How to setup a small Windows Domain in Virtualbox Part 1
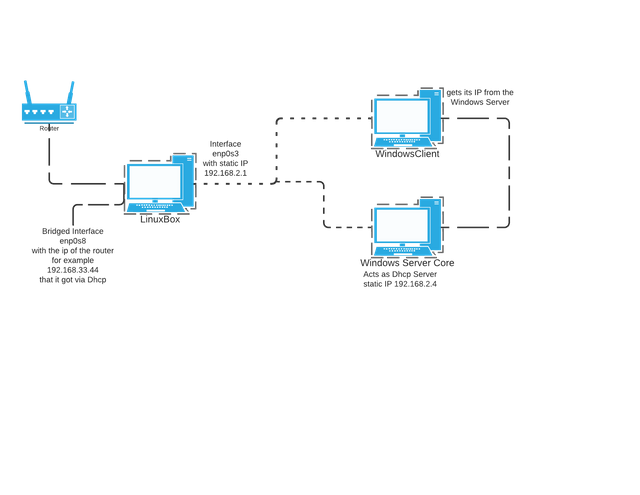
We will setup a small Windows domain with the following virtualboxes:
- 1 debian system that acts as a Nat device
- 1 Windows 10 client
- 1 windows server core with ActiveDirectory and Dhcp enabled
In general it looks like this:
First we‘ll have a look at how we can setup a linux box to work like a so called NAT-device.
Let‘s first answer the question of what a NAT-device is. NAT is an acronym for Network address translation which means that the device is capable of „translating“ IP-addresses that are „behind“ the device to an address that is on the Internet for example. That's a part of what your Router at home does.
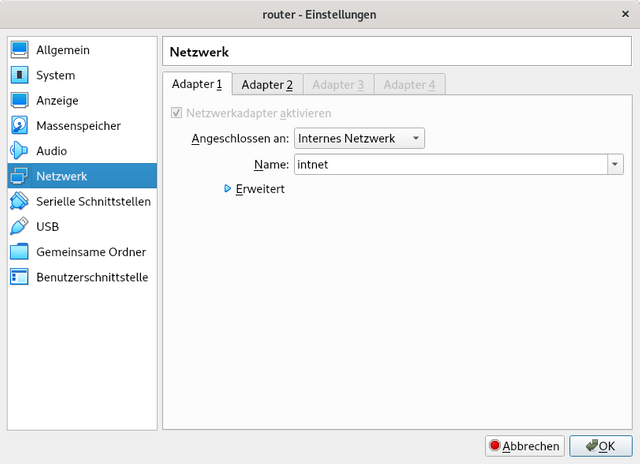
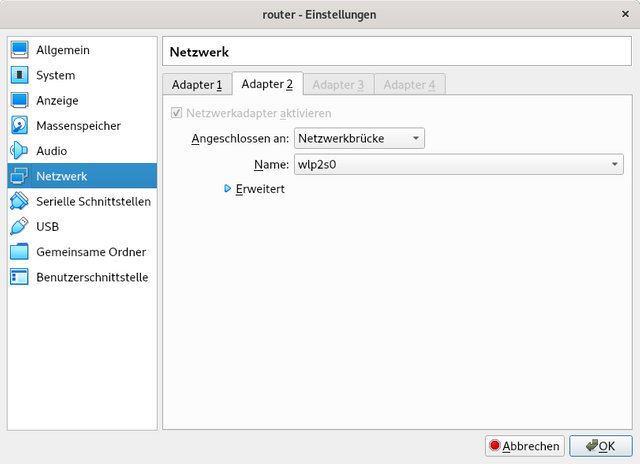
We will setup Debian in Virtualbox with two network adapters. One will be set to internal network and the other one to bridged network as seen below.
Enable IP-forwarding
First IP-Forwarding needs to be enabled which means that packets can be routed from one interface to anothre one. We can do this with the following entry to /etc/sysctl.conf if we want it to persist after reboot:
net.ipv4.forward=1
Changes will take effect after a reboot or if you simply type
sysctl -p
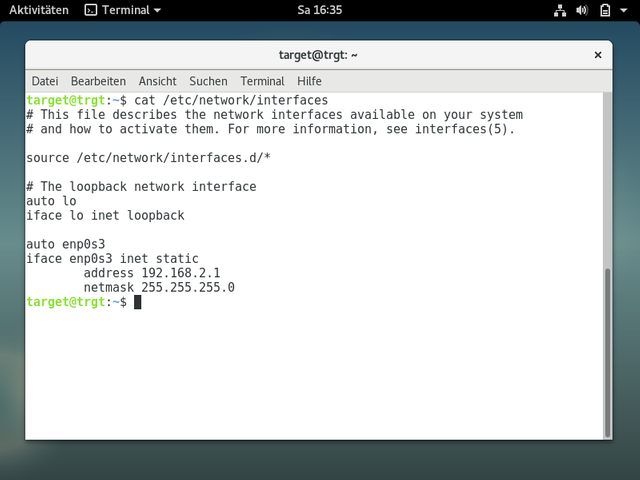
Giving Debian a static IP address
This is quite simple. We could work with the built in ip command but we‘ll define this simply in a file. For this you can edit the file located at /etc/network/interfaces with you favorite editor. Type in the following in the file or uncomment the line in case it is already present in the file.
Now we‘ll type the following to enable the interface:
systemctl restart networking
Iptables
We will use IPTABLES to turn linux into a NAT device. For this we define three rules as seen below:
# iptables -t nat -A POSTROUTING -o enp0s8 -j MASQUERADE
-t – tells iptables which table we want to use(we want to use NAT because Forward is the default table)
-A – here we tell where our rule is applied which is the POSTROUTING chain in our case
-o - this defines the outgoing interface which is enp0s3
-j – here we tell iptables to MASQUERADE the packets on the outgoing Interface enp0s8 which means that packets that come from our Windows Client will get the IP of the router(our debian box)
# iptables -A FORWARD -i enp0s8 -o enp0s3 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A - we want to append the rule to the Forward-chain(in the Filter table which we do not need to specify since its the default table)
-i - this is the incoming Interface
-o – this is the outgoing Interface
-m – tells iptables to match the rule to packets which have the state RELATED and ESTABLISHED which is important since this is the rule for incoming packets
-j – this switch means that packets that come from the ingoing to the outgoing interface will be accepted
# iptables -A FORWARD -i enp0s3 -o enp0s8 -j ACCEPT
-A – again we want to append the rule to the FORWARD-chain
-i – the incoming Interface
-o – the outgoing Interface
-j – again this tells iptables to accept accept the packets as stated in the rule above
So that's it for now! In the next part we'll have a look at Windows Server Core and how we can set it up as a Dhcp Server with Active Directory enabled. Since we'll use the Core Version of Windows Server we will only be able to use Powershell to set the Server up which is kind of interesting.(and which means no clicky clicky)
Sail Safe!
I look forward to your future posts.
How do you determine which interface enp0sx is connected to internal or external network in virtual box?
Happy to hear this!
ip a is a command with which you can see your network interfaces.
If you type ip a when you start the virtual machine and haven't defined a static IP you'll have an IP address from your home router. That's because Virtualbox uses the interface directly without going through your OS.
Congratulations @toalsty! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!