Digging into a Web Hacker's Mind. Step 2. Scanning
At this stage, web hackers will start getting familiar with their target's technical stack.
Disclaimer: Scanning for vulnerabilities may be illegal. Make sure to obtain a permission from the domain owner before performing a vulnerability scan on it.
Going back to the example of the intelligence agency, let's say we were fortunate enough and could successfully check in a few seconds that acme.com is built with WordPress. This time the statistics were on our side.

Then, the following tools come to the rescue for automated WordPress vulnerability scanning.
| Tool | URL | Type |
|---|---|---|
| WP Scans | https://wpscans.com/ | SaaS |
| WPScan | https://wpscan.org/ | Desktop |
Let the figures guide you again; here are the most common sources of vulnerabilities according to WPScan.
| Percentage | Source of Vulnerability |
|---|---|
| ≈ 50% | Plugins |
| ≈ 40% | Core |
| ≈ 10% | Themes |
A hacker will combine automated scanning with manual scanning for further research. They know the best thing to do in a hurry is to begin analyzing plugins and templates because in a WordPress ecosystem this is the main source of vulnerabilities.
In fact, automated scanning might not even be necessary if probability was on the web hacker's side. A couple of queries to both BuiltWith and the WPScan Vulnerability Database will suffice to bring some light on what to do next.
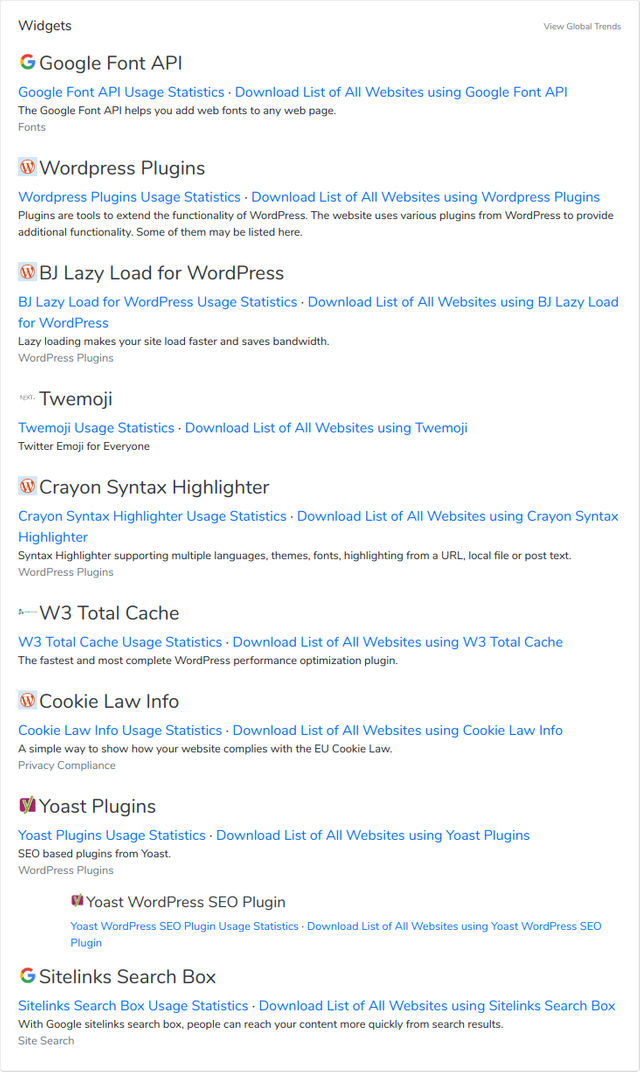
Note: The information above can easily be read in the web site's HTML code -- just browse the site, right click on the document and select View Page Source.
So, this is how the information is gathered when it comes to WP plugins and templates installed on acme.com and analyzed with the help of BuiltWith, WP Scans, and the WPScan vulnerability database.
| Name | Vulnerable (September 2018) |
|---|---|
| BJ Lazy Load for WordPress | No |
| Crayon Syntax Highlighter | No |
| W3 Total Cache | No |
| Cookie Law Info | No |
| Yoast Plugins | No |
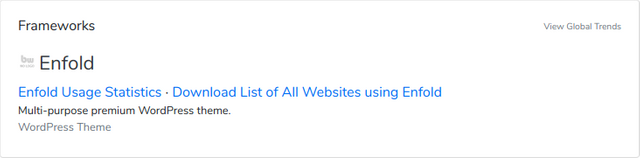
| Name | Vulnerable (September 2018) |
|---|---|
| Enfold | No |
Unfortunately for web hackers, this time everything seems to be okay on acme.com.
Of course, last but not least, apart from the fact that in this example we're analyzing a WP site with a special focus on the CMS, there are a few other potential sources of vulnerabilities to look at: JavaScript libraries, web hosting provider, web server, and so on.
You have been scouted by @promo-mentors. We are a community of new and veteran Steemians and we are always on the look out for promising authors.
I would like to invite you to our discord group https://discord.gg/vDPAFqb.
When you are there send me a message if you get lost! (My Discord name is the same as here on Steemit)