Facebook hack update: Nearly 30 million users' data stolen. How to find out if you're one of them
30 million Facebook users had their accounts hacked
See what was stolen from every one of those Facebook accounts.

SAN FRANCISCO – Facebook says 20 million less records were ruptured than initially thought in one of the most noticeably bad security episodes at the monster interpersonal organization – 30 million rather than 50 million – yet aggressors snatched touchy individual data from about portion of those clients that could put them at genuine hazard, including telephone number and email address, ongoing ventures on Facebook, area history and the kinds of gadgets individuals used to get to the administration.
Programmers got their hands on information from 29 million records as a component of a month ago's assault, Facebook unveiled Friday. Facebook initially assessed that 50 million records could have been influenced however the organization didn't know whether they had been endangered.
For about portion of those whose records broken into – somewhere in the range of 14 million individuals – the programmers plundered broad individual data, for example, the last 10 puts that Facebook client registered with, their ebb and flow city and their 15 latest pursuits. For the other 15 million, programmers got to name and contact points of interest, as per Facebook. Aggressors didn't take any data from around 1 million individuals whose records were influenced. Facebook says programmers did not access money related data, for example, charge card numbers.
The organization would not say what the thought process of the aggressors was yet said it had no motivation to trust the assault was identified with the November midterm decisions.
Facebook clients can check if their information was stolen by visiting the organization's Help Center. Facebook says it will exhort influenced clients on how they can shield themselves from suspicious messages and different endeavors to misuse the stolen information. Fellow Rosen, Facebook's VP of item administration, said the organization hasn't seen any proof of aggressors abusing the stolen information or that it had been posted on the dim web.
Influenced clients ought to be watchful for undesirable telephone calls, instant messages or messages from individuals they don't know and endeavors to utilize their email deliver and telephone number to target spam or endeavors to phish for other data. Facebook clients ought to likewise be careful about messages or messages professing to be from Facebook, the organization said.
Outsider applications and Facebook applications, for example, Instagram and WhatsApp were not traded off, as indicated by Facebook. Programmers were not ready to get to any private messages but rather messages got or traded by Facebook page chairmen may have been uncovered.
Security specialists say the 14 million clients who had broad individual data swiped are currently to a great degree helpless. Colin Bastable, CEO of Lucy Security, which centers around cybersecurity avoidance and mindfulness, painted a particularly inauspicious situation.
"Actually, because of this news, a great many phishing assaults will now be propelled, putting on a show to be from Facebook. Up to 20 percent of beneficiaries will click and an expansive number of those will be effectively assaulted, a considerable lot of them utilizing work PCs and cell phones," Bastable said. "Organizations and governments will lose cash, ransomware assaults will result from this hole, and the assault will resonate over numerous months."
The guilty parties behind the enormous hack have not been openly distinguished. The FBI is effectively examining the hack and requested that Facebook not unveil any data about potential culprits, Rosen said. When they revealed the rupture two weeks back, Facebook authorities said they didn't know who was behind the assaults.
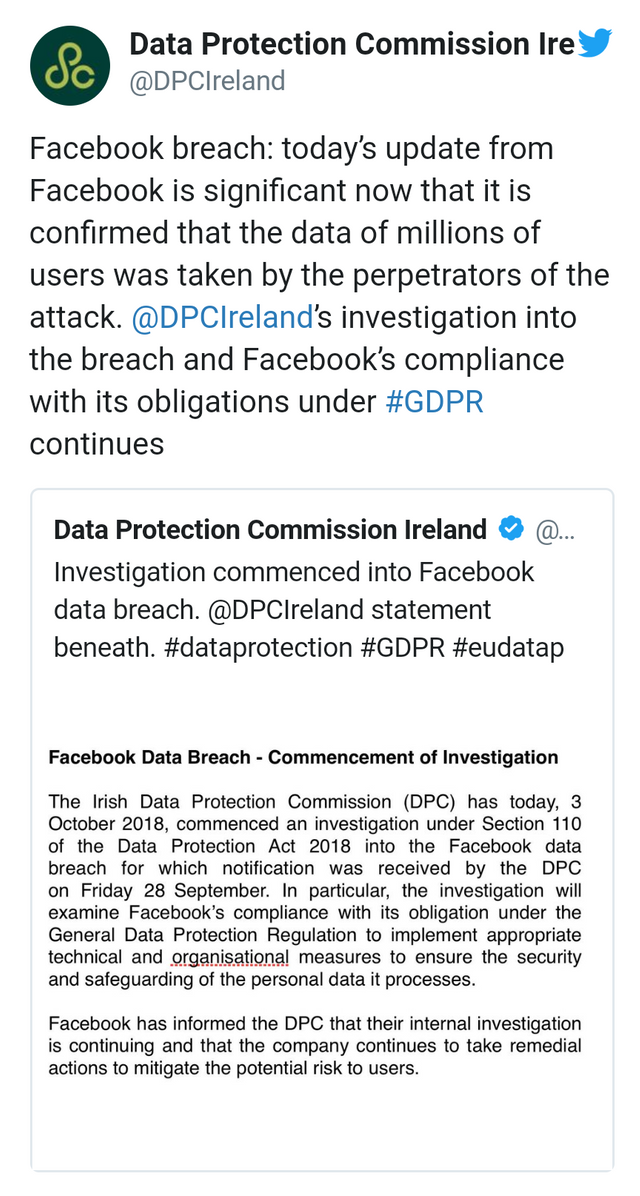
The most recent divulgence, another in a progression of security slips by that have shaken open trust in Facebook, may escalate political warmth on the organization. An examination is in progress by Ireland's Data Protection Commission, and Rosen said Facebook is likewise coordinating with the Federal Trade Commission and different specialists. The FTC declined to remark if it's exploring.
"The present refresh from Facebook is huge now that it is affirmed that the individual information of a large number of clients was taken by the culprits of the assault," Ireland's Data Protection Commission, the guard dog office accused of security assurance in the European Union, said in a tweet.
The degree of the individual data endangered by assailants conveyed a hit to the advertising effort Facebook has been pursuing to persuade the in excess of 2 billion individuals who consistently utilize the administration that it's not kidding about securing their own data after the records of 87 million clients were gotten to by political focusing on firm Cambridge Analytica without their assent and Russian agents spread purposeful publicity amid and after the 2016 presidential decision.
This week, Google recognized that a large portion of a million records on its Google + interpersonal organization could have been imperiled by a product bug. The affirmation incited officials to require a FTC examination. The two occurrences could additionally fuel a congressional push for a national security law to ensure U.S. clients of tech organization administrations.
"These organizations have a stunning measure of data about Americans. Ruptures don't simply damage our protection, they make huge dangers for our economy and national security," Federal Trade Commission Commissioner Rohit Chopra revealed to USA TODAY after Facebook unveiled the information break a month ago. "The expense of inaction is developing, and we require answers."
After the records were imperiled a month ago, in excess of 90 million clients were compelled to log out of their records as a safety effort.
Facebook says assailants abused a component in its code that enabled them to hold clients' records. Those records included Facebook CEO Mark Zuckerberg and his second-in-direction, Sheryl Sandberg.
The assault started Sept. 14. A spike in rush hour gridlock set off an inward examination. Over seven days after the fact, on Sept. 25, Facebook distinguished the helplessness and settled it two days after the fact.
The weakness was presented in July 2017 when a component was added that enables clients to transfer cheerful birthday recordings.
Assailants abused a weakness in Facebook's code that influenced "View As," an element that gives individuals a chance to perceive what their very own profile looks like to another person. The component was worked to give clients more command over their security. Three programming bugs in Facebook's code associated with this element enabled assailants to take Facebook get to tokens they could then use to assume control over individuals' records.
These entrance tokens resemble advanced keys that keep individuals signed in to Facebook so they don't have to return their secret key each time they utilize Facebook.
Here's the means by which it worked: Once the aggressors approached a token for one record, call it Jane's, they could then utilize "View As" to perceive what another record, say Tom's, could see about Jane's record. The helplessness empowered the assailants to get an entrance token for Tom's record too, and the assault spread from that point. Facebook said it has killed the "View As" include as a security insurance.
A month ago, Facebook reset the tokens of about 50 million records that it accepted were influenced and, as a safety measure, additionally reset the tokens for another 40 million records that had utilized "View As" in the previous year. Resetting the tokens logged the influenced Facebook clients out of the administration.
A rupture of this kind is anything but a solitary, confined occasion, cautioned Adrien Gendre, CEO of Vade Secure North America, an email security organization. Programmers don't benefit from breaking into Facebook accounts. Cash's made, he noted, by propelling lance phishing assaults utilizing the information they've purloined, an undeniably regular type of cyberattack where programmers parody somebody's character to inspire them to finish a compose exchange or offer private data.
What's more, that is terrible news for the 14 million Facebook clients who had insinuate individual data stolen.
"What's basic here is the level of individual information that was uncovered," Gendre said.
You got voted by @curationkiwi thanks to johnmichel! This bot is managed by Kiwibot and run by Rishi556, you can check both of them out there. To receive maximum rewards, you must be a member of KiwiBot. To receive free upvotes for yourself (even if you are not a member) you can join the KiwiBot Discord linked here and use the command !upvote (post name) in #curationkiwi.
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by johnmichel from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.