computer networking and inter-connectivity Tutorial 2- Network Types, Technologies And Network Security
Greetings wonderful stemians. Before we proceed with today’s tutorial, I would like to make a quick recap of our previous article on computer networking and inter-connectivity Tutorial 1.
This article was brought to you in conjuncton with Mechanic Assistant
We discussed that data communication is the transmission of data signals between two or more interconnected devices. Furthermore, we discussed on different network topologies that exist in the world today and they are; The Mesh, Bus, Star, Tree, Ring and hybrid topology.
Today we will be looking into The types of networks, common technologies used in networks and a brief of Networking Security.
This article was brought to you in conjunction with our partner href="https://celebexaminer.com/">celeb examiner
TYPES OF NETWORK
The first I would like us to discuss is the personal area network that is common to each and every one of us. Although others mentioned below are very popular.
PERSONAL AREA NETWORK
Abbreviationally known as PAN, this network spans between our devices within a short range. İt is known to be the smallest type of network that is very personal to any end user.
In some devices, you will notice that there are some features like Bluetooth and infra-red. These are examples of a personal area network and the range of connectivity is within 10 meters. Sometimes, we use Bluetooth on our mobile devices to share files with another device. Remote controls, keyboard, mouse-enabled devices, headphones, and wireless printers. All these devices make use of either Bluetooth or infra-red technology.
A Brief History Of Bluetooth: the name Bluetooth came from Jim Kardach who was known to be reading a novel about king Hareld Blatend and the Vikings that occurred a thousand years back. The name came from the nickname of the king.
Although its name was gotten from the king, Bluetooth technology started making its move from the year 1942 when it got it patent right.
Bluetooth technology got its full remarks in the year 1994. And this came when Ericson telecommunication company came up with the idea of replacing RS-232 cables that were used to communicate between RF-based devices.
After the idea came up, other companies like Nokia and Intel also acknowledged the same idea of linking computers and cell phones the same year with this technology. Due to the idea, they discovered an opportunity to make different devices produced by different manufacturers communicate with each other.
They decided to form a group since they all have one goal. The name of the group formed is called Special Interest Group (SIG). This group is formed by Ericson, Intel, Toshiba, Nokia and IBM.
After the group was formed, in 1998, they version 1 was launched and since then they have been progressing from year to year as technology advances, this also saw the formation of gaming companies such as Rockstar game the producers of GTA and Ubisoft, producers of Assasins creed .
LOCAL AREA NETWORK
This type of network spans inside buildings and is administratively controlled by administrators. The building includes offices and homes.
Ethernet has been in existence since the 70s, and its implementation can be done with either twisted cable or wirelessly (Wi-Fi) that is under the IEEE 802.11 standard.
İmplementing LANs in an environment is not expensive as it contains computers used as servers that serve clients with information needed at a particular point in time. More so, they function with IP addresses and routing with each other is less depending on how large the network spans.
LAN has given opportunities for workers to communicate and work together from their offices and this makes it easy for companies to share information efficiently.
Classification of LAN
“For every existing technology, there is an already existing component that defines and make it to exist”
The Local area network is not exempted when it comes to dealing with technologies. The advances in technology make it possible for an in-depth exploration of LAN. These technologies, though existing through the years still upgrade to suit the modern technologies that are used every day.
The Ethernet (Mr Popular)
Widely used to deploy local area network, this technology was invented by D.R Boggs and Bob Metcalfe in the year 1970. Its standardization was done in 1980 under IEEE 802.3.
In life, we cant live without the people around us. our growth is dependent on the people around of us whether good or bad, friends or enemies, they all help to build us and our personality.
Ethernet has played a vital role in the family of networking devices. Although there are some flaws when it comes to Ethernet, however, these flaws are covered. Thanks to other helping networking tech that supports other technology that has flaws.
One flaw that is common is data collision while sharing media and in other to cure the madness of collision, we now got a collision detector also known as carrier sense multi-access (CSMA/CD).
The question is, what happens when a collision is detected? Here is the answer. When a collision is detected, the host that is responsible for sending the transmission roll back and wait for some amount of time and then resends the data for transmission. Simple as that but the brain on the system doesn’t come easy.
The traditional Ethernet makes use of 10BASE-T features. However, the 10 identified, specifies that the speed of transmission is 10 megabit per second and the base means baseband and T depicts thick Ethernet. 10BASE-T uses cat-5 twisted cable or coaxial cable for cabling.
The Fast Ethernet
In order to make advancement to the undeniable evolving of technology around the world, Ethernet decided to keep its pace by coming up with Fast-Ethernet that can run on fibre optics, UTP and wirelessly. Its speed rate is 100 megabit per second and standardized as IEEE 803.2 100BASE-T while using the cat-5 twisted cable.
Basically, when it uses fibre, we can define it as 100BASE-FX standard and over a long distance, Ethernet fibre can cover a range of about 100 meters but that’s when it is on half duplex. What if it's on full duplex? then it can cover over 2000 meters.
Giga-Ethernet
Introduced in 1995, the giga-ethernet provides the great speed of about 1000 megabit per seconds and it is standardized with IEEE802.3ab which uses an unshielded twisted pair cable. However standardized IEEE802.3ah is specific to a Giga-Ethernet that makes use of fibre optics.
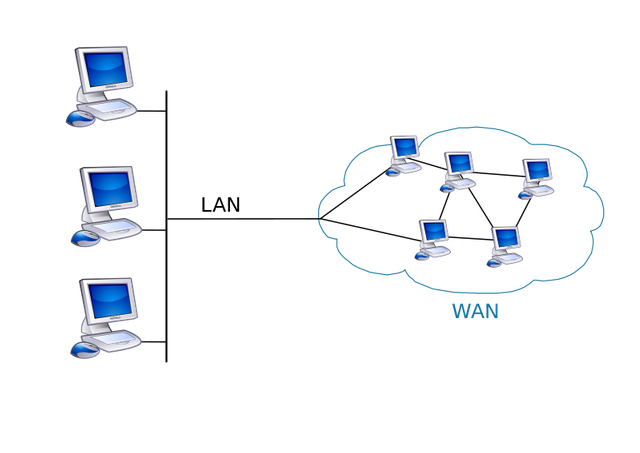
WIDE AREA NETWORK
Also known to be abbreviated as WAN, this type of technology covers a wide range of areas. İt spans across countries, continents etc. In our dispensation, we can observe that this type of network is what we use to communicate. This network specifically provides needed sustainable access to LAN and MAN.
WAN uses technologies that make it stand out from other networks and they are managed by different administrators.
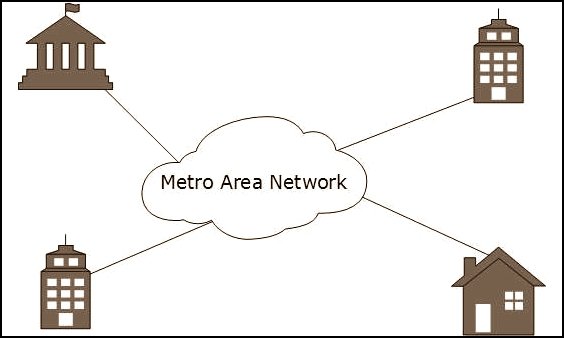
METROPOLITAN NETWORK
Known as MAN and spans a city. This includes the distribution of ethernet cables, microwave transmission technology, ATM or fibre distributed data interface (FDDI).
When implementing MAN, there is a high need for a quality communication channel in order to transmit quality information without interruption. The Backbone of MAN is usually connected with fibre optic cables.
VIRTUAL PRIVATE NETWORK
Known as VPN, but not very popular to the environment, makes use of the internet to give privileges, access to any individual that want to get resources, encrypt transmission in order to get hold of eavesdroppers etc. With VPN, one can access a device from any location with any device. for example, one can connect to his or her computer remotely with a mobile device. I use it often when connecting to my devices at work I must say that it's awesome!
Security On Network
I discovered that during the days when the internet was invented, there was a high restriction to İndividuals and companies except for the universities and military but as the world gets older, it spread across different areas of discipline. However, the use of devices to internetwork needs a high concentration of security because most security breaches that we encounter are based on the concept of network.
Every company in our era makes use of networking technology and sometimes the topology used affects the security of the network. Let's take a look at a big organization that has a different workstation, cameras, IP telephones, servers and so on. All these devices are connected one way or the other to the internet and when it comes to the operability of devices, you will notice that each has its own operating system,a connection type, software and how they handle them.
Connecting these devices to function without interruption is mainly done by the network engineers. They make sure that this device communicates effectively and efficiently without collision or interference. On the other hand, while making sure that this technology can communicate with each other, they also try as much to see that the network is secure so as to avoid intrusion from a third party.
Known Physical Network
There is basically two modes of operation when it comes to inter-connecting devices like I stated earlier. The wired or wireless mode of connection. The combination of these modes of connection is used by organizations in order to operate in an effective networking environment.
These cables connected to devices are connected to switches/routers in order to gain an external network access.
What Are the Attacks And vulnerabilities that networks are exposed to?
The major threat that exists between these two modes is the unauthorized access by an individual into the network. When a user connects a device to an unsecured switch/ hub, there is every tendency to be hacked if an unauthorized user connects a device to a port that belongs to that switch. Mind you, not only that single user is vulnerable to this attack but the company in general. These are the things that might occur when an unauthorized user gets his hands on a network device.
- packet sniffing in order to steal vital information. What is packet sniffing?
Packet sniffing is capturing transmitting packets of data from a network. The device or software us to carry out this act is called a packet sniffer.. when a sniffer sniffs a network, it does not modify the packets but rather watch and display logs in the network. Packet sniffing is hard to detect and most items it is known to sniff are SMTP, POP, Telnet authentification, allowing intruder to read emails, reading passwords and SQL database and more.
- spoofing is an attack done when an individual or a software impersonates a device on the network so as to attack the host network. They attack the network not just for a minor reason but to steal data that might be of great importance to any organization. Or sometimes they deliver a Man-In-The-Middle attack. The common method used is Address Resolution Protocol (ARP) spoofing, Internet protocol address (IP Address) and Doman Name System server (DNS) spoofing.
- Denial of service by flooding the network with packets thereby making it difficult for users to access the network.
Conclusion
A computer network is a broad discipline that deals with creativity and security. İf anyone wants to venture into this discipline, then the individual must be aware of security measures to be taken especially when handling a large network. A network engineer gets hold of the physical implementation of designing a network and inputs his skills by making it connect to each other with his mindset based on the security of the network.. The blockchain is based on network and one will discover the security measures used in order to secure the technology while connecting to different nodes.
Thank You For Your Time
References For Further Reading
Wireless Update
History of Bluetooth
Local Area Networks
Overview of Networks Types
Packet Sniffing
Security
This article was brought to you in conjuncton with Mechanic Assistant

I'm so happy seeing guys venture into my domain. I love your work and I would love to ask a question. How do one mitigate IP spoofing attacks based on address resolution protocol impersonation?
First, there are different techniques used to identify spoofing via arp. Softwares can be implemented but I will just give a quick info not going too deep. You know that arp works mainly on LAN to request and recognize the mac address and ip address of different host in the same network when sent with respect to the ip address. When an arp request is being sent, the distinct host replies with both the ip address and the MAC address in unicast(one to one) depends though. And all these contains packets that is packaged in a frame that is transmitted in the network. Thus, one solution is implementing Reverse path forwarding. In the place where I work, we make use of Fortigate firewall which perform this aspect of RPF. Fortigate is owned by Fortinet which tries as much to enhance network security on different enterprise. We make use of forti analyzer, forticlient in compliance with fortigate(on an end user computer). Our firewall blocks ip packets from reaching a destination if it does not belong to the routing domain and if its subnet is corresponding our network. Also, since arp is mainly used by switches, security measures can be taken in the area of the switch but that depends on the process you want to use. One is port security on the switch.
A very nice response but I have a little correction to make, address resolution protocol is used by a host within a LAN to identify the MAC address. Hence, it already knows the IP address, so only the MAC address is returned after a successful ARP. Also you answered my question from a layer 7 perspective but I was expecting you to answer the question from a layer 3 to layer 1 perspective, though your answer is purely valid and helpful. Thanks buddy.
Thanks buddy..in my response I quoted "in respect to the ip address". and to correct you too, In the format of arp, when replying, the ip address and the MAC is sent back to the host together. if you need the layer 1 to 3, then you can consider..port security, dynamic arp inspection and T-Arp as well. in additiion, fortigate does not only work in layer 7, because its configuration is done exactly like when configuring a router or a switch as it has its own CLI. you can check it out if your are interested
The address resolution protocol is a broadcast that says "hey buddies, I have this layer 3 address, does anyone of you bear the same address?" If any host has such ip address, it responds with "hey man, I heard someone is looking for my physical address, take, this is it". Of course every frame has source and destination field but that's not part of the response of an arp like you stated. Also I said the information you provided was would be useful to me. Thanks anyways
We are here to learn and nothing stop us from becoming highly knowledgeable in any particular niche. Had learnt so many things that would not have been possible without steemit.
This your question shows your versed, and I do hope the author @wisdomdavid provides a good answer to this question.
Oh😱! I see he has "wisdom" to his name. He must be a genius😂
This article worth consulting by those researching on similar topic.
Regards
@eurogee of @euronation and @steemstem communities
thanks so much for stopping by @eurogee. I do appreciate your presence😄
Good work though I am not really a computer person. I feel you could have done better with the structure and arrangement of the article in general. You are a steemstem veteran as far as I am concerned. Some of the sentences look disjointed and could have fared better being in separate paragraphs.
Thanks you so much for spotting that. Taken into consideration sir. Amendments will certainly be done.
Hi @wisdomdavid!
Your post was upvoted by utopian.io in cooperation with steemstem - supporting knowledge, innovation and technological advancement on the Steem Blockchain.
Contribute to Open Source with utopian.io
Learn how to contribute on our website and join the new open source economy.
Want to chat? Join the Utopian Community on Discord https://discord.gg/h52nFrV