peoples can be paying membership fee, then getting members only data dump each month. What members doing with data after is up to members.
TheShadowBrokers Monthly Data Dump could be being:
- web browser, router, handset exploits and tools
- select items from newer Ops Disks, including newer exploits for Windows 10
- compromised network data from more SWIFT providers and Central banks
- compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
Two weeks later, on June 30th, TSB made a post clarifying the details of TheShadowBrokers Monthly Dump Service – June 2017 .
In that post TheShadowBrokers provided a zCash address and instructions to send 100 zCash (ZEC) (worth about $30k today), along with an e-mail address in the encrypted memo line. In return, buyers would receive an e-mail containing "a link and a password for the June 2017 dump".
The zCash community didn't seem particularly pleased by the free publicity, with their unofficial slack channel banning anybody who asked how to send payment to TSB and Zooko Wilcox, the CEO of zCash saying, "It would be nice if there were somebody who had the ability to ban bad actors from using the network" (link). 
Personally, I was surprised that TSB chose zCash over the other (arguably more prominent) privacy-oriented cryptocurrency, Monero, which has already been adopted by a number of darknet markets (those .onion sites that allow you to buy drugs on the internet). Anyways, a few days later, on June 2nd, TSB released an update, announcing that they would be accepting Monero (XMR) as well and provided payment instructions.
What are Monero and zCash?
It's been about 10 months since TheShadowBrokers announced their original NSA exploit auction which ended up being a huge flop (if money is really what TSB was after).
A common myth is that Bitcoin is "anonymous" and "untraceable". This couldn't be further from the truth. Tracing Bitcoin is becoming routine for law enforcement agencies. The US Government (and some European governments) as well as some private companies (1,2) are all developing technology to track Bitcoin transactions.
Several people have already been arrested after having their Bitcoin transactions tracked; notably, ex-Secret Service agent Shaun Bridges. Usually, people are caught when converting tainted Bitcoin into fiat through exchanges, most of which strictly enforce KYC/AML laws.
This is where the alternative cryptocurrencies (altcoins) Monero and zCash come in. I'll avoid getting into the differences between Bitcoin, Monero and zCash. For now, just know that the latter two are a lot more difficult to track than Bitcoin, making them attractive as a means for hackers to pay each other. In my opinion, the clearest [non-technical] distinction between the two cryptocurrencies is that zCash's dev team is comprised of DARPA-funded, VC-backed academics, whereas Monero's is a bunch of cypherpunks, led by a 'Chief Entertainment Officer' who posts online under the moniker fluffypony.
Monero Payment IDs
In order to understand this article, you'll need to understand how I was able to glean information about TSB's buyers.
Here are the instructions TSB gave for potential buyers using Monero:
TheShadowBrokers is making decide to be accepting Monero. For subscribe sending 500 XMR to the following address.
41jwGGMNRBKNurVnuo7ZW4HqrgPnfiJbfHUi3k46b5nFhvbpwcK6KdTSjvTRdbzdEzZbQ1t5GWhsW7scxcNv2adUJSbtExP
Monero is having "Payment ID" not "Encrypted Memo Field" but being almost same thing, small exception. Email Address you including in "Payment ID" is needing be converted to hexidecimal. If you are uber geek and converting ascii to hex in your head then fucking you. TheShadowBrokers is using webpage, ascii to hex.
[email protected] = 75 73 65 72 6e 61 6d 65 40 64 6f 6d 61 69 6e 2e 63 6f 6d
Monero requires Payment ID to be 32 bytes or 64 hex characters so pad difference with 00
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32
75 73 65 72 6e 61 6d 65 40 64 6f 6d 61 69 6e 2e 63 6f 6d 00 00 00 00 00 00 00 00 00 00 00 00 00
"757365726e616d6540646f6d61696e2e636f6d00000000000000000000000000"
[emphasis added]
TSB is very wrong here: Monero's 32 byte (64 hexadecimal) payment IDs (PIDs) are not "almost same thing" as zCash's encrypted memo field.
zCash's encrypted memo fields are encrypted, meaning nobody but the sender and the recipient can read them. Monero's 32 byte "old-style" payment IDs are not encrypted. Rather, they're included, unencrypted on the Monero blockchain which means anybody can read them. Ideally, payment IDs should be random so that a minimum amount of information can be gleaned about both the sender and the receiver of a Monero transaction.
Additionally, you can easily search the Monero blockchain for any 32 byte PID and find all Monero transactions associated with that PID. I'll give you an examples of this later.
Monero does have encrypted payment IDs -- they're 8 bytes (64 bits) which is a little too short to fit an e-mail address into. You can read more about Monero's payment IDs here.
To convince yourself that 32 byte Monero PIDs are in fact publicly searchable, I encourage you to copy and paste the payment ID from TSB's instructions above (without quotation marks), and search it on one of these XMR blockchain explorers:
1, 2
Searching that PID will lead you to a Monero transaction that used the PID from the TSB example (it was made by another researcher as a proof-of-concept). (note: the other 2 XMR blockchain explorers I checked aren't working for PID searches.)
You can easily convert the hex to ascii and get the e-mail address using the tool here. Screenshot: 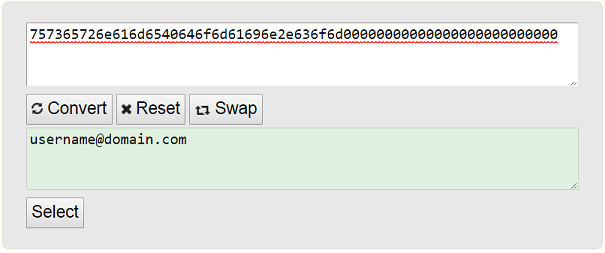
Methodology
How I [maybe] got a list of TheShadowBroker's Customers:
I had already downloaded the Monero blockchain because I use the Monero wallet and was logging Monero's 32-byte PIDs for another project.
The obvious next step was to iterate through every XMR block from June, then check each XMR transaction for PIDs, convert the binary 32-byte PIDs to hex and then to ascii and tally up the e-mail addresses that appear in the Monero blockchain. (I checked using a regex and also manually to see if I could find any other interesting PIDs.)
You can write your own script to do this or if you don't feel like downloading the blockchain, I guess you could use the web API here. (If you do go the web API route, you're going to burn a lot of their bandwidth so you should definitely donate to them.)
Results
To find out the "background level" of e-mail addresses in the Monero blockchain, I looked at how many e-mail addresses appeared in Monero payment IDs in the month of May. I found zero e-mail addresses.
The month of June was a lot more interesting. Right off the bat, I found a transaction with a PID encoding the e-mail address, [email protected]
The timestamp on that transaction is 2017-06-01 06:47:13 (UTC).
The timing of this transaction leads me to believe that it was very likely made by TheShadowBrokers (or someone known to them) as a test of Monero payment IDs to make sure that their PID e-mail scheme would work. The transaction was right between their post announcing zCash payments at 2017-05-30 06:06:15 and their post announcing Monero at 2017-06-02 09:24:03.
Additionally, I found 3 more e-mail addresses:
1 on 6/23 (@vfemail.net, the same e-mail was in 2 txs, ~1 hour apart).
1 on 6/26 (@protonmail.com)
1 on 6/27 (@protonmail.com)
I also found a nice PID about @fluffypony. (This is completely unrelated to TSB though.)
I am not posting the e-mail addresses publicly for two reasons: 1.)anybody could have inserted these e-mails into the blockchain, not just the owners of the e-mail address, and thus it'd be a violation of their privacy and 2.) I want to avoid pissing off someone who may possess weaponized malware.
(If you need the txids for some reason, shoot me an e-mail.)
However, here's two pastes with all of the PIDs for every tx from the month of June:
paste 1
paste 2
The first one goes from June 1st to June 27.
The format changes in the middle(I think before ~ 6/11 it only includes TXs with PIDs, after that it includes all 'extra' fields), converted to ascii. The format is: ascii PID,txid, block height.
The second paste contains txs from 6/27-6/30. The format is: ascii PID(UTF-8),Hex PID, txid, block height.
I redacted the e-mail addresses so they don't get picked up by search engines or something, but you can find them with (ctrl+f '.com'/'.net') then using the txid to find the PID and then converting hex to ascii.
You may notice a few interesting trends/patterns in PIDs (unrelated to TSB).
I apologize for the jenkiness of the datasets; I just decided to include them last night so that you could have a look for yourself and they're a bit thrown together. If someone makes a better one I'd love to link it. I'm also pretty sure I accidentally omitted a few txs but none which contain e-mail addresses.
Discussion
In my previous steemit posts, I avoided adding my own analysis/opinions to posts, preferring to allow readers to come to their own conclusions. It turns out when I do this it leads to self-proclaimed "experts" plagiarizing my post, overstating the significance of the findings to fit their narrative, and big media outlets publishing it as fact despite real experts saying their conclusion is bullshit. /rant
So here's my analysis:
How much did TheShadowBrokers earn from their Monthly Dump Service?
It is impossible to prove that TheShadowBrokers earned a single cent. Anybody in the world could have made those transactions and they could have gone to anybody, not just TSB. Therefore, they could be completely unrelated to TSB and the Monthly Dump Service. If someone had nothing better to do, they could spam hundreds of different e-mail addresses on the Monero blockchain and nobody would be the wiser. (They would have to pay a small transaction fee each time though.)
That being said, at least 1 of the e-mail addresses actually referenced TheShadowBrokers (the e-mail address included one of their more memorable quotes), so it did have something to do with TheShadowBrokers. Also, because encoding e-mail addresses on the XMR blockchain is rare, it seems reasonable to infer that these e-mail addresses are linked to the TSB monthly dump.
Because of Monero's RingCT, it is impossible to tell the value of Monero transactions, so we can't know if someone sent the full 500 XMR, or if they just sent 0.005 XMR to troll TSB or some other weird shit.
What this analysis does provide is an upper limit for how many people paid TheShadowBrokers using Monero. There were 3 e-mail addresses in the XMR blockchain. If each of those e-mail addresses represented a buyer who sent TSB 500 XMR, that's ~$66k at today's monero price. That's quite a bit of money for 1 month's work, but still considerably less than some of the exploits TSB previously released were worth.
One major caveat is that we have no idea how much zCash TheShadowBrokers may have received. (They claim to have received a payment from "[email protected]", which I did not find in the Monero blockchain. If TSB is telling the truth, this means they received at least 1 zCash payment.)
Of course, the most important implication of this article is that it's possible/probable that several criminal hackers and/or exploit brokers are now in possession of the NSA's weaponized malware. (Now imagine what would've happened if WannaCry came out before Microsoft released the MS17-010 patch.)
Did TheShadowBrokers know Monero PIDs are publicly viewable?
Choosing to use PIDs the way TSB did had big implications (as evidenced by this post). Someone creative should've been able to come up with another way to share e-mail addresses without making them publicly viewable.
There are two possibilities here (in no particular order):
Option A: TheShadowBrokers done fucked up.
This is plausible. Confusion with payment IDs is very common. If this is the case, it indicates that TheShadowBrokers aren't particularly familiar with Monero and may have made other mistakes. I am reaching out to some actual Monero experts and will ask them if there is any possibility that TSB may have helped feds further constrain the list of possible TSB suspects with the transaction from June 1st. (Tracking Bitcoin is tricky. Tracking Monero is waaay more complicated, and you should be skeptical of anybody who claims they have done it unless they're an XMR contributor or some world-renowned cryptographer or something.)
Option 1: TheShadowBrokers did this deliberately because TSB wants to fuck with the NSA. The combination of zCash and Monero is very interesting -- the Monero PIDs would allow NSA to know that TSB had some customers, but the possibility of zCash payments prevents the NSA from knowing just how many buyers TSB had.
Did anybody else do this analysis?
In their July Monthly Dump Service post (2017-06-28 06:47:33), TSB says:
Some peoples is sending small payment with hidden service url. TheShadowBrokers is not visiting url so no idea what it is. Could be good. Could be bad. Could be nothing. TheShadowBrokers is having too many enemies with to many resources to be finding out. But be enjoying at own risk. Smelling hidden service FBI hackish.
nfs6e454oyvajfro.onion/gwfGzkpR32UwCVXq46rgMpc2BVxl.html
That URL is too long to fit in an XMR transaction and thus must have come from a zCash tx.
Of course, TSB isn't dumb enough to click an unsolicited .onion url without posting it publicly first. You can view the link via onion.to here if you don't feel like booting up tor.
The link appears to be a note from Darknet Hacking Services (DHS) which is a darknet service that will hack stuff for you.
One interesting quote from the post is:
It doesn't appear you made much money from the first release and I can offer you significant financial gains should you choose to work with us.
To me, this implies that others may have carried out the same analysis that I did (which makes a lot of sense if you're a potential buyer, you want to know how many other people are going to get the same exploits).
Edit: apparently DHS just updated the link above right before I posted this. It now reads: "Why oust the people who attempt to purchase/work together. Things that make you go hmm." The original text is pasted here.
This post could be what it claims to be, some hackers for hire trying to cut a deal with TSB. Or it could be a federal honey pot.
Or combined with TSB's response, it could be TSB just fucking with the feds some more, basically telling them, "We're about to sell your exploits to the darknet hacking equivalent of 1-800-PLUMBER ."
It also seems possible that TSB is helping Darknet Hacking Services (DHS) advertise. After all, if DHS didn't want the whole world to be able to read their message, they should've encoded it with TSB's PGP key. (Also worth noting, the PGP key was initially registered as The Shadow Broker singular, no 's'.)

If you have any questions or comments, or caught any mistakes, please don't hesitate to post a comment, PM me or e-mail me. If you didn't get something, odds are a lot of other readers didn't understand it either so please ask me to clarify it!
If you want to collaborate on a project or hire me part-time (not really in it for the money but I wouldn't mind adding an infosec/analyst/journalism bullet point to my resume), shoot me an e-mail:
If you want to frame your friends by including their e-mail address in XMR txs, here's a good address to send the TXs to: 49GdoooVtwEGZjrVCpG9tsLZEVtChHaAEKWRKVNoFLZQNGLmAgjyhJ3AMj6BtLdT9PF14Pfc5x3Gc6SSpCxcDLUEMNXN1SD
;)
Also, I'd like to thank the Monero community on /r/Monero and Monero's slack channel. They're all awesome, very friendly and provided me with accurate, non-condescending answers when I asked stupid noob questions.
Updates
The pastes were down for a while because my github account got flagged by their spam filter. I contacted github and they fixed it.
I am told that a memo field is on the Monero "list" and will be implemented in the future. (Check out their roadmap too!)
Awesome Work.
Monero, Dash, Zcash, Neos, etc are still using the 'encrypted' money transfer services. Ethereum is to release Raiden in a couple of months, which allow for anonymous transactions, similar to Zcash, Dash, etc.
I wonder if this will effect their value?
I am uncertain whether or not Ethereum + Raiden tech will work truly similar to the Tor-brand dark currencies or Not.
I happy to have the Tor brands around, but they did create a lot of copycats, etc, which could lead to some pump and dump type behavior. TX is a coin I've been watching, waiting for it's pump, and MASS is another Tor Brand ICO type of service launching shortly.
Essentially MASS does the master node hosting for you on an assortment of these type of encrypted block chains for a fee.
Anyone here Master Node? I'm just getting mine setup :)
Personally, I've encountered difficulties in making anonymous transactions with ethereum. I was only able to find 1 (shady looking/centralized) mixer and a smart contract that almost nobody uses.
Led me to make a few payments in Monero/bitcoin (which has plenty of reputable mixers available) instead of ether which would've been my preference. So yea, IMO any increases in ethereum's fungibility will totally lead to immediate increases in value.
If anybody links me a good ethereum mixer, I'd be stoked.
I'm going to check out TX, sounds interesting.
Who is the idiot who would suscribe to the ShadowBrokers dump using a unencrypted payment ID??? This is designed to catch idiots. Not Monero's issue.
Monero just hit $120 :)
https://steemit.com/bitcoin/@jimbojones/exclusive-monero-just-hit-usd120