Class Third: " AWS RDS In A VPC "
AWS RDS Service
AWS RDS in a VPC
Hello and welcome to the next module – AWS RDS in a VPC.
In the previous module, we created a MySQL DB instance in AWS RDS using default network. Now let us learn about a VPC and see how we can create a VPC in AWS RDS and connect to a DB instance via EC2 instance.
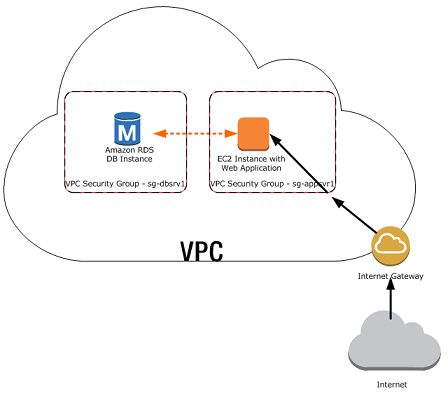
AWS RDS in a VPC
Expected Learning
So what can you expect to learn from this module?
We will begin with understanding a VPC and its benefits. We will see the process to create a VPC and an RDS DB Instance and once they are created how you can connect to the DB Instance via EC2 Instance.
So let’s begin with a brief introduction to VPC.
Virtual Private Cloud (VPC)
VPC or Virtual Private Cloud is nothing but a virtual network in the cloud which is logically isolated. Just think of it as your private Data Centre in the Cloud.
VPC - Benefits
What are the benefits of having a VPC? VPC gives you complete control over your networking power. Thus, you can create as many subnets as you want to. And if you are going to spawn your EC2 instance inside the VPC, you can assign a static private IP address to your EC2 instance. Moreover, you can have multiple IPv4 address in a single EC2 instance by attaching another network interface. In fact, you can attach up to 5 network interfaces to your single EC2 instance. And if you want an extra layer of security, you can go for ACL which is an option in VPC. Finally, VPC supports IPv6. So you can play around with that it in VPC too.
We will now proceed to create a VPC.
Create a VPC
Of course, to create a VPC, the very basic thing you require is access to Amazon Management Console. As a part of creating a VPC, you also need to create Internet Gateways, Route Tables, Public/Private Subnet, and finally Security Groups by which you can allow or block communication to your DB instance.
Demo
Let us now move to the Amazon Management console and create a VPC.
Creating VPC
Once you are logged into your Amazon Console, you will get to see the AWS services dashboard.
Here I will select the region from the menu on the top. I have selected North Virginia; you on the other hand can select any of the regions as per your requirement.
Now filter RDS and you will be redirected to the RDS Dashboard. Here you can create your database instance. But before doing that, you will need to create VPC. Let us search for VPC in the Services. Type VPC and select VPC from the results. You will be taken to the VPC Dashboard.
Click on Your VPCs from the panel on the left, and then click on Create VPC. A popup window will open asking for Name tag.
Enter tetra-vpc as name tag. Define the CIDR Block as 192.168.0.0/16. You can keep the Tenancy as Default, and then click on Yes, Create. Give it a few seconds and you will see that your new VPC has been created.
If you would like to check the details of the vpc, simply select it and the details will appear in the Summary section below.
You VPC ID, VPC name, VPC CIDR, Your main route table and the tenancy are all mentioned here.
Now the next step is to create subnets. From the panel on the left, click on Subnet, and then click on Create Subnet to create a new one. Enter Name Tag as tetra-vpc-priv-sub. Which VPC should this subnet belong to? Let us obviously select the Tetra VPC that we just created. Now set the AZ as 1a, and enter the CIDR Block. The CIDR Block for the VPC was 192.168.0.0/16 so I am going to enter 192.168.1.0/24 as my Private CIDR. And click on Yes, Create. Oops! It’s giving an error for 1a AZ. So I will set the AZ to 1b and then click on Yes, Create. This will take a few seconds.
Once it’s created, you will see it here. So I will create another subnet which will be a public subnet.
Now follow the same steps. Click on Create Subnet to create a new one. Enter name tag as tetra-vpc-pub-sub. Select Tetra VPC as the VPC, set the AZ as 1b, and enter CIDR Block as 192.168.2.0/24. Click on Yes, Create to create the public subnet.
So now here we have two subnets. Let me filter them as tetra – As you can see, one of them is Public while the other one is Private. The subnet mask is 24, also mentioned are the available IPs which is 251, and the AZ is 1b as we configured earlier.
Let us now create the route tables.
From the panel on the left, click on Route Tables. But for the vpc we will need Internet Gateways so that your instance can communicate outwards. So I am going to create one Internet gateway for the vpc. From the panel on the left, click on Internet Gateways, then click on Create Internet Gateway and enter tetra-vpc-igw in the name tag. Then click on Yes, Create. This will create an internet gateway. Once it is created, you can attach it to your tetra VPC. Click on Attach to VPC. Select the vpc from the drop down list and click on Yes, Attach.
Now let us go back to Route Tables. As you can see, there’s already a route table here which is the main route table. So if your subnet is not associated to any route table, it will be associated to this route table by default. Let us add a name to this main route table so that we can identify it easily from the new one we are going to create. Simply click on the Name field and enter tetra-vpc-main-rt and then click the tick mark.
Now click on Create Route Table and enter tetra-vpc-priv-rt in the Name tag. Set the VPC to tetra-vpc. Then click on Yes, Create. It will take some time. Is anyone wondering why I have created one more route table? Remember that we have created two subnets. We will need to associate those two subnets to different route tables as one of them is private Subnet and the other one is the public Subnet and private subnet should not have Public IPs. It should only have private IP’s. I am now selecting our main Route Table; this is where our Public Instance will reside. If we go to the details section of this Route Table, we can see the routes. Click on Routes and then click on Edit as we need to modify the Routes. Now click on Add another route and specify the destination and target. I am entering 0.0.0.0/0 as the Destination and our igw as the target. So this is the route we’re setting for Internet which means if our Instance is associated with this route table, it will have internet access. Now click on Save to save it.
Ok you also need to associate subnet. Select Subnet Associations tab and click on Edit, then select the Public Subnet to associate it with this Route Table. Now click on Save to save it. This will take some time.
When you’re done saving, go to the top section and select the private Route Table from the list. Look at its routes by clicking on Routes tab. As you can see, there’s only one route which is the default one. We will not add any more for now. Now go to Subnet Associations to associate the subnet with this route. Click on Edit and select the private subnet to associate to this route. Now click on Save to save it.
So now there are two subnets - one private and the other public. The Public Subnet is associated with Public Route Table and the Private Subnet with the Private Route Table. The Instance which resides under the Public Subnet will have access to Internet since we attached the Internet Gateway to it.
Now click on Subnets from the panel in the left. As mentioned, here are the two subnets - one public and the other private. But since we’re going to launch our DB instance in a Multi AZ form, we need one more subnet in another AZ. Let us create one more Subnet now.
Follow the same steps as before. Click on Create Subnet. Enter Name tag as tetra-vpc-priv-sub-1c, give Tetra VPC as the VPC, set the AZ as 1c, and enter CIDR Block as 192.168.0.3/24. Now click on Yes, Create. Ok! So this is not a part of the subnet so let me correct it. It should be 192.168.3.0/24. Now click on Yes, Create once again. This will take some time.
Once this is created, you can see three subnets – two private and one public. Let’s make the names more specific. The second private subnet is 1b so I will append 1b here. Since we now have two private subnets in two different AZs we can launch the DB Instance in these two subnets. But we need to create Security Groups for that.
From the panel in the left, click on Security Groups and then click on Create Security Groups. Enter tetra-rds-db-sg in the Name tag, and then enter any description. I will type in; “it contains Security rules for DB Instance”. Then set Tetra VPC as your VPC and then click on Yes, Create.
Now if you want to see the details, you can see the Inbound Rules. Another tab is Outbound Rules. Outbounds are set to ALL Traffic but in the Inbound Rules, you can set your own rules. I will add 3306 to my instance which is associated with this security group. This is how you create inbound rules. Note that if you’re creating your DB instance inside a private subnet, it will not be accessible to outside world and in order to access it, you should have your Instance in the same VPC and it should be attached to this SG so that it can access it.
We have come to the end of this demo. So this was an introductory video on how you can create your VPC.
Demo
Now that we saw how to create a VPC, let us see the steps to create an RDS DB Instance.
Create RDS DB Instance
02-01-AWS_RDS_HA.trec
[00:00:10] to [00:09:26]
Alright! We will get started now. What you see here is the VPC Dashboard. So from here, I will directly go to the RDS Dashboard. From the panel on the left, click on Instances. Then you can go to Launch DB Instance; but before doing that, you should have your database subnet group. Since we don’t have one created already, I will go create one now. From the panel in the left, click on Subnet Groups, and then click on Create DB Subnet Group to create a new one.
Enter Name as tetra-rds-subnet-group, give a description to it and then select the VPC ID which we recently created since we’re going to spawn the DB Instance inside a VPC. So this is the VPC we will spawn in to.
Now moving on, you can select all subnets. As you might remember we had three subnets among which one was public and the other 2 were private.
So I will now switch to the VPC console, click on Subnets and filter the subnets I created using the keyword ‘tetra’. As you can see, these two are private subnets while the other one is the public subnet. Now let us go back to the previous window, here I would like to warn you not to include the public subnet to the database unless you’re going to connect to your database from outside.
Therefore if you’re going to launch your Database Instance, it is recommended you have that DB instance inside the private Subnet only. To do that, we will remove the Public Subnet from the list. So which one is public? Let us go back to the VPC console and find out the id of public subnet. The ID ends with ‘9e18’. So after coming back to the RDS Dashboard I will remove the last subnet group from the list as it is Public subnet. Click on Remove to do this.
Now you’re left with two private subnets that are in different A-Z. Now click on Create; once it is created, the subnet group will be displayed as shown on the screen.
Now, click on Instances and then click on Launch DB Instance. You will be taken to the Engine selection. Select MySQL, and then click on Select. Now you’re taken to the next step which is to select the type of environment. Select MySQL Dev/Test environment since this is for testing purpose. Note that if you’re going for Production Environment, Amazon Aurora is recommended. Now click on Next Step. Here you will specify the DB Details. Under Instance Specifications, MySQL is already set as the DB Engine. As you already know, MySQL is served with a general public license. So select general-public-license in the License Model. Then you can also set the version of Engine according to your code or select the one supported by MySQL. Let us go with the latest version.
Then set the DB Instance Class which is the hardware requirement for your DB Instance. So out of all these specifications, you can select any based on your requirements. For this Demo, I will select db.t2.micro because it will be good for our environment. Here you have to choose whether you need a Multi-AZ Deployment or not. We will set it to YES, as we will test this out for a Multi-AZ Failure. In the next session, we will cover the fail over part.
Now select the Storage Type from the drop down menu. We have three options - General Purpose (SSD), Provisional IOPS (SSD) or Magnetic. For Dev/Test environment, General Purpose (SSD) is fine. For production environment, it’s recommended to choose Provisional IOPS (SSD). Now scroll down to the Settings section. Here the DB instance Identifier is to help you identify your DB instance uniquely. Type in tetra-virginia, and enter the Master Username and Master Password which will be used to log in to the DB you’re creating. I will enter tetra as the Master Username, set a strong Master Password and confirm the entered password before clicking on Next Step.
Here you will find all the network and security related specifications. Select the vpc that we created earlier. The related subnets will be populated automatically under Subnet Group menu. Set the subnet group to tetra-rds-subnet-group. It’s then asking if the DB is publicly accessible or not. Remember that for the production kind of environment it is not recommended for the Database to be publicly accessible. So I will set Publicly Accessible to No. Since we have included our AZ in our subnet group, we need not specify AZ here. So we will leave it as No Preference. Now select the VPC Security Group(s) for the VPC you created. So we will select tetra-rds-db-sg (VPC) here.
Finally coming to the Database Options, enter the Database Name as tetranoodles. As you can see, the default port of MySQL is 3306. Let us keep the default settings here. Now scroll down to Backup. You can set the Backup Retention Period here. You will have a daily backup if you go for automatic backup. So for how many days do you want to reserve your backup? I will go with 7.
The other option is to set a Backup Window. It should be automatic but at what time of the day should it take a backup? The recommended setting is midnight, since it’s a time when there aren’t too many connections to the database. I will go with No Preference.
Moving on to the next section Monitoring, here you can Enable Enhance Monitoring if you want to have a closer look at your database by selecting Yes. I will enable it because I want to know how much IOPS am I consuming, how much Network and memory my Database is consuming. Set the Monitoring Role to Default and Granularity to 60.
And finally, the very last step in the configuration is to set the maintenance window. This lets you select a maintenance window in case a newer version is launched. For the demo, we will leave it with the default settings.
After making sure that you have specified all the information asked for, launch the DB Instance. I will just scroll up to take a quick look and then click on Launch DB Instance. Just relax while it’s being created.
Click on View your DB Instance to see the status. Here you can see the status as creating.
That’s it for this session. We successfully created an RDS DB instance in AWS.
Demo
We first created a VPC and then created an RDS DBS instance inside the VPC. In this demo, we will connect to your private Database Instance via an EC2 Instance.
Connect to DB Instance via EC2 Instance
Alright lets get started now. As you can see, the Database Instance is now up and running. So we will go ahead and connect to it. But remember this DB instance is in VPC and in a private subnet. So you cannot connect to it directly or from outside. So you will need an EC2 instance in the same VPC in which the DB instance resides. So we will create a new Instance EC2 in the same VPC. Click on Services, and under Compute section, go to EC2 to launch a new Instance. Then click on Launch Instance. Here you can choose any of the AMI. Let us go with Ubuntu AMI. Click on Select. This is your Ubuntu AMI. t2.micro is already selected as the Instance type which is fine. Click on Next: Configure Instance Details.
Here you can configure the networking aspects. We will spawn this Instance in the same VPC in which our RDS DB Instance is running. So select network as tetra-rds-vpc, and then set tetra-vpc-pub-sub as the subnet. We’re connecting to a public subnet because we’re going to connect to this instance first and from this instance we will connect to Database Instance. So it should be in public and then the Public IP should be enable so that you can connect to it. Choose Enable for Auto-assign Public IP.
Now click on Next: Add Storage. 8 GB size is good so click on Next: Add Tags. Here you can give the tag, so that you can identify it when there are too many instances. I will name it as public-vm-1. Now click on Next: Configure Security Group. So this is where you can define security policies via security groups. Choose Select an existing security group.
As you already have a previously created public Security group – public-vm-sg, we will select it from the list. Then click on Review and Launch.
Here you can review the entire configuration and when you’re done, click on Launch. A pop up asking to select a key pair will open. You can create a new one if you don’t have it already. But I already have a key pair so I will select it from the drop down menu and then check the box for acknowledgment. Now click on Launch Instance. As you can see the instance is launching. Click on View Instance now and as you can see, our instance is now in pending state and it will take a bit to come up. Go look through your phone while you’re at it.
Okay so now it is up and running as you can see in the Instance State column. So we’re going to connect to it, ensure it is selected and click on Connect. And here you can find the SSH command. So just copy it from here and paste it in MobaXterm. So to connect to an EC2 Instance via SSH, you will need a SSH client. For that you can use PuTTY or MobaXterm.
As I feel comfortable using MobaXterm I will use that. If you want MobaXterm then all you need to do is to search for mobaxterm download in Google. The very first link is the link you need. Go there, and then click on Download now in the Home Edition version. Then in the next page click on MobaXterm Portable Edition. Once you click on this, you will get your MobaXterm in the downloads section. Just double click on it and you’re done.
This how you can download it. So I will now proceed to connecting it to our EC2 Instance.
Let me paste here the SSH Command that I copied earlier and press Enter. Now you’re connected to the EC2 Instance. Once connected, you can go ahead and connect to your DB Instance. But Remember, you’re going to connect to a MySQL Database. So you will require a MySQL Client here.
We will now install a MySQL Client. This is the MySQL client that you will need. Wait! Let me clear the screen so that it’s easily visible to you. So just enter command and press enter. As you can see on the screen, I already have the MySQL client installed. But you will need to install the MySQL client.
To connect to RDS Instance, go to the RDS:AWS Console. Click on DB Instances and make sure that the MySQL DB is selected and click on Instance Actions. From the drop down menu, click on See Details. In the details, look for the End Point, and copy that information. Now go back to the MobaXTerm and type mysql, I will clear the screen to help you see better. Ok so type –h which is your host name and paste your end point there. Sorry let me copy it again. Okay so this is your host name and followed by user, type –u and copy the username from the details section and paste in the MobaXTerm window, followed by –p for the password. Once you’re done with the command, press enter and you will be asked for the password. Enter the password which we declared at the very beginning of the RDS Section. Press enter and you will be connected to your database Instance.
If you want to check your connection, you can type the command show databases followed by a semi colon and you will get your entire database. It’s showing tetranoodledb which we created earlier. To confirm, go to the browser and see the details. Look at the DB Name and you will see tetranoodledb there.
Give the command to use tetranoodledb. Oh it gave an error! Let me see what went wrong. Why would we get an error?
Ok! Because we used a single quotation mark at the end. Remember, that the rule is to write a semicolon at the end of every command.
Let me redo that with a semicolon now. Okay so once you’ve used this database, you can go ahead and give the command show tables;. It will show you the tables in your Database. Since we don’t have any tables created it is showing that the database is empty. We will create the tables some other time.
So that’s all for this session! This video was an introductory video to show how you can create your Database Instance in a private subnet under your custom VPC, and you also learned how you can connect to your private Database Instance via an EC2 Instance. So there was quite a lot to learn. I hope you enjoyed this session.
Summary
With that we have come to the end of this module. To summarize what we learnt – we started with understanding VPC and its benefits. Then we saw the steps in creating a VPC and an RDS DB Instance. Finally, we also saw how we can connect to the DB instance via EC2 instance.
What we have next is ‘Operational Guidelines’. We don’t have a lot of demonstrations in the next module; but we do have some interesting guidelines that we should follow after creating and launching a database instance. Talk to you soon!
Congratulations @niraj456! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPVery Helpful Information. Thanks and keep it up