Learn Cryptography #5 - Encryption using Python | "Symmetric" | "Stream Cipher"

Hey Guys!!..
In this tutorial, we will be learning further about "Encryption using Python". We will continue from where we ended in the last tutorial.
Previous tutorials in this "Learn Cryptography" series:
- Learn Cryptography #1 - Hashing vs Encryption
- Learn Cryptography #2 - Hashing using Python
- Learn Cryptography #3 - Hashing using Python - part 2 | "File Integrity Checker "
- Learn Cryptography #4 - Encryption using Python | "Symmetric" | "Block Cipher"
Here, we will cover the Stream cipher which is another type of "Symmetric Encryption".
Introduction
A stream cipher is a method of encrypting text (to produce ciphertext) in which a cryptographic key and algorithm are applied to each binary digit in a data stream, one bit at a time. This method is not much used in modern cryptography. The main alternative method is the block cipher in which a key and algorithm are applied to blocks of data rather than individual bits in a stream.
For more, read Wiki
Applications:
Read this PAPER
Stream cipher is usually used in limited resource
environment, such as cell phones, network stream media,
wireless network and mobile devices and so on.
Advanced Encryption Standard (AES) is an algorithm, successor of DES (discussed in the previous tutorial). It was invented due to the following 2 reasons:
- there was some security problem in DES i.e. attack through brute-force.
- AES is based on a design principle known as a substitution-permutation network, a combination of both substitution and permutation, and is fast in both software and hardware. For more, read this
Features:
- key size - 128-bits (16-bytes), 192-bits (24-bytes) or 256 bits (32-bytes).
- block size - 128 bits
- rounds - 10, 12 or 14 (depending on key size) respectively.
AES has been adopted by the U.S. government and is now used worldwide. It supersedes the Data Encryption Standard (DES), which was published in 1977. The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting and decrypting the data. Source
Here, we will use the AES algorithm (CTR mode) for stream cipher. For more, read AES as A Stream Cipher
As a well-known alternative, by feeding back its
key stream, block cipher could be adopted as a stream cipher.
So in this paper, we use Counter Mode (CTR) AES to make it
as a stream cipher.
Coding
# import the AES library
import pyaes
# Enter plain text of any byte (stream)
i = input("Enter the plain text: ")
# A 256 bit (32 byte) key chosen
key = "abhijit#4387926131r513f124597851"
# CTR mode chosen for stream cipher
aes = pyaes.AESModeOfOperationCTR(str.encode(key))
# cipher text creation
e = aes.encrypt(i)
# or, use this directly
# e = pyaes.AESModeOfOperationCTR(str.encode(key)).encrypt(i)
print("\n The Encrypted text (in bytes): \n", e)
# decrypting cipher text
# The counter mode of operation maintains state, so decryption requires a new instance be created
aes = pyaes.AESModeOfOperationCTR(str.encode(key))
d = aes.decrypt(e)
# or, use this directly
#d = pyaes.AESModeOfOperationCTR(str.encode(key)).decrypt(e)
print("\n The Decrypted text (in bytes): \n", d)
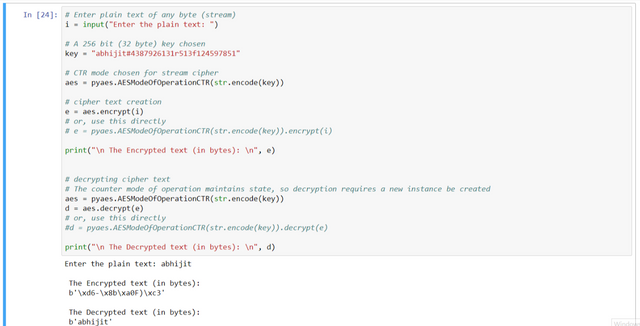
Here, in the example above we give the plaintext "abhijit" & encrypt it and then decrypt. The plaintext can be of any bytes as we are using the AES as a stream cipher in CTR mode.
NOTE: The counter mode aes = pyaes.AESModeOfOperationCTR(str.encode(key)) has to be initialised during encryption & decryption as well.
Yet, we have not used the initial counter value in the CTR mode while creating the AES key for encryption.
We will do that in the following code.
CTR is counter mode. CTR mode was standardized in 2001 by NIST in SP 800-38A. CTR mode uses a counter rather than a traditional IV. The counter has additional properties, including a nonce and initial counter block. The mode does not require padding the plain text to the block size of the cipher.
Code snippet
# Enter plain text of any byte (stream)
i = input("Enter the plain text: ")
# A 256 bit (32 byte) key chosen
key = "abhijit#4387926131r513f124597851"
# To use a custom initial value
counter = pyaes.Counter(initial_value = 100)
# CTR mode chosen for stream cipher
aes = pyaes.AESModeOfOperationCTR(str.encode(key), counter= counter)
# cipher text creation
e = aes.encrypt(i)
# or, use this directly
# e = pyaes.AESModeOfOperationCTR(str.encode(key)).encrypt(i)
print("\n The Encrypted text (in bytes): \n", e)
# decrypting cipher text
# The counter mode of operation maintains state, so decryption requires a new instance be created
counter = pyaes.Counter(initial_value = 100)
aes = pyaes.AESModeOfOperationCTR(str.encode(key), counter= counter)
d = aes.decrypt(e)
# or, use this directly
#d = pyaes.AESModeOfOperationCTR(str.encode(key), counter= counter).decrypt(e)
print("\n The Decrypted text (in bytes): \n", d)
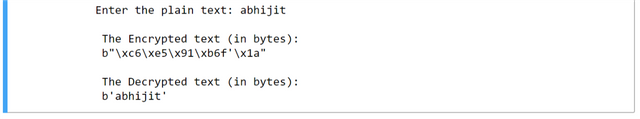
Here, we did the same thing i.e. feeding plaintext and decrypting the encrypted text / ciphertext.
NOTE: The counter value has to be initialised during encryption & decryption as well. i.e.
counter = pyaes.Counter(initial_value = 100)
aes = pyaes.AESModeOfOperationCTR(str.encode(key), counter= counter)
Conclusion
We saw that AES can be used as a stream cipher which is the main purpose of this tutorial.
Following points to be pondered upon:
- AES in CTR mode can be used for stream cipher
- Like IV initialisation vector in block cipher here, we have used the counter value e.g. 100
That's all for now.
Stay tuned for more such tutorials...
Follow this series in Github
Posted on Utopian.io - Rewarding Open Source Contributors
Your contribution cannot be approved because it does not follow the Utopian Rules.
You can contact us on Discord.
[utopian-moderator]
Hello @manishmike10,
FYI, this is Applied Cryptography. Not pure Cryptography.
I have also added the application in quotes.
So, please review once and let me know.