Mac Users Update Your root Password NOW!
There have been a lot of people on the internet screaming about the latest "hack" against the new Mac OS High Serria. If you've recently updated to the latest version of Mac OS X, it's time to change the root password on your Mac. The latest version of Mac OS High Serria has a vulnerability in it where the root password is blank which allows anyone with physical access to the MacBook to gain full administrative access to the system by logging in as the root user.
UPDATE: Apple has just released a patch for this vulnerability and you can find it here
TL;DR Skip to "So How do I Fix This?"
How bad is this really?
Well, it's pretty bad. The root account is the most important account on any mac so the fact that the password is blank is kind of a big deal. However, I think there is a lot more panic over this than there should be. This is not a "hack" in the traditional term. There is no malicious exploit code that has to be run to take over the system and from what I can tell as long as you have not turned on the mac SSH server there is no way to use this to get into a mac without having physical access to the system. It's also important to note that the SSH server is turned off by default on all macs so unless you have turned it on there is very little chance that someone will use this vulnerability against you remotely.
I also don't want to discount the severity of this vulnerability, it is serious and Apple should issue a patch or guidance as soon as possible. I'm just not as concerned about it as most people. I work in the Cyber Security field as a white hat hacker so I know the severity of this vulnerability. However, there is a perfectly good workaround and it's easy to implement.
What is root?
Image Courtesy of Giphy
Ok, so the GIF above is my attempt at an awful joke. Please don't hate me for my bad sense of humor.
For those that are not familiar with the interworkings of Mac or Linux/Unix, the root user account is considered the super admin. This account comes by default on all Mac, Linux, Unix or BSD operating systems and is the one that has all privileges to do anything it want's to the computer. So this is a user account that you want to protect because if someone with malicious intent were able to gain access to this account they could do whatever they wanted to your computer, including installing malware or stealing passwords and files.
So how do I fix this?
So far as of this posting, I cannot see that Apple has issued a patch. My guess is that a patch will come down in a few days, Apple is usually pretty good about security updates so make sure you are watching for any updates and install them as soon as possible. The other way to temporarily fix this issue is to set a new password for the root account. This works because the vulnerability we are talking about is the root account has no password set (i.e. the password is blank). So here's how you do it:
Before doing this make sure you set the new root password to something you know and is secure. If you lose this password it could cause issues for you in the future.
- While logged in to your normal user account open the Terminal app by clicking on the spotlight search and typing
terminal - Type
sudo passwd root
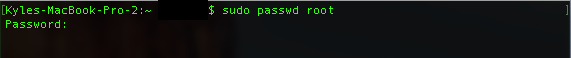
- The terminal will ask you for your current password, this is the password that you use to log in to your normal account. Type it in and hit enter (note, you will not see the characters or any dots when you are typing your password. This is the way that the terminal app masks your password from those that may be shoulder surfing).
- The terminal will ask you for a new root password. Type it and hit enter.
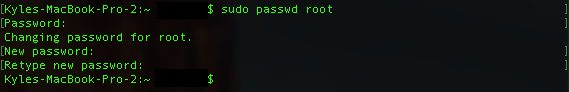
- The terminal will ask you to confirm your new root password. Type it and hit enter.
That's it, you should be set to go. Again make sure that the password you set for the root account is secure and set to something you know.
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by kslo from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews/crimsonclad, and netuoso. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP. Be sure to leave at least 50SP undelegated on your account.