HACKING!!!
When technology advances it always comes with cons. Hacking is shockingly repellent; inspiring horror. Pseudo or real rumors or news we are getting from all over the world about hacking. What is hacking? Hacking is the phenomenon in which hackers can know about your very personal information and your data by means of unlawful means and unauthorized practices. Cyber hacking is something stealing and invading space just like recent incidents of facebook, twitter and many social media forms were a hot news all around feels ecentric.
COMMON TYPES OF HACKING TECHNIQUES:
- PHISHING:
In this technique the hacker copies and replicates the most approaching sites by housing the user and sending him a parody link. It is most deadliest site of insertion where engineers are involved.
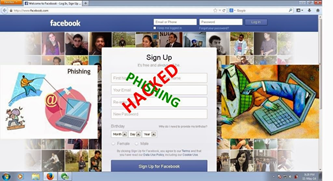
When the user logs in and enters the data to its site the hacker by using Trojan software gets the personal information by this pseudo site of the person who is tricked and swindled.
- BAIT AND SWITCH:
This hacking technique runs on paid advertisements spacing of the specific websites which are ruled by the hackers to get directed on the septic page malware. This attracts the users to click on the ads run on websites and later the data is invaded by the hacker. This would make user to believe its authenticity and maliciously the hacker has your all information by hacking your systems.
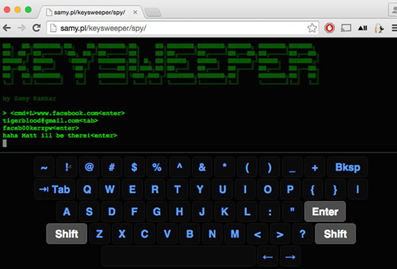
- KEYLOGGER:
This hacking technique has a link with your software keyboard system which the user uses keypad to logging in for certain sites and files of its accounts. It has your certain confidential area where your IDs and passwords can be detected by using sensors and radiations of electromagnetic. This is why banking information has high alert systems so no one invades it. We ought to be very cautious!!
- COOKIE THEFT:
This provocative method is used by hackers by getting into your browsing history, your passwords and IDs of your username by accessing it and authenticate as a browser on your system by gaining all your personal data by having IP packets through the machine of the hacker.

- FAKE WAP:
WAP (Wireless Access Point) this connects it to as public formal place. Hackers have all the joy in using this pseudo WAP and it access to your personal data and belongings online. This is believed to be the easiest way possible for the hackers to invade your data publically using WAP. Net cafes and common usage of internet users needs to be really cautious.
~By Haya Sultan
You have a minor misspelling in the following sentence:
It should be publicly instead of publically.Hey @awaismemon, great post! I enjoyed your content. Keep up the good work! It's always nice to see good content here on Steemit! Cheers :)
Congratulations @awaismemon! You received a personal award!
Click here to view your Board
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness and get one more award and increased upvotes!
Congratulations @awaismemon! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!