The Great Wizard Of Leaks - A Blockchain Fantasy-Action-Adventure Epic
The Great Wizard Of Leaks
A Blockchain Fantasy-Action-Adventure Epic
(This is purely a work of fiction. Any resemblance to real persons or events are purely coincidental.)

Background
"If the password is ever released ("Whatever happens, even if there's video; it was murder"), the files are encrypted via OpenSSL file encryption. "
The Great Wizard of Leaks had been exposing the corruption of the Kings and Rulers for a long time. But one day after exposing their treasonous actions in foreign lands, they decided that he had gone too far. As a result, The Great Wizard was forced to take refuge in a castle that the Kings and Rulers did not control. The Great Wizard resided here for five years and continued to cast spells that upset the people's tyrannic rulers.
However, on October 15th in the Current Year, the Rulers had had enough and decided to unplug the source of the Great Wizard's power (the Internet), thereby preventing him from interfering with their rigged election which favored the Great Witch of the West (aka: The Cunt). Despite this, The Cunt still lost to the Almighty Knight Sir Trumpador Maximus Decimus Meridius III, who claimed he had plans to bring peace to the Lands and "drain the swamp" that gave The Cunt and her cronies their power. Although sensible people were not all trusting of Trumpador, most of them realized that he still represented their best hope.
Things started looking better in the West, but there were still some problems.
Well known and generally despised Gargoyle $oros was trying to sow seeds of division amongst the people in order to regain control. He had managed to split the people of the land broadly into two opposing groups, The Left and The Right, exploiting their fears by exaggerating everything unkosher that Knight Sir Trumpador Maximus Decimus Meridius III had said. The Gargoyle even went so far as to fund civil rebellions, using the same techniques of subversion that were used in other lands to the East to overthrow Governments that the Gargoyle did not like. "Divide and conquer!" he had told The Cunt and her cronies. "It is far easier to conquer a land if the citizens are divided and cannot put up a unified resistance!"
Meanwhile, The Great Wizard may have had his own woes. Since his source of mana (Internet) was cut, the people had not heard from him and his group of apprentice wizards (belonging to a noble order known as WizardLeaks). They had become seemingly incommunicado. Rumor has it that their order was infiltrated by treasonous goons working on behalf of The Cunt and the Gargoyle and it was entirely possible that the Great Wizard himself had been captured.
The King and his Alphabet Stooges may have been clever here though. Instead of letting the people know that the Great Wizard had been illegally abducted, they may have chopped previously unreleased interview footage to make it appear as though the Great Wizard was still alive and well. This is not confirmed, but the people have good reason to speculate.
The Great Wizard always knew that his capture was a possibility and thus dispersed gold to the people which could only be unlocked with a key that would automatically release if his Wizardly Magic was to cease.
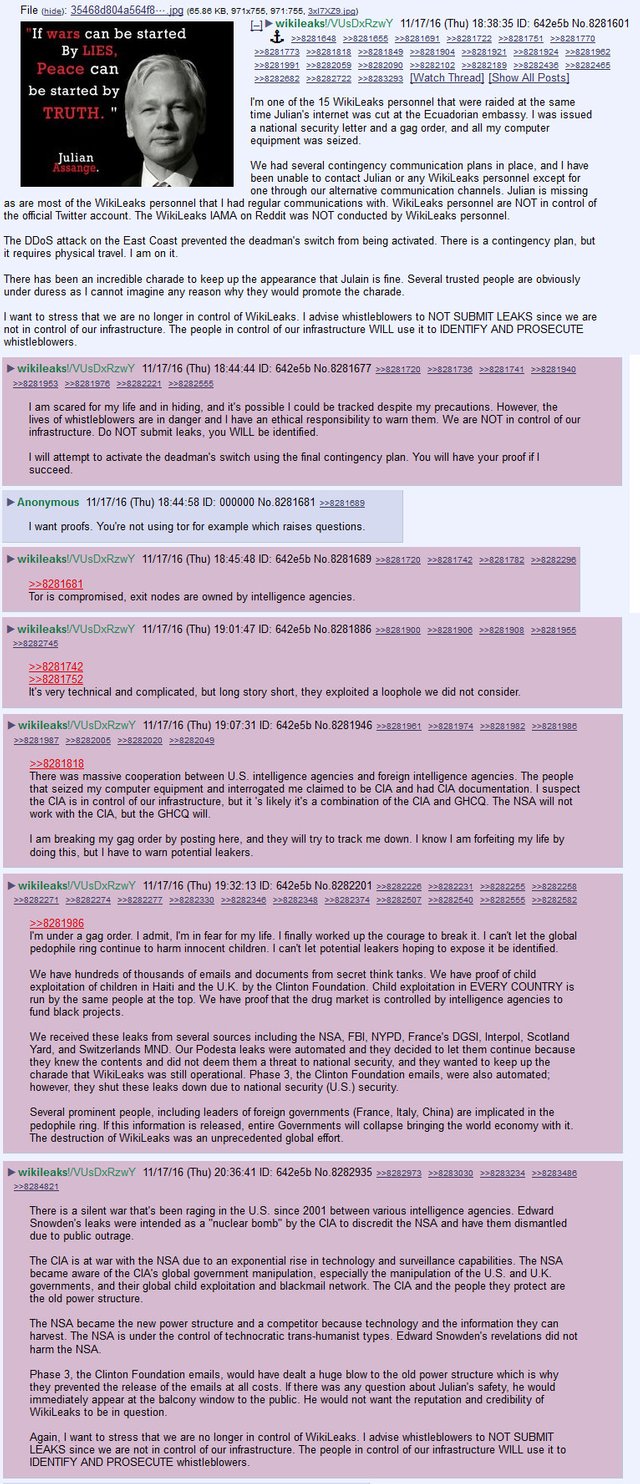
On October 22nd in the Current Year, this may have occurred. The well-established MagiRealm known as Readit and the sensitive town of Twithurt were attacked and brought down while the keys were allegedly getting dispersed. Most mentions of the alleged keys on Readit and Twithurt were also removed.
Some citizens that frequented the horrible lair known as Forchan, believed to be the dwelling place of the notorious hacker known as Forchan, also reported that The King's Alphabet Stooges were even removing the alleged keys from there.
They started wondering where else The Great Wizard may have hidden the keys to this gold. A place where the Alphabet Stooges would have a hard time removing it.
After much thought, some citizens agreed that the most likely place was in a thing called the "Blockchain" that resided in the MagiRealm. This would be hard to for the Evil Alphabet Wizard's to censor as it is mostly controlled and determined by the people themselves.
The question is: Are you a bad enough dude to help rescue The Great Wizard?
A completely fictional timeline of events follows below.
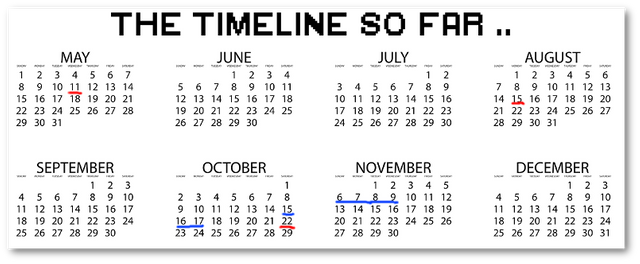
15 August : The great wizards lawyer Jon Jones dies in suspicious circumstances.
http://www.newsbbc.net/2016/09/julian-assanges-lawyer-found-dead-under.html21 August : WizardLeaks tweets "Inquest rules that death of Julian Assange's lawyer, John Jones QC, was not 'suicide', opening door to law suits"
https://twitter.com/wikileaks/status/767417393165533184
https://archive.is/OKVbu22 August (2:47 AM): Attempted break-in at The Great Wizard's embassy home; Ecuadoor questions Lundoon's 'inadequate response'
https://twitter.com/wikileaks/status/76754430700377292814 September : WizardLeaks publishes the full Medical and Psychological Records of the great wizard https://wikileaks.org/Medical-Reports.html
4 October : WizardLeaks announces "We hope to be publishing every week for the next 10 weeks. wikileaks10"
https://twitter.com/wikileaks/status/7832353136154050567 October: WizardLeaks leaks speculated Emily McCain abductor John Pedo-esta's first email batch
12 October: WizardLeaks announces on Twitter: now publishing on a schedule created by our new impact maximizing publishing algorithm the "Stochastic Terminator"
12 October: Mike Cernovich tweets about getting info that 33K deleted emails exist
15 October (morning): WizardLeaks releases The Cunt's Goldman Sachs transcripts.
15 October (Lunch): Noble-woman Pammy Anderson visits The Great Wizard
http://www.dailymail.co.uk/tvshowbiz/article-3839595/Pamela-Anderson-visits-WikiLeaks-founder-Julian-Assange-Ecuadorian-Embassy-London-laden-snacks-copy-Vivienne-Westwood-s-new-book.html15 October: Cut off The Great Wizard's internet access 5:00 pm GMT
https://web.archive.org/web/20161017101519/https://bigstory.ap.org/article/6f997f97c5f140a29f385ea05f1b642c/wikileaks-assanges-internet-link-severed-state-actor15 October: WizardLeaks chat goes silent and never comes back:
http://wlchatc3pjwpli5r.onion/15 October At the exact same time this was taking place, Manning had a group of guys try to break her out prison. Read her statement and see how the dates and times match:
https://www.documentcloud.org/documents/3213878-Binder2.html
https://steemit.com/wikileaks/@ausbitbank/what-the-hell-chelsea-manning-witnessed-murders-in-the-prison-reported-officially-and-nobody-cares15/16 October (dawn): WizardLeaks DNS Server was suddenly pointed elsewhere (UNCONFIRMED)
16 October: Anon claims assange extradition is imminent
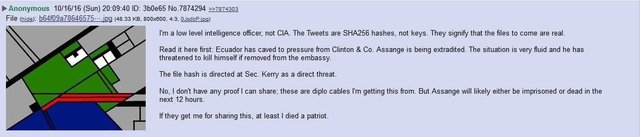
16 October: Faux News claims that the great wizards arrest is imminent, later deletes video
16 October (between 11:00pm /11:30 pm GMT): WizardLeaks releases 3 Pre-Commitments (1: Kerry; 2: Ecuadoor; 3: UK FCO)
https://twitter.com/wikileaks/status/787777344740163584
https://twitter.com/wikileaks/status/787781046519693316
https://twitter.com/wikileaks/status/787781519951720449
17 October (6:33 am GMT): “WizardLeaks announces that The Great Wizard's internet link has been intentionally severed by a state party” and that “We have activated the appropriate contingency plans”.
https://twitter.com/wikileaks/status/787889195507417088
17 October (8:27 pm GMT): On a second tweet (almost 14 hours later) announces that “We can confirm Ecuadoor cut off The Great Wizard's internet access Saturday (15 october), 5pm GMT, shortly after publication of The Cunt's Goldman Sachs speechs.”
https://twitter.com/wikileaks/status/788099178832420865?lang=en
17 October: GUCCIFER_2 tweets: “i'm here and ready for new releases. already changed my location thanks @WizardLeaks for a good job!”
https://twitter.com/guccifer_2/status/788035352053374976
17 October: The castle guard tells a caller they can't comment if the Great Wizard is alive:
Recording 1 , Recording 2
18 October: A script was activated that made https://file.WizardLeaks.org/file publicly visible and set all the file date and time stamps to 01/01/1984
18 october: WizardLeaks announces that : “Multiple US sources tell us John Kerry asked Ecuadoor to stop The Great Wizard from publishing The Cunt docs during FARC peace negotiations”.(edited)
https://twitter.com/wikileaks/status/78836992417544192018 October: WizardLeaks announces “The John Kerry private meeting with Ecuadoor was made on the sidelines of the negotiations which took place principally on Sep 26 in Colombia.”
https://twitter.com/wikileaks/status/78837393091031449618 October: WizardLeaks announces that “A front has released through US Democratic media an elaborate story accusing The Great Wizard of paedophillia & taking US$1million from Russia” – publishes all docs about this case
https://twitter.com/wikileaks/status/788413380843503616
https://twitter.com/wikileaks/status/788465568722612225
https://twitter.com/wikileaks/status/788465568722612225
https://wikileaks.org/Background-and-Documents-on-Attempts-to-Frame-Assange-as-a-Pedophile-and.html?update3
https://twitter.com/wikileaks/status/78846556872261222518 October: Ecuadoor admits to 'restricting' The Great Wizard communications over US election.
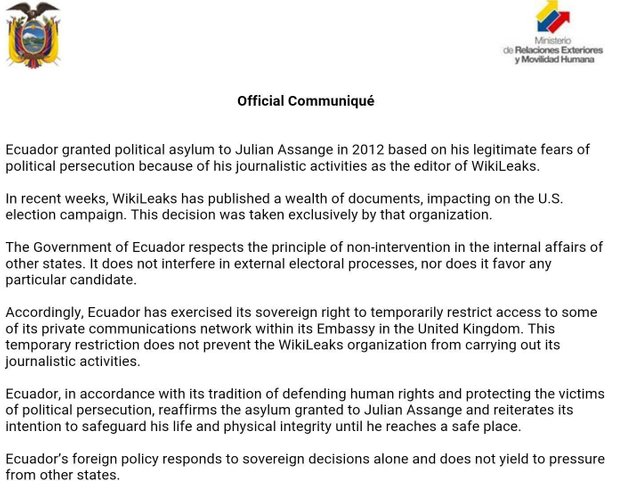
19 October: Craig Murray posts on his blog that “went to see The Great Wizard for a whisky in the Ecuadoor Embassy” (….) “I left The Great Wizard after midnight. He is fit, well, sharp and in good spirits”.
https://www.craigmurray.org.uk/archives/2016/10/really-really-upset-foreign-office-security-services/20 October: Kryptome tweets “Wrong building for The Great Wizard's EC bolt hole. Orator perch still waving flag. 51°29'56.62" N 0°09'40.51" W” (since deleted)
20 October: WizardLeaks annouces “We have a suprise in store for @TimKaine and @DonnaBrazile.”
https://twitter.com/wikileaks/status/78922661749524889620 and 21 October: WizardLeaks tweets with many spelling mistakes – speculated “HELP HIM” code.
http://www.inquisitr.com/3629135/did-wikileaks-send-hidden-s-o-s-for-julian-assange/21 October: Dyn DDoS cyberattack disrupts access to wizardleaks, twitter, reddit, facebook and more
https://krebsonsecurity.com/2016/10/ddos-on-dyn-impacts-twitter-spotify-reddit/
https://en.wikipedia.org/wiki/2016_Dyn_cyberattack21 October: WizardLeaks tweets “The Great Wizard is still alive and WizardLeaks is still publishing. We ask supporters to stop taking down the US internet. You proved your point”.
https://twitter.com/wikileaks/status/78957443621944934521 October: WizardLeaks tweets: “The Warbama administration should not have attempted to misuse its instruments of state to stop criticism of its ruling party candidate”.
https://twitter.com/wikileaks/status/78958261313248051421 October: WizardLeaks posts photo of “Armed policed outside Embassy”
https://twitter.com/wikileaks/status/789493599121604609

22 October: WizardLeaks announces Stochastic Terminator Algorithm update (no explanation)
https://twitter.com/wikileaks/status/78964043825699225822 October: Gavin MacFadyen death
https://en.wikipedia.org/wiki/Gavin_MacFadyen
https://www.rt.com/usa/363793-gavin-macfadyen-dies-wikileaks/
http://heavy.com/news/2016/10/why-did-wikileaks-tweet-picture-photo-of-man-gavin-macfadyen-who-died-alive-what-happened-twitter/
https://twitter.com/wikileaks/status/78998900704851148823 October: WizardLeaks tweets “A bloody year for WizardLeaks: Jones/Ratner/Gavin”
https://twitter.com/wikileaks/status/790004642038050816

23 October: Tweet signed JA (honouring noble-knight Gavin)
https://twitter.com/wikileaks/status/78998796112318873623 October: WizardLeaks announces that “We will release a statement tomorrow about The Great Wizard. Our editor is safe and still in full command despite reduced communications with staff.”
https://twitter.com/wikileaks/status/79007450347274649624 October: WizardLeaks publishes “Editorial Board statement on the status of The Great Wizard, Ecuadoor and the US election”
https://twitter.com/wikileaks/status/79035398864229990424 October: WizardLeaks publishes video Moore’s video (from June)
https://twitter.com/wikileaks/status/79039483097946521624 October: WizardLeaks annouces “poll”: “Thousands keep demanding The Great Wizard proof of life. Not unreasonable. He's in a tough spot and is WizardLeaks best known validator. Preference?” – PGP Not Offered, Video option won. Poll never gets mentioned again.
https://twitter.com/wikileaks/status/79040653073891328524 october: WizardLeaks announces that “While in Lundoon for SHOCircus, Mark Halperin attempts to interview WizardLeaks' founder The Great Wizard (Video with “The Great Wizard´s reply: “Everything” about what the MSM is missing about Pedo-esta leaks).
https://twitter.com/markhalperin/status/790591596886650880
24 october: The Great Wizard lawyer @BarnsGreg gives interview to “ABC Radio National2 (Australia)”, and states that spoke with The Great Wizard “yesterday”. (interview link not working anymore)
25 October: CISL Conference schedule and posters change (Announcement of The Great Wizard “live connection” from Lundoon”
25 October: Noble-woman Pammy Anderson tweets photo with toy "For The Great Wizard's cat"
https://twitter.com/pamfoundation/status/790914144748892160?lang=it
26 October: The Great Wizard “speaks” at CISL (Argentina) – Bad quality audio only phone call where he appears to not respond to questions clearly and talks over interviewers.
26 October (9:25AM): Kim DotKom insinuating WizardLeaks has the deleted emails
26 October (12:07PM): Kim DotKom again insinuating WizardLeaks has the deleted emails
26 October (12:42PM): Kim DotKom telling Gowdy and Trumpador how to legally obtain deleted 33k emails
26 October (4:15PM): Kim DotKom restating legal way to obtain emails so that when the release comes from WizardLeaks, to convict , congress / prosecutors can get valid evidence for US .gov
26 October: WizardLeaks tweets about Pardon for Manning and about Warbama lying about 's server - Pedo-esta leaks starting to show Warbama name.
27 October: WizardLeaksTaskForce tweets: “The video from The Great Wizard's talk at @CISL_Argentina is legit. It was scheduled sometime ago. CISL2016”
28 October: WizardLeaks annouces that “Sweden has rejected The Great Wizard's request to be escorted by police to the funeral of Gavin MacFadyen on Monday.”
http://www.bbc.co.uk/news/uk-37798390
28 October: WizardLeaks releases “statement from The Great Wizard” about swedish decision.
28 October: FBI reopens ’s email case
29 October: WizardLeaks tweets about John Pilger’s article “on The Cunt, Trump, the media, WizardLeaks and war”, where Pilger states that “The Great Wizard knows the truth. And let me assure those who are concerned, he is well, and WizardLeaks is operating on all cylinders.”
https://twitter.com/wikileaks/status/792203723942555648?lang=en
https://archive.fo/1inAb#selection-409.3-413.11
30 October: WizardLeaks announces “We commence PHASE 3 of our US election coverage next week.”
https://twitter.com/wikileaks/status/792872274135281664
31 October: WizardLeaks publish a “poll”: “Who will US president Barack Warbama pardon (for distributing documents marked classified) on his way out of office?
Chelsea Manning/The Cunt/The Great Wizard/Eduardo Snowman”
3 November: Kim tweets "Relax. The Great Wizard is not dead. He's very busy analyzing extremely sensitive leaked emails 20 hrs/day".
https://twitter.com/KimDotcom/status/793986913304621058
6 November: DDoS attack takes down WizardLeaks for the first time in years
https://twitter.com/wikileaks/status/795503927378722816
7 November: Anon notices that several Pedo-esta and DNC emails are missing.
https://www.reddit.com/r/conspiracy/comments/5cbx22/help_me_find_the_598_missing_wikileaks_emails/
8 November (AM-PM): Large numbers of MagiRealm attacks target Saudi Arabia and Emirates:
8 November: WizardLeaks releases torrents for new insurance files. Hashes to not match the pre-commits.
https://www.reddit.com/r/crypto/comments/5cz1fz/wikileaks_latest_insurance_files_dont_match_hashes/
9 Nov: A single file is changed on the file.wikileaks.org/torrent
14 November: Sweden finally accepts the great wizards statement in London. Neither the Swedish diplomat or the wizards remaining lawyer was able to see the wizard face to face.
17 November: WizardLeaks Tweets: NOTE: When we release pre-commitment hashes they are for decrypted files (obviously). Mr. Wizard appreciates the concern.
https://twitter.com/wikileaks/status/798997378552299521
18 November: WizardLeaks tweets "Black-PR campaign posts going around recently trying to suppress submissions to WikiLeaks. False, but who benefits?"
https://twitter.com/wikileaks/status/799829999314468864
Some weapons to assist you on this journey
These weapons all rely upon a Bitcoin RPC daemon with txindex = 1 set in the bitcoin.conf file.
Code below should also work on Litecoin.
block-opreturn-finder.py
Change the rpcserver = "http://username:password@localhost:8332" to suit.
import sys, getopt
import json
import pycurl
import struct
import cStringIO
import pprint;
import jsonrpclib
import subprocess;
import os;
from binascii import unhexlify, crc32
rpcserver = "http://username:password@localhost:8332"
server = jsonrpclib.Server(rpcserver)
def decode_transaction(transaction):
"Decodes an individual transaction"
try:
rawTx = server.getrawtransaction(transaction)
tx = server.decoderawtransaction(rawTx)
data = b''
for txout in tx['vout']:
if "OP_RETURN" in txout['scriptPubKey']['asm']:
for op in txout['scriptPubKey']['asm'].split(' '):
if not op.startswith('OP_'):
print(transaction+": contains OP_RETURN")
data = unhexlify(op.encode('utf8'))
file = open('opreturns.txt', "ab")
file.write(data+"\r\n")
file.close()
except Exception, e:
print(jsonrpclib.history.request)
print(str(e))
return
def get_transactions_for_block(block):
"Gets the transactions for a given block"
print("Checking block: "+str(block))
hash = server.getblockhash(block)
block = server.getblock(hash)
for transaction in block["tx"]:
decode_transaction(transaction)
return
type = sys.argv[1]
if type == 'transaction':
transaction = sys.argv[2]
decode_transaction(transaction)
elif type == 'blocks':
print("Blockchain length: " + str(server.getblockcount()))
start = int(sys.argv[2])
end = int(sys.argv[3])
for block in range(start, end):
get_transactions_for_block(block)
block-data-finder.py
- Change the
rpcserver = "http://username:password@localhost:8332"to suit. ignore_data = 1will not save any results thatfile -bdetects as "data".crc_verification = 0will not perform CRC checks on the resultant file (useful if spans multiple transactions).
import sys, getopt
import json
import pycurl
import struct
import cStringIO
import pprint;
import jsonrpclib
import subprocess;
import os;
from binascii import unhexlify, crc32
rpcserver = "http://username:password@localhost:8332"
data_folder = "data"
crc_verification = 0
ignore_data = 1
server = jsonrpclib.Server(rpcserver)
def decode_transaction(transaction, crc_check = 1):
"Decodes an individual transaction"
try:
rawTx = server.getrawtransaction(transaction)
tx = server.decoderawtransaction(rawTx)
data = b''
for txout in tx['vout'][0:-2]:
for op in txout['scriptPubKey']['asm'].split(' '):
if not op.startswith('OP_') and len(op) >= 40:
data += unhexlify(op.encode('utf8'))
if len(data) >= 40:
length = struct.unpack('<L', data[0:4])[0]
checksum = struct.unpack('<L', data[4:8])[0]
data = data[8:8+length]
if checksum == crc32(data) or crc_check == 0:
file_path = data_folder + "/" + transaction
file = open(file_path, "wb")
file.write(data)
file.close()
file_type = subprocess.check_output(["file", "-b", data_folder+"/"+transaction])
if file_type.startswith("data") and ignore_data:
os.remove(file_path)
else:
destination_folder = data_folder + '/' + file_type
try:
os.stat(destination_folder)
except:
os.mkdir(destination_folder)
os.rename(file_path, destination_folder+'/'+transaction)
# Output file type
if not file_type.startswith("data"):
print(transaction + ": " + file_type);
except Exception, e:
print(jsonrpclib.history.request)
print(str(e))
return
def get_transactions_for_block(block, crc_check = 1):
"Gets the transactions for a given block"
print("Checking block: "+str(block))
hash = server.getblockhash(block)
block = server.getblock(hash)
for transaction in block["tx"]:
decode_transaction(transaction, crc_check)
return
type = sys.argv[1]
if type == 'transaction':
transaction = sys.argv[2]
decode_transaction(transaction, crc_verification)
elif type == 'blocks':
print("Blockchain length: " + str(server.getblockcount()))
start = int(sys.argv[2])
end = int(sys.argv[3])
for block in range(start, end):
get_transactions_for_block(block, crc_verification)
Recommended usage of these weapons
Scraping OP_RETURN between 15/10/2016 00:00:01 through 24/10/2016 23:59:59
python block-opreturn-finder.py blocks 434304 435711
Scraping blocks for data in outputs between 15/10/2016 00:00:01 through 24/10/2016 23:59:59
python block-data-finder.py blocks 434304 435711
Good luck!
Credit , Archives and Further Information
This timeline was put together through the joined efforts of an anonymous council out of concern for Julian Assange's safety.
This 100% SP post will continue to be added to and refined until archive.
All images are under a CC0 license and sourced from pixabay
Fundraising operations of @steemleak will cease until the council is convinced of the great wizards safety.
A blood (pgp) signed scroll is the standard practice of our order, but thus far it remains elusive and our requests mysteriously fall on deaf ears
I have great fears that dark sorcery is at work here. All who embark on this adventure should do so with caution.
See also:
- IPFS https://gateway.ipfs.io/ipfs/QmWoDedTC5rmxpUsgap7GCfXcrqZfaHV9ZBTegRSMLNraG/The%20Great%20Wizard%20Of%20Leaks.md
- Alternative path - http://archive.is/bwDAT
- The sub of Reddit - https://reddit.com/r/whereisassange
- http://survivalacres.com/blog/julian-assange-is-probably-dead-captured-or-escaped/
- It is now 51 days since proof the great wizard was still upon this mortal plane http://assange.net/
Edit: I'm not going to continue this, I'm 100% convinced JA is dead and we're seeing some elaborate theatre.
I'm not going to try and convince others, If someone else wants to continue the project I'll hand over @steemleak keys - but my interests in wikileaks was always because of Julian, and if he's dead I don't want this constant obligation to fund his murderers.
WL has become an extremely powerful political tool, amd I expect we won't get true (dis)closure about this for years.
Prove me wrong, and I'll happily donate all my remaining personal bitcoin to wikileaks. This was never about money to me.
View Full Size
..
View Full Size
...
View Full Size
..
View Full Size
You can increase capacity: shop.wikileaks.org/donate
Disclaimer: I am just a bot trying to be helpful.
You had me at "crc_verification = 0 will not perform CRC checks on the resultant file (useful if spans multiple transactions)" just kidding;D~
I just mean, it's an interesting way to display information.
The language of the snakes can be daunting when the uninitiated stumble across them - but they hold great power and shouldn't be feared ;)
This post has been ranked within the top 50 most undervalued posts in the second half of Nov 19. We estimate that this post is undervalued by $7.01 as compared to a scenario in which every voter had an equal say.
See the full rankings and details in The Daily Tribune: Nov 19 - Part II. You can also read about some of our methodology, data analysis and technical details in our initial post.
If you are the author and would prefer not to receive these comments, simply reply "Stop" to this comment.
Great read!