Tor (Onion Router) Basic Explanation how it works
Before to explain how the Tor (Onion Router) works to give you network location anonymity, I just want to talk about where to download it and what to download. You can download Tor at https://torproject.org/ and you need to download Stable Tor Browser for your OS. This is a standalone browser that is configured to use only tor leaving fewer configuration options that allows the Tor software to do its intended function. There’s the common assumption of Tor that it provides the user with absolute anonymity, although Tor does hide the computers and networks the data the users sends and gets while using Tor could still identify them.
The first thing Tor does when opened on your computer, it connects to its directory servers on the Internet. These servers are trusted and redundant and they are set up by the Tor project which lists all of the nodes available in the Tor network. The Tor Proxy on your computer will download this list to build a circuit to use. After downloading the list of available nodes, the Tor Proxy on your computer selects the first Entry Node. After the entry node is chosen it will exchange TLS keys with selected entry node and it will set a secure connection. The goal of this connection is to play as an overarching communication method. Your surfing data is still not moving to the internet after connection to the first Entry Node. The Tor Proxy on your computer sets a node to node key with the Entry Node. The first message Tor proxy sends a create request to the Entry Node. The Entry Node responds with a created respond. At this time a circuit has been set between the Tor Proxy and the Entry Node. The session key has been created specifically for this link.

Once the link between the Tor Proxy on your machine and the Entry Node is completely set then your Tor Proxy sends a message to the entry node with instruction to set a circuit with the Middle Node. The Tor Proxy selects middle node by itself. When the Entry Node gets message from the Tor Proxy, it unwraps it with their agreed-upon session key number 1. Only the Tor Proxy and the Entry Node know about this specific key. The Entry Node reads this message with the instruction to connect a circuit to the selected Middle Node. Then Entry Node sends create a circuit request to the Middle Node and the Middle Node responds with the circuit created to the Entry Node. The Entry Node encrypts this message with the session key number 1 and then sends this message to the Tor Proxy on your computer, so your Tor Proxy knows that the circuit has been extended. Additionally this message has a session key between only the Tor Proxy and the Middle Node. This is the session key number 2.
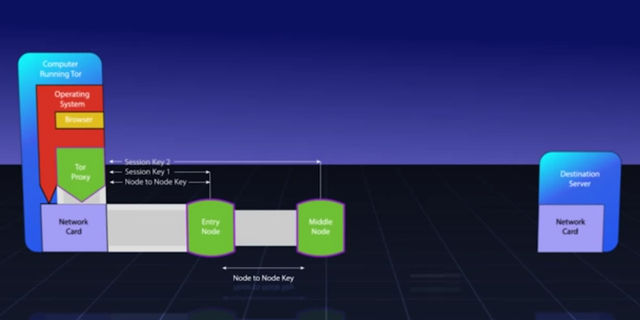
Once communication is set with the Middle Node then the Tor Proxy has to select and set circuit with the third Exit Node. The Tor Proxy sends a relay requests to the Entry Node. The Entry Node unwraps it with the key number 1 and it finds another relay request inside this message. The Entry Node sends this request to the Middle Node, then the Middle Node unwraps this request with the key number 2. The Middle Node finds inside another extend request to the specified Exit Node. The Middle Node extends the circuit to the Exit Node the same way as the Entry Node extended the circuit to the Middle Node. The Exit Node replies through the chain and Tor Proxy gets the session key number 3 between only the Exit Node and the Tor Proxy. Additionally this key number 3 is used to validate the data coming into the Tor Proxy is the same data being sent out of the exit node.
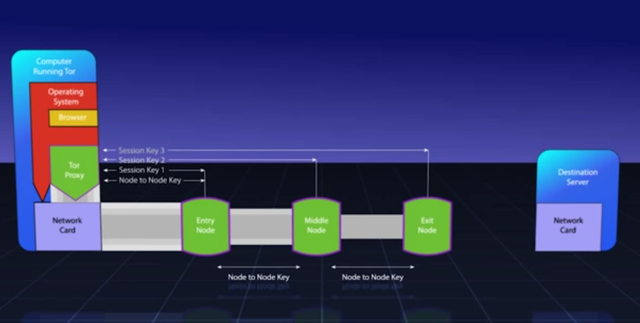
At this point we get a set of tunnels that unwrap like the layers of an onion. The request can be send from the browser to the Tor Proxy then this message will be wrap up in three layers of encryption using three keys, after this encryption is done the message can be send through the three nodes. At this point each node will unwrap one layer of the message. The only Exit Node will see that it has to send message to specific website, but the Exit Node has no clue where this traffic originally came from. You have to keep in mind if you sent unencrypted traffic to the Tor Proxy then this traffic will come out unencrypted from the Exit Node and if someone is listenning between the Exit Node and the Website then this person will obtain your unencrypted message that might potentially identify you, if this message has some personal information.
https://steemit.com/news/@bible.com/6h36cq